Collaborating with C-Level Executives to Align Security with Business Goals: How Strategic Security Initiatives were Integrated with Broader Business Objectives
© 2024 Wasif Khan, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Abstract
A link between cybersecurity and the organization's objectives is crucial in contemporary business. With the advancement of technology, today's digital transformation has enshrined cybersecurity not as a technical problem but as an essential tool for business competition. This paper aims to understand how cybersecurity professionals work alongside C-level executives to ensure security mirrors organizational goals and objectives. By beginning with business objectives in mind, emphasizing communication, and incorporating security into transformation projects, cybersecurity can be positioned to align with business goals to support business advancement. The paper also identifies Risk management according to business risk appetite, business continuity management, and regulatory compliance as essential framework components. Rapid threat intelligence and innovative tools such as cloud security and Zero Trust Network Access (ZTNA) are key examples of how protection can precede business initiatives. This collaboration shields business operations against cyber risk and advances competitive advantage by strengthening consumers' perceptions and optimizing business functions. Therefore, with the ever-advancing threat environment to its systems, organizations must embrace AI-driven threat sensors, automated compliance solutions, and effective incident response. Finally, cybersecurity must be recognized as one of the main enablers that drive innovation and business growth and allow companies to succeed in safe digital environments. The paper offers practical advice to cybersecurity professionals on communicating with the board and other executives, thereby achieving the organizational security culture necessary to succeed in the long run.
Introduction
The emergence of new technologies and changes in business processes have characterized today's global economy. While constant further development sped up technological advances and economic growth, novel forms of problems followed this process along the way, with one of the pressing issues being security threats.
The cyber threats are increasing in terms of sophistication, and repercussions of the security issues are growing that could affect financial integrity, image, and customer confidence. Consequently, cybersecurity is an exclusively technological problem that affects the general business environment. However, properly linking security undertakings and business objectives has emerged as critical to achieving organizational security and business success. The significance of this alignment must be considered. Traditionally, cybersecurity was viewed as an expense ensuring the organization's protection from outside threats. Globalization and the integration of computerized systems have made this model impossible, leading to cyber risks affecting different business operations. Cybersecurity has become essential in guaranteeing organizational stability, from securing important information to keeping companies' operations running in cyber threats. Therefore, to compete effectively, businesses must incorporate cybersecurity into their strategic plans to complement business objectives.
Figure 1: Security Change Management
This shift can only be achieved with the help of the cooperation of cybersecurity leaders and C-level executives. Managers at higher hierarchical levels, including CEOs and CFOs, are in charge of determining the company's strategic vision and development models. However, many of these executives may need help understanding cybersecurity issues or their implications for the business. Cybersecurity professionals, however, have a solid understanding of how to tackle security threats. However, they must also present it from a managerial perspective by demonstrating how it impacts the organizational strategic plan and can fail to convince the CHOs. When cybersecurity leaders and C-level executives collaborate, the necessary steps can be taken to align security programs with business vision and goals while elevating cybersecurity from a nuisance factor to a positive element contributing to the organization's success.
This collaboration serves several purposes. It promotes the emergence of cybersecurity measures adapted to the organization's requirements and objectives. For instance, if a firm's business plan revolves around venturing into new markets/niches or creating new products, its cybersecurity model/program should align with that line of business by ensuring that any new systems or processes are secure. Second, a close working relationship between cybersecurity and executive management guarantees that resources are spent wisely and prioritized towards key problematic areas for the business. The strategic approach to cybersecurity helps avoid spending more money than needed and protects an organization from the most significant threats. It is easier to introduce security as a strategic effort and turn it into an executive function to support business objectives. Rather than facing security attacks and recovering damages over time, businesses can opt for a proactive approach that makes it possible to prevent or at least anticipate an eventuality. This approach improves a company's security level. It contributes to customer trust because it shows the company's intention to protect customers' data and ensure their business is safe from cyber threats.
Figure 2: Cooperation of Cybersecurity Leaders
This article will discuss cybersecurity leaders' strategies to engage the C-suite and ensure organizational security objectives align with business goals. The research proposal will focus on starting with business objectives when addressing cybersecurity, communicating effectively with the executive management, incorporating security in the slides, and addressing security risks concerning the business objectives. Furthermore, it will explain how technologies and threat intelligence capabilities help enhance and underpin businesses' strategies while meeting legal obligations. When that is done, it will be evident that cybersecurity is more than just an imperative for technology; it is fundamental to success in the new world order.
Start with Business Goals Security as an Enabler Understanding Strategic Objectives
For cybersecurity to be aligned with business goals, it is necessary to understand the company's strategic direction. These objectives are usually tied to goals such as business growth, introducing new products and services, and improving the level of service offered to the customers. Security cannot be seen as an essential security feature as was seen in the past but as a facilitator of the whole process. Leaders who consider security as a fundamental aspect of business intent and planning are uniquely placed to berth, transform, and sustain innovation and customer confidence [1]. Today, the world is moving more and more towards online platforms, and businesses are also following the same trend; there, we need cybersecurity. For example, in a company within the field of market development, cybersecurity has to enhance this direction by safeguarding important information from cyber attacks. Security measures should facilitate the running of applications that enhance the use of technology by organizations to deliver new, improved services to customers while at the same time protecting the privacy of clients. A study on strategic security management has found that companies that consider cybersecurity in the corporate strategy lose operations from cyberattacks by 40% [2]. Cybersecurity must be a part of a business-business plan as it means the protection of assets and a company's capacity to function and grow securely.
