Network Segmentation of Biomedical Devices Review
© 2022 Akilnath Bodipudi, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Abstract
This review delves into the critical role of network segmentation in securing biomedical devices within healthcare organizations. It highlights the importance of isolating these devices to protect against cyber threats and ensure compliance with industry regulations. The review examines the unique challenges posed by biomedical devices, such as their inherent vulnerabilities and integration with legacy systems. It outlines strategic approaches and advanced technologies for effective segmentation, providing a comprehensive analysis of best practices. By implementing robust network segmentation, healthcare organizations can enhance their cybersecurity posture, safeguard sensitive patient data, and maintain the integrity of essential medical services
Introduction
Importance of Cybersecurity in Healthcare
The healthcare sector is a prime target for cyberattacks due to the high value of patient data and the critical nature of medical services, necessitating robust cybersecurity measures to protect sensitive information and maintain operational continuity. Biomedical devices, essential for patient care by monitoring vital signs and administering treatments, are increasingly integrated into hospital networks, making them crucial to healthcare but also vulnerable to cyber threats. Network segmentation, which involves dividing a network into smaller, isolated segments, enhances security and performance by isolating biomedical devices from other network traffic, thereby preventing the spread of cyber threats across the network.
Challenges in Securing Biomedical Devices
Securing biomedical devices within healthcare environments presents a unique set of challenges that stem from their inherent vulnerabilities, regulatory requirements, and the complexities of integration with existing systems. These challenges must be addressed to protect patient data, ensure the reliable operation of medical equipment, and comply with legal standards [1-3].
Unique Vulnerabilities of Biomedical Devices
Biomedical devices are primarily designed with an emphasis on functionality and patient safety, often at the expense of security. This focus results in several inherent vulnerabilities:
Outdated Software: Many biomedical devices operate on legacy operating systems and software that are no longer supported or updated by vendors, making them vulnerable to known exploits.
Limited Security Features: These devices frequently lack essential security features like encryption, secure boot, and advanced authentication mechanisms, making them susceptible to cyber-attacks.
Direct Internet Connectivity: Some devices are directly connected to the internet without adequate protection, exposing them to external threats.
Lack of Standardization: The variety of devices from different manufacturers, each with unique software versions and configurations, creates a fragmented and challenging security landscape.
Regulatory and Compliance Requirements
Healthcare organizations must adhere to various regulations and standards designed to protect patient data and ensure the safety and efficacy of medical devices. Key regulatory challenges include: HIPAA Compliance: The Health Insurance Portability and Accountability Act (HIPAA) mandates stringent protection of patient health information. Biomedical devices that store or transmit patient data must comply with these requirements.
IEC 80001 Standard: This standard emphasizes the risk management of IT networks incorporating medical devices, requiring healthcare organizations to manage the risks associated with connecting medical devices to their networks.
FDA Guidelines: The U.S. Food and Drug Administration (FDA) provides guidelines for the cybersecurity of medical devices, necessitating manufacturers to address security risks throughout the device lifecycle.
Integration with Legacy Systems
Many healthcare facilities depend on legacy systems and infrastructure not designed with modern cybersecurity needs in mind, leading to several challenges:
Compatibility Issues: Ensuring that new security measures and protocols are compatible with older systems can be challenging, often requiring customized solutions or workarounds.
Operational Disruption: Implementing security upgrades and network segmentation must be done carefully to avoid disrupting critical healthcare services and device functionality.
Resource Constraints: Healthcare organizations often operate with limited IT resources and budgets, making it difficult to invest in necessary upgrades and ongoing maintenance for legacy systems.
Operational and Organizational Challenges
In addition to technical and regulatory issues, there are operational and organizational challenges that complicate the security of biomedical devices:
Lack of Security Awareness: Staff who operate and manage biomedical devices may lack sufficient training in cybersecurity best practices, leading to unintentional security lapses.
Interdisciplinary Coordination: Effective security requires coordination between various departments, including IT, clinical engineering, and healthcare providers. Miscommunication or lack of collaboration can hinder security efforts.
Vendor Management: Relying on multiple vendors for different devices can complicate security management, especially when vendors have varying levels of commitment to cybersecurity.