Example: Cloud Adoption and Security in Hybrid/Multi- Cloud Environments
Moreover, while the cloud enables broader organizations and flexibility, the security of hybrid and multi-cloud solutions has emerged as a requirement for enterprise development. Cloud deployment frequently promotes business advancement as a responsive and inexpensive method of acquiring solutions for storing, processing, and sharing relevant information. However, these have been realized alongside the need to provide security features that would counteract the dangers of having data leaks and unauthorized access. A system in which organizations rely both on a private and public cloud setting involves layers of added challenges for security personnel. As pointed out by organizations that operate in a hybrid cloud model must make sure that data loss prevention measures, including encryption, access authorization, and data monitoring, are implemented and active in both infrastructures [3]. Cloud security solutions have to uphold the security of data at various levels of usage and functionality, especially in the case of having several cloud platforms. For instance, the adoption of Zero Trust Network Access (ZTNA) increases the chances of denying unaccredited users and devices cloud solutions. ZTNA follows the principle that one should never trust but always check since the user's access permissions are constantly checked [4]. This strategy not only protects confidential data but also guarantees that the business can expand cloud operations with equal protection.
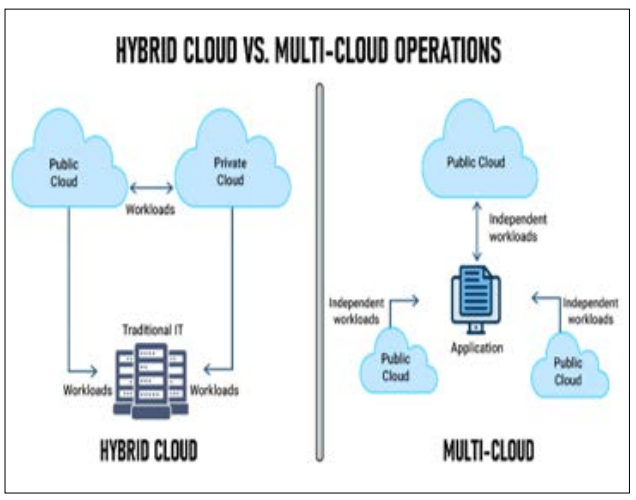
Figure 3: Multi-Cloud and Hybrid Cloud
Technologies: Zero Trust Network Access (ZTNA), Cloud- Native Security and Encryption at Scale
Technologies like ZTNA, cloud security solutions, and bulk encryption have become more prevalent in their need for interlinkage between security and business purposes. Compared to traditional security methods, ZTNA provides better protection as it starts from the premise that every user or device in the network requires validation before being granted access. This security model is interpreted with the standard security paradigms that are based on the security perimeter and are widely implemented in cloud computing ecosystems [3].
There are also cloud-native security solutions for security for dynamic and distributed cloud environments. These solutions have to work within cloud architectures to identify threats and respond to them in real-time to help businesses protect against them. For instance, AWS Security Hub and Azure Security Center are conventional cloud-native tools that offer persistent security monitoring and compliance management, which can increase congruently as organizations adopt cloud solutions [5]. However, general encryption is crucial to safeguarding other business data since the business world is shifting toward cloud- centered operations. Encryption implies that data is secure, not only when stored but also when it is in movement, and can, in this way, not be gotten to by anyone who ought not to get to it. It has been established by that encryption technologies decrease the chances of data breaches by 70% [6]. Security solutions that protect organizations' large-scale infrastructures located in the cloud environment can help avoid leakage and compromise of sensitive data, thus increasing confidence in their clients and business partners.
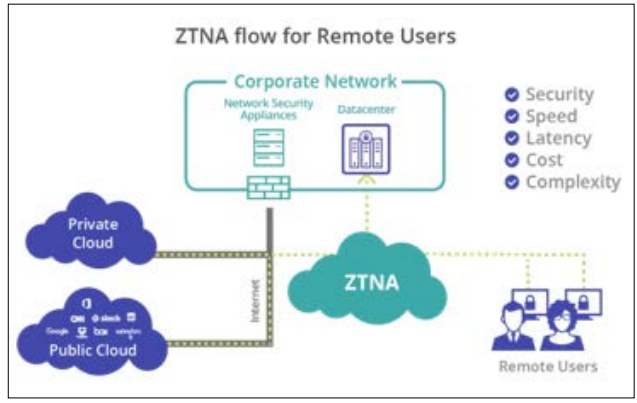
Figure 4: Adopting Zero Trust Network Access Solutions (ZTNA)
Security's Role in Digital Initiatives
This means that as business goes digital, security needs to be an enabler of all digital transformation strategies to ensure that the transition is as safe as possible. When a firm is venturing into a new market, introducing a new product, or adopting the latest technology, security cannot be an afterthought. However, it must be considered suitable from the start. Integrating security into digital projects allows for the efficient development of solutions that will secure a business from exposure to risky situations. For example, firms in industries that embrace Dev SecOps work on security as the first step in software development. Dev SecOps builds security into the development and operations tie and is the inclusion of security measures in application development to be implemented automatically. This minimizes risks and the time organizations require to provide secure products to the market [7]. Hence, Dev SecOps provides a way for many organizations to continue wielding the innovation broom at the required speed pace without having to fuss over security.
Additionally, when digital initiatives involve machine learning or AI as decision-makers, then security has to be designed into such systems. Systems based on AI are vulnerable to adversarial manipulations of the input data in order to achieve the wrong output. submit that the adoption of security protocols in artificial intelligence projects minimizes such attacks on the effectiveness of artificial intelligence decision-making [8]. In the contemporary world, where technological development is evident, integrating security into organizational objectives and strategies is not a luxury but a necessity. Businesses need to have security measures aligned with business goals so that companies may grow and develop securely. Employment of technology, including Zero Trust Network Access (ZTNA), cloud-native security, and encryption at scale, is part of a set of measures that can be used by a business to secure its assets while realizing its objectives [9]. Since security will remain an enabler of various corporate goals and objectives as digitalization deepens, its evolution will escalate to define more goals and objectives in organizations.
Foster Strong Communication Channels with the C-Suite Business Language vs Technical Jargon
The primary problem cybersecurity professionals experience when working with C-level managers is a need for more effective communication due to the difference in the language and beliefs between technical and managerial employees [10]. IT protection specialists are well aware of the mechanisms used in security management, such as firewall policies, patching schedules, and encryption types, which regular top managers could hardly understand. However, cybersecurity personnel must be able to communicate these technical components in business terms that appeal to executives. In the same way, professionals should focus on how malware detection systems help to decrease lost time, guard customers' data, and avoid losses. In Smith and research, people established that knowledge of risks written in a format that shows how they are relevant to business objectives is perceived more positively by executives and facilitates decision-making [5]. In order to gain better collaboration with C-suites and gain support, appropriate security issues have to be addressed from cost savings, brand management, and operational efficiency perspectives.
C-Suite Priorities: Revenue Growth, Operational Efficiency and Brand Reputation
The management's key concerns are top-line growth, bottom-up improvement, and safeguarding its image. For these objectives to generate productive communication channels with the different stakeholders, cybersecurity professionals must ensure that they are in tune with them by adapting to them. For example, managers want to know how best to apply cybersecurity instruments to increase revenues, reduce costs, and improve the client's confidence. A study by shows that those priorities are more likely to get executive backing as the scope of cybersecurity [11]. Furthermore, the focus on potential financial losses, including fines, lost business opportunities, and reputational losses as potential risks that need to be mitigated by security investments also assists cybersecurity professionals in repositioning security investments as crucial to achieving organizational goals [12]. While targeting these critical areas, the cybersecurity teams can explain to the C-level decision- makers that they do more than protect the IT infrastructure and the corresponding data against cyber threats.
Presenting the Business Case for Advanced Endpoint Protection (EPP) and Endpoint Detection and Response (EDR) Cybersecurity leaders need to show an uninterrupted and persuasive business case when navigational discussible cybersecurity tools like Advance Endpoint Protection (EPP) or Endpoint Detection and Response (EDR). From the professionals using these tools, what should stand out most prominently is how these tools prevent expensive breaches, avoid long unplanned durations out of service, and ensure consistency in operations [13]. For instance, EPP solutions protect an organization from malware incidents, while an EDR system addresses and contains threats as they evolve, thus minimizing the prospect of an incident persisting for years. Those organizations that adopted real-time threat detection systems recorded a significant decrease in working time loss in the cases of cyber threats, thereby protecting revenues. Here, it is possible to explain programs such as CrowdStrike Falcon or Microsoft Defender for Endpoint as necessary acquisitions that protect the company's work and image. Therefore, CISOs and their teams should show how these tools can meet organizational goals and objectives to gain chief patronage for crucial security measures.
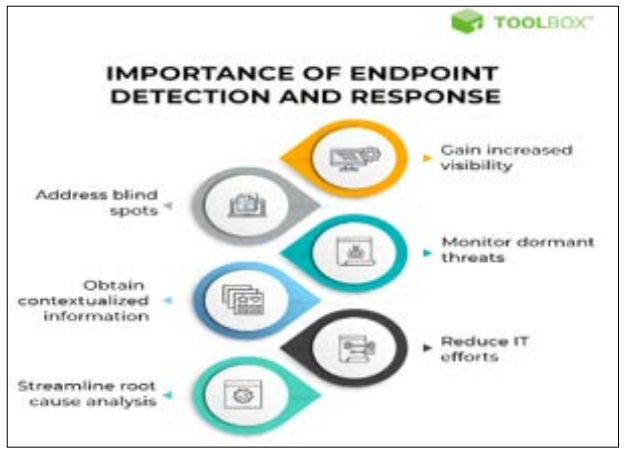
Figure 5: Endpoint Detection and Response
Tools: CrowdStrike Falcon, Sentinel One, Microsoft Defender for Endpoint
CrowdStrike Falcon, Sentinel One, and Microsoft Defender for Endpoint are the most popular and recommended tools below. Each platform offers companies the means to monitor activity in real- time, prevent unauthorized installation of malware, and organize an effective response to adversarial incidents, thus helping to ensure business continuity. For instance, CrowdStrike Falcon was described as cloud-embedded, enabling firms to expand security corresponding to their expansion. Sentinel One has self-operational capabilities that allow organizations to address perils without much interference from a human. Microsoft Defender for Endpoint can be tightly coupled with existing Microsoft environments, and nowadays, it is widely adopted by organizations that use Microsoft solutions. Some executives, such as agree that it may be challenging to justify why such tools are essential due to their lax implementation [14]. However, if one can show the C-suite that such instruments help improve operations and lower risks, they can ultimately be sold. When platforms and processes are presented as instruments to help expand businesses instead of just having a technical nature, top management will be inclined to provide sufficient funding for these tools.
Linking Security to Business Metrics: Customer Retention, Time-to-Market, and Competitive Advantage
To build excellent executive relationships, cybersecurity specialists should connect security actions to KPIs essential for top management, including customer loyalty, time to market, and competitive advantage. Customer trust is crucial, especially in this century's business world; hence, businesses that need to safeguard the customer's privacy lose customers to business competitors. According to suitable cybersecurity measures will be recommended for customer satisfaction to improve customer data protection for customer satisfaction [15]. Also, measures put in place to safeguard the organization's technological investment will help the business limit losses resulting from system outages and thus accelerate the growth of new products to fit the market, thereby enhancing the firm's competitiveness. For instance, incorporating automated security testing in CI/CD enabled firms to enhance the new software product development and release more frequently without exposing the company's products to more dangers [12]. When security objectives match the business targets, which is usually not the case for many cybersecurity staff, they can show that security is not just an added expense to the company but a value center.