Securing biomedical devices is a challenging yet essential responsibility for healthcare organizations. It involves addressing the specific vulnerabilities of these devices, meeting regulatory standards, integrating with legacy systems, and managing operational challenges. These steps are crucial for protecting patient data and ensuring the safe and reliable functioning of medical equipment. By recognizing and addressing these challenges, healthcare providers can strengthen their cybersecurity measures and protect their vital assets.
Network Segmentation Overview
Definition and Benefits of Network Segmentation
Network segmentation involves partitioning a network into smaller, distinct segments, each managed by its own set of security controls. This practice is crucial for bolstering network security, especially in complex environments like healthcare, where numerous devices and systems operate simultaneously. By isolating biomedical devices from other network segments, network segmentation significantly curtails the spread of cyber threats. For example, if a cyber-attacker breaches one segment, they cannot easily access others. Additionally, segmentation enhances overall network performance by reducing congestion, as network traffic can be managed and optimized more effectively within smaller segments [4, 5].
Key benefits of network segmentation include:
Enhanced Security: Restricts the lateral movement of threats within the network.
Improved Performance: Reduces network congestion, improving data transfer speeds and reliability.
Regulatory Compliance: Aids in meeting industry standards and regulatory requirements by segregating sensitive data.
Simplified Management: Makes network management and troubleshooting easier by localizing issues within specific segments.
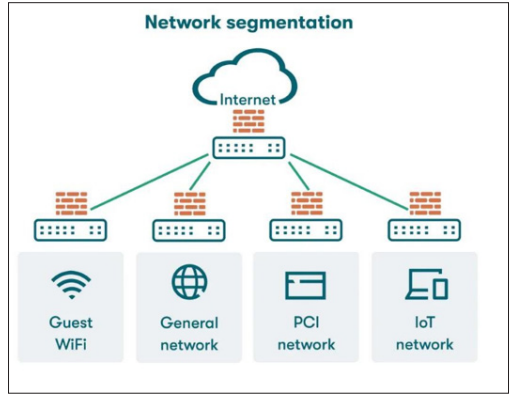
Figure 1: Overview of Network Segmentation Types of Network Segmentation
Network segmentation can be implemented through various methods, each offering unique advantages and applications:
VLANs (Virtual Local Area Networks): VLANs enable logical separation of devices within the same physical network. By assigning devices to different VLANs, organizations can control and restrict communication between segments. VLANs are flexible and cost-effective, allowing efficient use of existing network infrastructure.
Subnets: This method divides the network into smaller IP- based segments, each with its own IP range. Subnetting enhances security by isolating groups of devices at the network layer and can be used in conjunction with VLANs to provide an additional layer of security.
Physical Separation: This approach uses different physical network infrastructures for different segments. Although it offers the highest level of isolation and security, it is also the most expensive and complex to implement and manage. Physical separation is typically used for highly sensitive systems requiring maximum security.
Case Studies of Network Segmentation in Healthcare
Real-world examples provide valuable insights into the practical application of network segmentation in healthcare settings. These case studies highlight the benefits and challenges associated with different segmentation approaches:
Case Study 1: Large Hospital Network Using VLANs
A large hospital implemented VLANs to segment biomedical devices from other network traffic. Each department, such as radiology and cardiology, was assigned its own VLAN. This logical separation enhanced security by ensuring that devices in one department could not communicate directly with those in another. Additionally, VLANs improved network performance by reducing broadcast traffic and congestion.
Case Study 2: Subnetting for Enhanced Security in a Medical Center
A medical center employed subnetting to isolate its biomedical devices. Each type of device, such as infusion pumps and patient monitors, was assigned a specific subnet. This IP-based segmentation not only bolstered security but also simplified network management, as administrators could apply targeted security policies and monitor traffic more effectively.
Case Study 3: Physical Separation in a Research Hospital
A research hospital with highly sensitive data opted for physical separation to secure its biomedical devices. Separate network infrastructures were established for research, clinical, and administrative operations. This approach provided the highest level of security but required significant investment in infrastructure and maintenance.
These case studies illustrate that while the specific method of segmentation may vary, the primary objective remains consistent: to enhance the security and performance of networked biomedical devices, ensuring reliable and safe healthcare delivery. Each approach comes with its own set of challenges and considerations, such as cost, complexity, and maintenance requirements, which must be carefully evaluated against the organization’s security needs and resources.