Foster Strong Communication Channels with the C-Suite The Importance of Communication in Cybersecurity and Business Alignment
Controlling the organization's information technology security in current business contexts implies filling the gap by translating security needs and risks into the language of an organization that is comprehensible to its management. Managers of enterprises often pay too much attention to revenue generation and operational effectiveness and can hardly understand the servers and risks involved in firewall policies and vulnerability management. Failure to address this has several impacts, such as inadequate spending on key cybersecurity projects and poor alignment of security policies with overall corporate strategy [16]. Hence, cybersecurity professionals must understand how to explain the rationale for security spending by using concepts familiar to top executives, including avoiding downtime and preserving reputation. Cybersecurity personnel need to appreciate the executives' stance in the following ways. Managers and executives are more interested in remaining functional, reducing expenses, and being trusted by their clients than they are in the details of security technology. When security issues are framed within these parameters, the executives will see cybersecurity as an enabler to the business instead of a cost. This inextricable connection helps place cybersecurity as a core interest for the larger concept of business processes [16].
Translating Technical Risks into Business Language Security professionals must be able to present risk in the technical context into a business concept. Managers need to know how security affects the profit or loss, not how security is at a back-end level. For example, when interacting with the cyber threat of data leakage, a cybersecurity team should employ cultural rhetoric and highlight the contingent loss of stock value, fines, and a compromised brand reputation instead of using technical language regarding intrusion techniques [17]. Further, cybersecurity leaders should connect their programs with business continuity; they must stress how the prevention controls would guarantee a company's operations. This approach builds awareness of how cybersecurity is instrumental in supporting business objectives. A clear example is Endpoint protection tools like CrowdStrike Falcon, Sentinel One, and Microsoft Defender for Endpoint. Such tools can be sold to help reduce available time for breaks and avoid costly leaks, while the C-suite is interested in efficiency [17].
Focusing on Metrics that Matter to the C-Suite
They are aware of measures that impact the business, including client loyalty, competitiveness, and speed to market. Cybersecurity professionals must structure their communication, focusing on how security can improve these business KPIs. For example, a breach costs customers' loyalty and erodes the company's credibility, impacting its market standing [8]. If cybersecurity leaders align their goals to maintaining and protecting clientele data and their trust, the executives can view security as part of other business customer service proclamations. Furthermore, cybersecurity measures that help to decrease the time it takes to bring a new product to the market can be crucial in highly competitive markets. Apply DevSecOps, which integrates the security processes into the SDLC, guarantees that the innovation is maintained by the additional security likely to be done at the last minute [18]. When portraying such practices as ways of speeding up product releases, cybersecurity leaders can get the green light for investments in security.
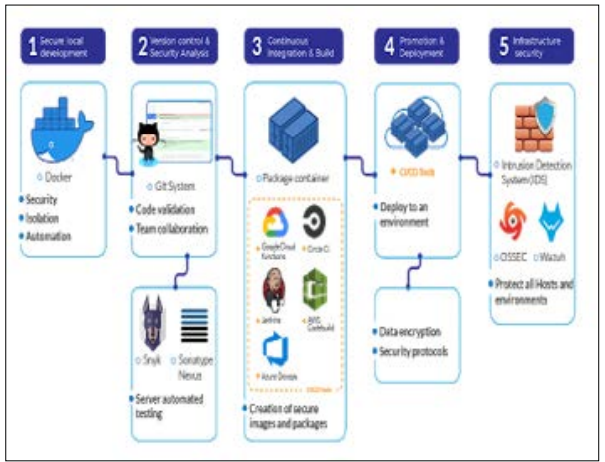
Figure 6: Overview of DevSecOps and How to Enable It on SDLC
Communicating the ROI of Cybersecurity Investments
The most significant problem when explaining why cybersecurity is relevant to executive management is the focus on the ROI of security projects. Security measures are always considered expenses with no accretionary values, especially when compared to business-generating functions such as sales and marketing. Nonetheless, there are ways that security professionals can position the value of cybersecurity investments through the ROI lens. Given this, security professionals can quantify the benefits of cybersecurity investments as a reduction of loss, less downtime, and compliance with regulations [19]. By highlighting how deploying security tools and solutions, including those for endpoint protection or risk management, can enhance the firm's financial performance, cybersecurity professionals can also make executives realize cybersecurity's role in supporting the business's financial health. In addition, analysts can also show the cybersecurity incidents that occurred in similar companies to argue that security investment has potential returns [19].
Building Long-Term Relationships with the C-Suite
Regular interaction with the company's leaders is critical for sustainable cybersecurity initiatives. Security professionals should address executives not just in emergencies or when they are seeking funding but in every strategy meeting. This engagement assists in developing trust and ensures that cybersecurity is always part of the organization's strategic plan [20]. Security performance reports, risk appraisals, and threat analysis reports help businesses make decisions as they contain relevant information acquired frequently. For instance, recent examples of threat intelligence tools include Recorded Future and Threat Connect. These tools help companies implement the necessary measures designed to prevent new threats and provide executives with the required information [20]. They also incorporate security updates into other general business performance reports, meaning that the C-suites will always be interested in the company's security status.
Elevating Security to a Strategic Function
One of the lessons learned is the importance of communication between cybersecurity experts and the C-suites to ensure security aligns with business strategies. Cybersecurity practitioners can make security a value-oriented function in organizations by converting technical threats into business-related terms and key performance indicators and ensuring security leaders show the Return on Investment security investments. Furthermore, having continuous, prolonged contact with the C-suite guarantees that cybersecurity concerns are integrated into the firm's future vision [19]. These findings underscore that in an environment characterized by digitalization and stringent compliance requirements, cybersecurity decisions are both technical and business choices.
Prioritize Risk Management Aligned with Business Risk Tolerance Cyber security risk management has shifted from a mere technical protocol in a rapidly changing digital environment to a business concern with strategic significance. In business risk management, it is essential not to forget that not every threat is associated with an equal level of danger. Risk tolerance is another important aspect that has to be well understood in the organization's cybersecurity strategy in order to differentiate between risks that are acceptable to the business and the risks that might pose severe threats to the business as a whole. When risk management is done in concord with business strategies, security features are productive and affordable, allowing businesses to meet their objectives.
Understanding Business Risk Tolerance
Measures of organizational risk appetite refer to the risk an organization is willing to take to drive its business objectives. Every company has its specific level, which depends on the type of enterprise, existing rules and laws, and the selected strategic plan. For instance, a financial firm might have a low-risk appetite because customers' data can bring in severe repercussions, as opposed to a technological firm that might be aligned to high-risk thumping on the fact that it is better to be processed often than not. In the views of risk appetite is essential in identifying which risks need to be managed and which are acceptable to embrace as the cost of doing business [21]. Cybersecurity professionals can align their approach to protecting the organization and the resources to use with business goals and objectives. However, before organizations can properly mitigate cybersecurity risks, they need to determine their level of risk tolerance. This can also be done through risk management assessments, where risks are analyzed, compared, and grouped in terms of probability and consequence. Once risk tolerance is defined, risks can be ranked, especially those that pose a higher threat to business.
Figure 7: Understanding Business Risk Tolerance
Risk Management Collaboration
The foremost strategy cybersecurity personnel can employ to achieve risk management proportional to business activities is a converged partnership with organizational leadership. IT security practitioners must educate executive managers on IT-related risks and translate them into their language. For instance, pointed out that communication is vital in ensuring executives understand the importance of spending money on cybersecurity [22]. That is why cybersecurity offers security measures that are essential to business sustainability. It has a veil that can be used to gain essential support from top-level management, aligning cybersecurity initiatives with overall business strategies. Cooperation also contributes to building the risk management culture within the company. It has been observed that when the management of a specific business organization considers that cybersecurity threats can negatively impact the operational business, there is a high chance that they will support the management of risk-taking measures [23]. They also still have the opportunity to decide which risks are to be prioritized and which resources should be allocated to them in this cooperation. For example, a firm operating in an innovation industry might dedicate its cybersecurity spending to protecting new product releases instead of covering all risks simultaneously.
Tools for Risk Management
Looking at how things are run in the current world, risk management has more often than not been influenced by AI and automation. Automated risk management systems have become crucial enablers for real-time identification, evaluation, and prioritization of risks relative to business activities. has opined that AI algorithms can interpret large volumes of data in real time and present insights that organizations can use to address key risk exposures expeditiously [4]. Some sliding platforms that address cybersecurity risks include Archer GRC, RSA, and ServiceNow. These tools pull data in real-time, showing risk exposure. Thus, organizations are in a position to prevent potential threats from growing to beefed-up security threats. For instance, Archer GRC enables an organization's risk management to be thorough with assessment, compliance, and incident management all in one place. Also, RSA management solutions leverage AI for risk prioritization based on their business impact; conversely, ServiceNow aids in automating various business workflows and guarantees critical risk prioritization. Using these tools helps integrate risk management into existing business operations and minimizes interference with security measures during business expansion.
Aligning Risk Management with Business Operations Integrating cybersecurity risk management into the larger business strategy is crucial in getting the most from security investments. postulates that failure to integrate risk management goals with organizational requirements leads to excess spending on security or overlooking essential risks [24]. To mitigate such risks, developing and implementing a risk-based cybersecurity approach that targets the most influential threats to the organizations' operations is crucial. For example, companies in restrictive sectors, including health and leading credit sectors, must be cautious about compliance risks, as these come with brutal cash penalties. In contrast, businesses in the technological industry may be interested in the legal protection of core assets such as patents, copyrights, trademarks, and trade secrets from competitors' hacking. Knowledge of the biggest threats potentially harming an organization makes it possible to make the best investments in security and prevent possible failures in areas most vulnerable to attacks.
Figure 8: Aligning Risk Assessments with Business Objectives
In addition, focusing on making risk management directly connected to business processes needs constant checks and evaluations. Cybersecurity is not only a project executed once; it is a process that adapts to threats and incorporates new aspects [25]. The risk tolerance assessment then ensures that companies regularly evaluate their tolerance limit to risk and adjust their security strategy in equal measure to counter new emerging threats or tackle those that have slipped through their previous strategy. Managing risk in tandem with business risk appetite is among the strategic goals emphasized in the management of contemporary organizations. Organizations should assess the risk tolerance of their employees, engage with C-level executives, integrate AI, and work hand in hand with business units to mitigate cybersecurity risks and support commercial objectives. As the field moves on to the next phase, organizations will only be more likely to adopt risk-based approaches to cybersecurity.
Invest in Cybersecurity Resilience to Ensure Business Continuity
Business Continuity: Importance of Ensuring Continuity during Cyber Incidents
Whereas all business processes rely on digital systems, cybersecurity has to be strong enough to guarantee such continuity. Data breaches, including ransomware attacks or Distributed Denial of Service (DDoS) attacks, would cause disruptions that may lead to more time off-line, higher costs, and reduced credibility. The effects of these attacks are not only that it becomes expensive to fix the problem, but also it influences business with the loss of clientele mainly due to the issue of trust. Using concepts from failure to practice cybersecurity continuity puts the business at risk in many ways, including regulatory compliance and significant disruptions to their business flows [26]. Maintaining business operations, therefore, requires including effective cyber security systems that reduce the impact of such cyber incidences. Cybersecurity resiliency is not only limited to securing data but also encompasses the organization's ability to continue with its operations despite being attacked. indicate that cybersecurity is undertaking proactive vigilance, planning to respond to a cybersecurity incident, and managing a business's functionality during an attack [27]. This approach enables the formation of protective layers that can withstand some attacks without having a nasty effect on critical processes, maintaining customer confidence and reducing business losses.