Assessment and Inventory Management
Effective network segmentation for biomedical devices begins with a thorough assessment and inventory management process. This foundational step ensures that all devices are accounted for, evaluated, and appropriately prioritized for protection. The following sections outline the critical components of this process [6, 7].
Conducting a Comprehensive Inventory of Biomedical Devices A detailed and comprehensive inventory of all network- connected biomedical devices is crucial. This step involves cataloging every device, including its make, model, software version, network connectivity details, and any other relevant information. By having a complete inventory, healthcare organizations can:
Identify Devices Needing Protection: Knowing the exact devices that are connected to the network helps in understanding which ones need to be secured.
Ensure No Device is Overlooked: A meticulous inventory process ensures that all devices, even those that are less obvious or infrequently used, are accounted for in the segmentation strategy.
Support Effective Management: Maintaining an up-to-date inventory facilitates better management and monitoring of biomedical devices, aiding in timely updates and maintenance.
Assessing Network Architecture and Current Segmentation Evaluating the existing network architecture is the next critical step. This involves:
Reviewing Current Setup: Understanding how the current network is configured, including existing segmentation (if any), helps in identifying potential vulnerabilities and areas that need improvement.
Identifying Gaps: By mapping out the current network, healthcare organizations can pinpoint weaknesses or gaps in the existing setup that could be exploited by cyber threats.
Establishing a Baseline: This assessment provides a baseline from which to develop a more effective segmentation strategy.
It highlights what is already working well and what needs to be changed or enhanced.
Identifying Vulnerabilities and Risk Analysis
Once the inventory and network assessment are complete, the next step is to identify vulnerabilities and conduct a risk analysis:
Identifying Security Vulnerabilities: This involves examining each biomedical device and the network as a whole to find weaknesses that could be targeted by cyber threats. Common vulnerabilities might include outdated software, default passwords, and unsecured communication channels.
Conducting Risk Assessments: Risk assessments help prioritize security efforts by determining which devices and systems are most critical and which are most vulnerable. Factors considered in this analysis include the device’s role in patient care, the sensitivity of the data it handles, and its exposure to potential threats.
Prioritizing Protection Efforts: By understanding the risks associated with each device, healthcare organizations can ensure that the most critical and vulnerable devices receive the highest level of protection. This targeted approach helps in allocating resources efficiently and effectively.
The assessment and inventory management phase is a vital part of implementing network segmentation for biomedical devices. Conducting a comprehensive inventory ensures all devices are identified and accounted for, while assessing the current network architecture helps to understand existing strengths and weaknesses. Identifying vulnerabilities and conducting risk analyses ensure that the most critical devices receive prioritized protection. These steps lay the groundwork for a robust and effective network segmentation strategy that enhances the cybersecurity posture of healthcare organizations.
Defining Segmentation Strategy
In the realm of securing biomedical devices within healthcare networks, establishing a coherent segmentation strategy is essential for effectively managing and reducing cybersecurity risks. This section focuses on defining segmentation objectives, creating network divisions based on risk evaluations, and implementing necessary access controls and technologies [8, 9].
Establishing Segmentation Objectives
The initial step in crafting a segmentation strategy is to define precise and specific objectives. These objectives should align with the broader cybersecurity goals of the healthcare organization. Key aims typically encompass:
Isolation of High-Risk Devices: Identifying and isolating biomedical devices at high risk of cybersecurity threats, often due to outdated software or their critical role in patient care.
Compliance with Regulatory Standards: Ensuring that segmentation practices adhere to relevant healthcare regulations (e.g., HIPAA, GDPR, IEC 80001) governing patient data protection and medical device security.
These objectives serve as the groundwork for designing network segmentation that not only bolsters security but also supports operational efficiency and regulatory conformity.
Creating Network Zones Based on Risk Assessment Network segmentation involves partitioning the healthcare network into distinct zones or segments based on the risk profiles of interconnected devices. Conducting a risk assessment aids in categorizing devices according to their vulnerabilities, criticality in patient care, and potential impact of a security breach. Key considerations include:
High-Risk Devices: Devices such as life-support systems and diagnostic imaging equipment, identified as high-risk due to critical functions or vulnerabilities, may be isolated in dedicated network segments with stringent security measures and limited access.