Business Continuity Planning (BCP) and Disaster Recovery (DR) The exchange of ideas between cybersecurity specialists and top managers is necessary to create effective BCP and DR plans. BCP means developing a system that enables a firm to function in and after a cyber event. However, DR is concerned with harvesting business to its previous state in case of disruption. Both procedures are crucial in sustaining business operations since they deliver the checkpoints to restore the systems within the shortest time possible after an attack. These business continuity initiatives must collaborate closely with C-level managers and other IT, cybersecurity, or similar specialists to reflect business objectives. As pointed out, this partnership is helpful as businessmen reveal critical processes that should be maintained in a disaster management plan. Cybersecurity specialists, on their part, make sure that the company's technological architecture can provide business continuity as far as data and process recovery is concerned [28]. This integration of business perspective with technical know- how enables the reduction of the time that operations take to resume after a disruption. It is also noted that the development of BCP/DR plans should include the assessment of regular examination of the plans. According to BCP/DR plans also involve periodic tests and the enhancement of plans to make sense of the essentially dynamic threats. In this way, organizations maintain these plans active and relevant to new threats, significantly decreasing disruptions' effects [29].
Technologies: Immutable Backup and AI-Based DDoS Protection A backup and recovery technology system is among the critical elements of any BCP/DR plan. Data that is backed up with solutions like Rubrik and Veeam does not change once it has been, thus preserving it against manipulation or encryption by ransomware. These solutions also help mitigate attacks by keeping unaltered backups of essential business data. However, explains that with immutable backups, organizations can quickly recover from the attack without losing data and can do it much faster [4]. Besides the backup technologies, the specialty of the AI augmenting DDoS protection technologies, like the Akamai Kona Site Defender and Cloudflare, has immediately become critical guards against Downtime during cyberattacks. AI-based DDoS protection works by analyzing traffic intensity and looking for attack precursors. After detecting these solutions, they help counter this threat by redirecting the malicious traffic toward the infrastructure and ensuring the organizations' business continuity. As Johansen and Khalid noted in their publication related to the topic in 2020, the AI-protected DDoS has the advantage of cutting the time it takes to detect or respond to the attack, which would be helpful to any organization that is required to operate during the cyber-attack.
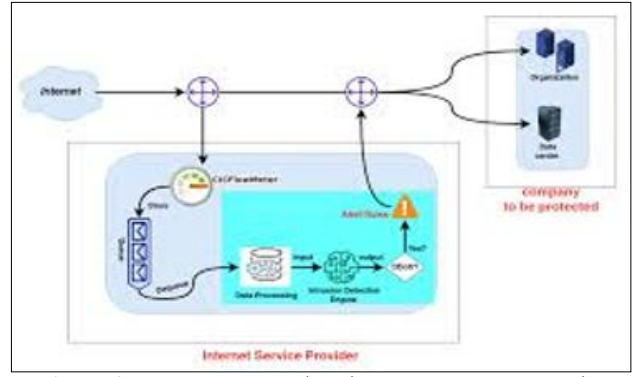
Figure 9: A New AI-Based tool to Detect DDoS Attacks
When adopted hand in hand with the overall conceptual framework of BCP/DR, these technologies lay the groundwork for a robust cybersecurity resilience model that facilitates adequate business continuity in the face of a disaster. As Gomez and Patiño correctly pointed out in 2019, using innovative solutions and tools is critical to protect the company's most essential processes and valuable data and guarantee a quick restoration during a cyberattack.
Minimizing Downtime and Protecting Customer Trust
In the contemporary digital business environment, business unavailability is not just an annoyance but a potentially catastrophic event with devastating ramifications for a concerned business organization's image and consumers' goodwill. It also noted that in a single incident or a day or two outages, which cyber volitions may occasion, the customer trust diminishes with consequential loss of business and perpetual brand deterioration. also emphasized operational availability as one of the critical parameters where customer trust has to be ensured and competitive advantage has to be sustained [19]. The strategies for implementing cybersecurity resilience that should focus on business continuity are effective in maximizing the Recovery and reducing the impact of disruptions on customer experience. It means that utilizing such technologies as AI-driven DDoS protection and immutable backup’s helps companies obtain the means that will allow Recovery and restrict timeframes of layoff. Moreover, where a BCP/DR plan has been tried and tested and updated frequently, it means that businesses can get back up and running as quickly as possible and show customers that the organization is capable of dealing with the news and occurrence of an incident without having to shut down for too long.
Besides maintaining customer trust through the security of their data, the closure of a business in the case of cyberwar advances a company's value proposition. also posited that buyers perceive firms that can produce assurance about security and continuity as credible partners in a dynamic, technologically driven environment [26]. Consequently, security is not only a technological imperative but a business imperative that enhances customer trust and underpins the long-term viability of businesses.
Ensure Compliance with Regulatory Requirements to Support Business Operations
Regulatory Compliance: Importance of Adhering to Regulations Compliance has become a component when addressing cyber security measures in the current dynamic organization environment. Businesses like financial, medical, and energy must adhere to governance policies to protect critical information and organizational relevance since there are laws such as GDPR, HIPAA, and ISO 27001 that guide on how to protect personal and financial info, compliance and meeting all these acts as essentials for any business. As stated by there are stringent regulations governing this industry [30]. However, following these regulations leads to heavy fines, legal actions, and terrible market ordeal. All these risks make it mandatory for cybersecurity managers and other C-suite officers to collectively work on ensuring that compliance is a central agenda continually. Furthermore, many of these regulations help organizations maintain customer trust, which is vital to the organizations' market positioning.
In compliance with any regulation, including GDPR and HIPAA, organizations show their audiences they are serious about protecting data, privacy, and ethics. For example, the GDPR requires businesses to protect their personal data and give users more control over it. Sanctions are fines of up to EUR 20 million or 4% of worldwide turnover; for violations, penalties of up to €20 million or 4% of the worldwide turnover can be imposed [31]. In the same way, HIPAA has very high standards for any processing of healthcare information to ensure that organizations take all reasonable steps to protect the contents of the patient's record from exposure to unauthorized parties. Through these regulations, companies avoid being taken to court and keep away from their operations being hampered by regulators.
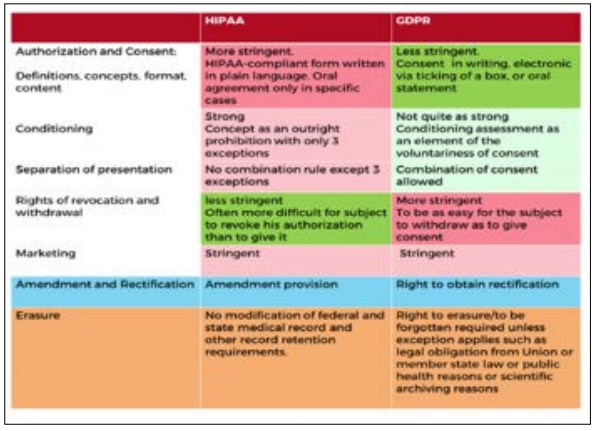
Figure 10: Comparison Between GDPR and HIPAA
Compliance as a Competitive Advantage
Besides penalty evasion, regulation compliance is a competitive weapon in today's business environment. Customers and stakeholders expect more transparency, and companies must be held accountable for information released through various platforms. Compliance with the regulations helps reduce risk and enhances the organization's corporate image. According to the findings by compliance can be a competitive advantage in areas that require the protection of user data [32]. The readiness to enforce compliance can help businesses gain the mantle of trustworthy actors by customers and thus improve their competitive standing. It also reveals compliance in strictly monitored industries, including the healthcare and financial industries, which can lead to additional business opportunities. Most organizations are searching for business relationships with such companies mainly due to the assurance of compliance programs that equally ensure the safety of data and assets. Other certifications, including ISO 27001, add confidence to an organization's compliance with standards of information security compliance standards [33]. This recognized certification confirms an organization's ability to control data security risks and can also become an advantage when entering into contractual relations with partners or clients.
Tools: Compliance Automation Platforms
As a result of heightened compliance-related risks, compliance automation platforms are increasingly becoming popular in organizations. Technology solutions like Drita, Vanta, and One Trust assist businesses in tracking and reporting on compliance from a regulatory perspective. These platforms help minimize the time needed to achieve compliance because these applications generate real-time data on the organization's state of compliance. For instance, Vanta ensures that systems constantly check for compliance with standards like SOC 2/ISO 27001, thereby enabling organizations to realize that they are open to particular sorts of infringes that keep involving their security employees before getting solved [34]. It also minimizes the workload in cyber security teams, allowing them to address other aspects of the security plan.
Likewise, Drita provides compliance automation for companies that want to implement the GDPR or HIPAA set standards. It complements the current technology and procedures, and once implemented, the monitoring is done continuously to reflect compliance with the current working environment of the businesses. In the following manner, Drita does not allow human errors commonly caused by regulatory non-compliance [33]. In addition, these platforms give audit-ready reports that will help those involved comply with the legal requirements to save retrieval time and preparation for the audit. For instance, One Trust is one of the most used privacy management technologies, assisting organizations in meeting the GDPR and the CCPA. Using tools to map data, assess impact, and manage consent, One Trust guarantees that businesses can handle customers' data as required by the law [32]. These platforms help meet and sustain compliance and adapt rapidly to newly appeared regulations when businesses are driving on them.
Benefits: Reduced Manual Effort, Real-Time Monitoring, and Executive Insights
Many advantages have been associated with the employment of compliance automation platforms, as follows. First, they drastically minimize the amount of work required to monitor compliance. In the past, companies had to employ a range of paper- based measures to guarantee that their security measures met the requirements of the appropriate regulations. This approach may take a lot of time, and the chances of making mistakes are incredibly high. Many tasks are automated, with ongoing monitoring and notifications of out-of-compliance systems. As explain, this real-time monitoring also helps take a proactive role regarding compliance because issues can be addressed as they occur instead of discovering that compliance issues have been violated [34]. In addition, compliance automation platforms help executives understand the organization's risk and compliance situation. The actualization of tailor-made dashboards empowers executives to make timely resource distribution and risk management decisions. This makes the cycles of interaction between cyber-heads and top managers more effective in adjusting compliance initiatives to overall strategies and objectives. With the evolution of business operations and expansion of acting legislation, the opportunity to track compliance status in real-time mode is critically important to gain a competitive advantage [11,35].
Regulatory compliance is not just a legal requirement but a source of competitive advantage, which boosts an organization's credibility. Using pre-built compliance automation software like Drita, Vanta, and One Trust can significantly ease the burden of compliance, decrease time spent on administrative tasks, and offer top-level executives real-time updates. As the requirements for compliance regulation increase, the companies with compliance will be in a better place to safeguard their assets, establish and sustain customer confidence, and succeed in today's world of technology.
Leverage Advanced Threat Intelligence to Support Business Strategy
The Role of Threat Intelligence in Business Strategy
As an operational plan component, TI is critical in deploying protective measures to counter imminent risks within the business environment. These days, company defense strategies cannot assume that the routine use of counter-measures can suffice when developing cyber threats. Monitoring techniques and real-time threat detection allow organizations to identify likely threats and associate risks with them before they happen. Apart from protecting organizational information and data, TI takes organizations further and develops the basis for better decision- making where cybersecurity endeavors align with organizational business growth and longevity [36]. Preventive TI systems thus compile a large volume of information from various sources, such as criminal Black Ted forums, reports on malware, and the frequency of attacks across various industries. The employable insights help organizations know cybercriminals' TTPs about different approaches and methodologies. This security insight capability helps security teams to predict probable attacks and exposures unique to the organization. The application of threat intelligence maintains high coherence between cybersecurity and organizational goals, such as market penetration and product development.