Lower-Risk Devices: Devices with fewer vulnerabilities or less critical operational roles may be grouped into less restrictive network zones. Nevertheless, these devices necessitate sufficient security controls to prevent unauthorized access and mitigate potential risks.
Segmenting the network based on risk assessments ensures that security measures are tailored to the specific needs and vulnerabilities of each category of biomedical device.
Implementing Access Controls and Segmentation Technologies
Effective enforcement of security policies and preservation of segmented network integrity heavily rely on access controls and advanced segmentation technologies. Key strategies encompass:
Access Control Mechanisms: Deploying firewall rules, access control lists (ACLs), and network segmentation policies to govern traffic flow between distinct network zones. These mechanisms thwart unauthorized access and diminish the potential threat landscape.
Software-Defined Networking (SDN): Leveraging SDN technologies provides centralized control and programmability of network infrastructure, facilitating dynamic adjustment of segmentation policies in response to real-time security requirements. SDN enhances flexibility in managing network segments and addressing emerging threats effectively.
By harnessing access controls and segmentation technologies, healthcare entities can proficiently mitigate risks associated with biomedical device connectivity, while maintaining operational efficiency and regulatory adherence.
In summary, defining a segmentation strategy entail delineating clear objectives, structuring network zones based on risk assessments, and deploying robust access controls and technologies. This strategic approach fortifies cybersecurity resilience and fosters secure and efficient integration of biomedical devices within healthcare networks.
Implementation of Network Segmentation
Implementing network segmentation is essential in healthcare settings to bolster cybersecurity by isolating biomedical devices and reducing the impact of potential security breaches. This section delineates the practical steps involved in executing network segmentation, focusing on designing network segments, configuring network devices and biomedical equipment, and implementing necessary security protocols.[5][6][10]
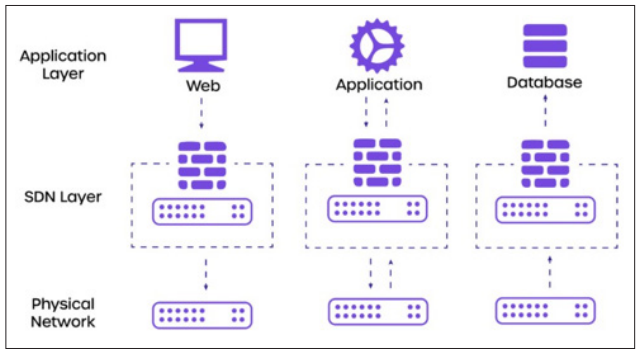
Figure 2: Implementation of Network Segmentation Designing Network Segments
Designing network segments requires a systematic approach to ensure effective isolation of each type of biomedical device according to its specific security requirements and risks. The process typically includes:
Review of Segmentation Goals: Begin by revisiting the segmentation goals established earlier to align with the organization’s cybersecurity objectives and regulatory obligations.
Network Mapping: Conduct a thorough mapping of the network to identify all biomedical devices and their connectivity needs. This step clarifies the scope and boundaries of each network segment.
Integration of Risk Assessment: Incorporate findings from the risk assessment phase to categorize devices based on criticality, vulnerabilities, and regulatory implications. This categorization guides the design of segmented zones with appropriate security measures.
Selection of Segmentation Methods: Choose the most suitable segmentation methods, such as VLANs, subnetting, or physical separation, based on the network architecture and identified security needs.
Documentation: Document the designed network segments comprehensively, including network diagrams, segmentation policies, and access control rules. Clear documentation ensures consistency in implementation and facilitates future maintenance.
Configuring Network Devices and Biomedical Equipment Effective configuration is crucial for ensuring secure operation of both network infrastructure and biomedical devices within their designated segments. Key steps in configuring these components include:
Configuration of Network Infrastructure: Configure routers, switches, and other network devices to implement the defined segmentation strategy. This involves setting up VLANs or subnets, configuring routing protocols, and establishing access control policies.
Configuration of Biomedical Devices: Configure individual biomedical devices to operate within their assigned network segments. Tasks include setting IP addresses, subnet masks, gateway settings, and ensuring compatibility with security protocols specific to segmentation.
Testing Connectivity: Conduct connectivity tests to verify that biomedical devices can communicate effectively within their segmented environments while maintaining security and operational efficiency.
Deploying Security Measures
Deploying additional security measures enhances the integrity of segmented networks and safeguards against unauthorized access and data breaches. Key security measures include:
Firewalls: Install and configure firewalls to monitor and control traffic flow between network segments, enforcing segmentation policies through traffic filtering.
Access Control Lists (ACLs): Implement ACLs on routers and switches to restrict access to specific network segments based on IP addresses, protocols, or port numbers, complementing firewall rules with granular traffic control.
Encryption: Enable encryption protocols (e.g., SSL/TLS) to secure data transmissions between biomedical devices and other network endpoints, ensuring confidentiality and integrity within segmented environments.
Intrusion Detection/Prevention Systems (IDS/IPS): Deploy IDS/IPS solutions to monitor segmented network traffic for suspicious activities or security threats, providing real-time alerts and responses to mitigate incidents.
By following a structured approach to designing network segments, configuring network devices and biomedical equipment, and implementing robust security measures, healthcare organizations can effectively enhance cybersecurity while supporting seamless biomedical device operations within their networks. These measures contribute to safeguarding sensitive patient data and maintaining compliance with regulatory standards such as HIPAA and GDPR.
Testing and Validation
Testing and validation play essential roles in implementing network segmentation for biomedical devices within healthcare organizations. These phases ensure that segmentation not only enhances security but also supports the continuous operation of critical medical equipment and meets regulatory standards [4, 7, 5].
Functional Testing of Segmented Networks
Functional testing verifies that network segmentation does not interfere with the functionality of biomedical devices. This testing ensures devices can operate effectively within their designated network segments by focusing on:
Device Operation: Checking that biomedical devices can communicate with necessary systems and services without any hindrance.
Performance Verification: Assessing device performance under segmented network conditions to maintain operational efficiency.
Integration Testing: Confirming seamless operation of segmented devices with other network components.
The goal of functional testing is to uphold the reliability and functionality of biomedical devices while implementing network segmentation.
Conducting Security and Compliance Testing
Security and compliance testing is crucial to validate that the segmentation strategy aligns with industry standards and regulatory requirements such as HIPAA, GDPR, and IEC 80001. This testing ensures:
Effective Security Controls: Proper implementation and functionality of security measures like firewalls, access controls, and encryption.
Data Protection: Adequate protection of patient data and sensitive information transmitted within segmented networks against unauthorized access.
Regulatory Alignment: Compliance of the segmentation strategy with healthcare data privacy and medical device security regulations.
Thorough security and compliance testing help identify vulnerabilities or deficiencies in segmentation implementation that require remediation.
Addressing Testing Challenges and Solutions
Healthcare organizations may face various challenges during testing that can affect the effectiveness of network segmentation:
Interoperability Issues: Compatibility challenges between segmented devices and existing network infrastructure.
Performance Concerns: Potential degradation in network performance due to increased traffic routing and segmentation complexity.
Configuration Complexity: Difficulty in configuring and maintaining segmented networks, particularly in environments with diverse biomedical devices and legacy systems.
Practical solutions to these challenges include:
Testing Environments: Setting up dedicated testing environments to simulate segmented network conditions and identify interoperability issues early.
Performance Monitoring: Implementing monitoring tools to continuously assess network performance and optimize segmentation configurations.
Automation and Orchestration: Using automation tools and orchestration frameworks to streamline configuration and management tasks, reducing errors and enhancing efficiency.
Proactively addressing these challenges ensures that segmented networks remain secure, efficient, and compliant with regulatory requirements throughout their operational lifecycle. Testing and validation are critical phases in deploying network segmentation for biomedical devices in healthcare environments. Functional testing ensures devices operate seamlessly within their segments, while security and compliance testing verifies adherence to standards and regulations. By overcoming testing challenges with practical solutions, healthcare organizations can maintain robust cybersecurity measures, ensure smooth device operation, and bolster resilience against cyber threats, ultimately enhancing patient care and organizational security.
Monitoring and Maintenance
Effective monitoring and maintenance practices play pivotal roles in a robust network segmentation strategy designed to secure biomedical devices within healthcare networks. This section focuses on continuous monitoring, regular security audits, and the importance of updating and patching devices and infrastructure [10, 7].
Continuous Monitoring of Network Segments
Continuous monitoring is indispensable for promptly detecting and responding to security incidents within segmented network environments. By actively monitoring network segments, healthcare organizations can achieve the following:
Real-time Threat Detection: Promptly identify and respond to suspicious activities or potential security threats as they occur.
Anomaly Detection: Monitor network traffic patterns to detect deviations that may indicate unauthorized access attempts or malware activity.
Performance Optimization: Ensure that segmented networks operate efficiently while maintaining robust security measures. Continuous monitoring provides healthcare organizations with the visibility needed to maintain a proactive cybersecurity posture and swiftly mitigate emerging risks.
Regular Security Audits and Reviews
Regular security audits and reviews are essential to assess the effectiveness of the network segmentation strategy over time. Key benefits include:
Assessment of Security Posture: Evaluate whether the implemented segmentation controls effectively protect biomedical devices and sensitive healthcare data.
Identification of Vulnerabilities: Identify potential gaps or vulnerabilities in the segmentation architecture that could be exploited by malicious actors.
Compliance Verification: Ensure that segmentation practices align with regulatory requirements and industry standards (e.g., HIPAA, GDPR, IEC 80001).
Conducting periodic audits and reviews enhances overall security resilience and helps healthcare organizations stay aligned with evolving security best practices.
Updating and Patching Devices and Infrastructure
Timely updates and patches are crucial for mitigating security risks associated with biomedical devices and network infrastructure. Key considerations include:
Vulnerability Management: Regularly applying security updates and patches to devices and infrastructure components to address known vulnerabilities.
Firmware and Software Updates: Ensuring that biomedical devices are running the latest firmware and software versions to mitigate potential exploits.
Configuration Management: Implementing consistent configuration changes and updates to strengthen security measures across segmented network zones.
Prioritizing updates and patches significantly reduce the likelihood of security breaches and ensures the ongoing integrity of segmented network environments.
Monitoring and maintenance are foundational aspects of effective network segmentation strategies in healthcare settings. Continuous monitoring facilitates proactive threat detection and response, while regular security audits and reviews uphold ongoing effectiveness and regulatory compliance. Timely updates and patches further reinforce security defenses, safeguarding biomedical devices and patient data against evolving cyber threats. Integrating these practices into their cybersecurity framework enables healthcare organizations to maintain secure and resilient network segmentation environments essential for safe patient care delivery.
Incident Response and Management
In healthcare settings, where safeguarding biomedical devices is critical, having a well-structured incident response and management plan is essential to promptly address security breaches and minimize their impact [10, 7].
Developing an Incident Response Plan
Crafting an incident response plan tailored to the unique challenges of securing biomedical devices ensures healthcare organizations are prepared to effectively manage security incidents. This plan typically includes:
Incident Identification and Classification: Procedures for recognizing and categorizing security incidents involving biomedical devices.
Response Actions: Defined steps and responsibilities for mitigating the incident, containing its effects, and restoring normal operations.
Communication Protocols: Guidelines for internal and external communication, including notifying relevant stakeholders and regulatory bodies when necessary.
Post-Incident Review: Processes for conducting a thorough analysis after an incident to extract lessons learned and enhance future incident response efforts.
Training and Drills for Incident Response Teams
Regular training sessions and drills are vital for ensuring incident response teams are well-prepared and capable of responding promptly and effectively to security incidents involving biomedical devices. Key aspects of training and drills include:
Role Familiarization: Ensuring team members understand their roles and responsibilities during different stages of an incident.
Simulation Exercises: Conducting simulated exercises to practice incident response procedures in realistic scenarios.
Continuous Improvement: Using feedback from drills to refine the incident response plan and improve team readiness.
Case Studies of Incident Response in Healthcare Settings Real-world examples of incident response scenarios within healthcare settings provide valuable insights and lessons learned. These case studies highlight:
Preparation Benefits: The importance of proactive preparation and having a well-defined incident response plan.
Effective Strategies: Successful tactics and strategies used to mitigate and manage security incidents involving biomedical devices.
Lessons Learned: Challenges faced, and improvements made based on real experiences, which can inform and strengthen future incident response efforts.
Best Practices and Recommendations
Effective network segmentation is foundational to securing biomedical devices within healthcare environments. Key best practices include [6-8, 11 ]:
Comprehensive Inventory: Maintaining an updated inventory of all biomedical devices connected to the network.
Regular Risk Assessments: Performing periodic risk assessments to identify vulnerabilities and prioritize security measures.
Robust Access Controls: Implementing stringent access controls, such as firewall rules and access policies, to restrict unauthorized access to biomedical devices and data.
Recommendations for Healthcare Organizations Actionable recommendations for healthcare organizations to enhance their cybersecurity posture include:
Adopting Advanced Segmentation Technologies: Utilizing technologies like Software-Defined Networking (SDN) for more flexible and scalable network segmentation.
Continuous Monitoring: Implementing continuous monitoring solutions to detect and respond to potential security threats in real-time.
Prioritizing Updates and Patches: Ensuring biomedical devices and network infrastructure are regularly updated with the latest security patches and firmware updates to mitigate vulnerabilities.
Future Trends in Network Segmentation for Biomedical Devices
Emerging trends and technologies in network segmentation offer promising advancements for securing biomedical devices:
Artificial Intelligence and Machine Learning: Using AI and ML algorithms to analyze network traffic patterns and detect anomalies that may indicate security threats.
Automation: Implementing automated response mechanisms to swiftly isolate compromised devices and mitigate the spread of threats within segmented networks.
Integration with IoT Security: Enhancing network segmentation strategies to accommodate the increasing complexity of interconnected IoT devices in healthcare environments.
These future trends hold considerable potential to significantly improve the efficacy and responsiveness of network segmentation strategies in safeguarding biomedical devices against evolving cybersecurity threats.
Conclusion
The conclusion of the review emphasizes key points underscoring the importance of network segmentation for biomedical devices in healthcare. It summarizes that effective segmentation is essential for enhancing cybersecurity tailored to these devices, stressing continuous improvement and adaptation to evolving threats. Healthcare organizations are encouraged to maintain vigilance and proactive security measures to protect biomedical devices and patient data integrity. The conclusion underscores that robust network segmentation is pivotal for safeguarding devices and ensuring compliance with industry standards and regulations. It reiterates that a strategic approach to segmentation not only mitigates risks associated with device connectivity but also enhances overall cybersecurity resilience in healthcare.
References
- Loncar Turukalo T, Zdravevski E, Machado da Silva J, Chouvarda I, Trajkovik V (2019) Literature on Wearable Technology for Connected Health: Scoping Review of Research Trends, Advances, and Barriers. J Med Internet Res 21: e14017.
- Shang Gao, Zecheng Li, Yuan Yao, Bin Xiao, Songtao, et (2018) Software-Defined Firewall: Enabling Malware Traffic Detection and Programmable Security Control. The Hong Kong Polytechnic University 12.
- (2014) Cybersecurity in Medical Devices Guidance for Industry and Food and Drug Administration Staff. Center for Devices and Radiological Health 1-10.
- Paul Dunbar, Laura M Keyes, John P Browne (2023) Determinants of regulatory compliance in health and social care services: A systematic review using the Consolidated Framework for Implementation Plos One 18: e0278007.
- Neerja Mhaskar, Mohammed Alabbad, Ridha Khedri (2021) A Formal Approach to Network Segmentation. Computers & Security 103: 102162
- Dr Choong May Ling (2020) Principles and Practices for Medical Device Cybersecurity. International Medical Device Regulators Forum 1-46.
- Feilx A Tettey, Santhosh Kumar Parupelli, Salil S Desai (2023) A Review of Biomedical Devices: Classification, Regulatory Guidelines, Human Factors, Software as a Medical Device, and Cybersecurity. Springer Science Bussiness Media 2: 316-341.
- N Wagner, Sahin CS, Winterrose M, Riordan J, Pena J, et (2016) Towards automated cyber decision support: A case study on network segmentation for security. IEEE Symposium Series on Computational Intelligence 1-10.
- Reza Azad, Ehsan Khodapanah Aghdam, Amelie Rauland, Yiwei Jia, Atlas Haddadi Avval, et (2022) Medical Image Segmentation Review: The success of U- Net. ArXiv https:// arxiv.org/abs/2211.14830.
- https://www.cisa.gov/sites/default/files/publications/layering-network-%20security-segmentation_infographic_508_0.pdf.
- (2021) Strengthening Cybersecurity Practices Associated with Servicing of Medical Devices: Challenges and U.S. FOOD & DRUG ADMINISTRATION 1-6.