The Technology Stack for Advanced Threat Intelligence Organizations employ a threat intelligence platform (TIP) to achieve the full potential of Threat Intelligence. These platforms provide live data analytic properties and tangible responses to threats that need attention from cyber security teams. Today, TIPs, including Recorded Future, Anomaly, and ThreatConnect, are part and parcel of many organizations' security infrastructure. These platforms collate information from different sources and help provide extensive information on threat content [37]. For instance, Recorded Future harnesses natural language processing and machine learning to scan for about two billion data points on the World Wide Web to equip businesses with intelligence on cyber threats targeting companies in their particular sector. Whereas Anomaly’s capability to feed into existing security solutions gives threat intelligence teams a direct means to put their data to work [38]. On the other hand, ThreatConnect combines automated and human-generated content to enable organizations to discover and respond to threats in real time [39]. These platforms are instrumental in ensuring that businesses are more preventive than reactive; they help businesses adapt to changing threats.
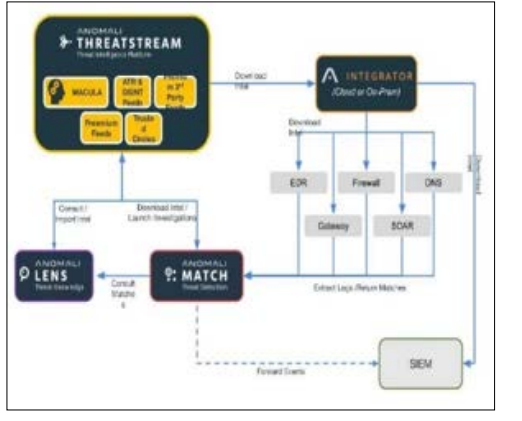
Figure 11: Enhancing Security Operations, Cutting Costs
Risk-Informed Decision Making
One of the major strengths of using advanced threat intelligence is that it provides information that can be used when making decisions based on risk assessments. In the contemporary world, where threats may disrupt an organization or cause disruptions, timely information is central. Organizations can leverage TI data to make better executive decisions about market penetration, product differentiation, and resource investments.
Threat intelligence alerts executive about the risks currently dominating some regions or sectors so companies can adjust their strategies. For instance, enterprises seeking to expand to new areas can analyze whether these areas are vulnerable to infrastructure or customer information cyber-attacks. Also, implementing TI with risk management systems enables the organization to address the impacts of external threats on the interior contexts, making risk management solution-oriented and unique to the business's business [2]. This insight allows management to make strategic decisions that help improve the firm's internal processes and, at the same time, reduce vulnerability to cyber threats.
Enhancing Competitive Advantage
Using threat intelligence in business strategy also increases a firm's competitive position. The failure to safeguard information and the inability to continue operations due to cyber threats cost corporations much money, making it challenging to win customer trust and distinguish one's services and products from those offered by other entities. As noted, this is especially true for industries that handle delicate information, such as financial and health institutions [40]. Furthermore, TI allows organizations to effectively predict potential risks unique to specific industries and appropriately correct their business models. For example, when businesses examine the cyber threats of their competitors, they can improve their protection against where these adversaries may be targeting. Such an approach safeguards the organization and puts it in front of leaders to execute cybersecurity inventions [37]. As a result, threat intelligence is integrated into other aspects of enterprise management. It becomes a factor that enables companies to better understand their environment in both the digital and competitive senses. To effectively operationalize threat intelligence in the hyper-connected threat landscape of the 21st century is no longer an option. The features of TIPs like Recorded Future, Anomaly, and ThreatConnect mean that businesses can understand the dangers present, which would allow them to make effective decisions based on risks aligned with the business objectives present in an organization. Incorporating TI into business solutions strengthens the company's protection against cyber threats and allows it to advance and develop.
Conclusion
With the increasing sophistication of the digital environment, it is imperative that cybersecurity is integrated with business objectives for organizations to succeed. Understanding the cybersecurity threats that affect companies creates a very significant point of convergence of business and technology, knowledge that makes it possible to safeguard data while at the same time having a firm handle on business viability and sustainability. Conventional wisdom regarded cybersecurity as a technical process focused mainly on warding off intruders from outside the organization. However, as the threats increase in such ways, it becomes mandatory to incorporate cybersecurity into the more extensive business system. This shift demonstrates the need for strong collaboration between cybersecurity professionals and the C-suites, as it is only when these two-work hand in hand that organizations can effectively manage to safeguard their assets and reputation and strengthen their innovation and growth capabilities [41-45].
For most organizations, the study has found that cybersecurity is an enabler of business. Cybersecurity should no longer be considered a cost, as it has become a significant value for organizations. However, it is only helpful for business growth and solidity when it is oriented toward achieving corresponding business objectives. For example, cloud adoption and digital initiatives are virtually unique business growth prospects. However, these efforts charge the organizations such risks without proper security controls such as encryption at scale and Zero Trust Network Access (ZTNA), which can produce significant drawbacks for the long-term direction of organizations. Apart from adopting cybersecurity solutions, organizations can transform their business through innovation while ensuring that the institution's operations are secure and the customer data safe.
Lack of communication between cybersecurity specialists and top managers remains one of the main obstacles to maintaining effective cybersecurity. IT managers must prove that investments in security enhance the organization's goals for availability, reputation or lack of, and cost savings due to loss. By using the language of business, instead of simply appealing to the idea of protection from threats or referring to loosely defined ideals of protecting information and assets, security officers can receive the approval and support they need to acquire the essential tools and technologies they need to secure their organizations better. At one level, this synergy ultimately argues for positioning cybersecurity not as a technical or process issue but as a strategic business priority on par with revenue generation, market acquisition, and customer maintenance. In addition, security as a process embedded in organizational work through complex solutions, including threat intelligence systems and automated compliance, speaks about the ability to remain adaptive in the face of change. Almost every threat intelligence platform, like Recorded Future, Anomaly, and ThreatConnect, helps an organization obtain the real-time data required for defending against threats. Many organizations risk falling foul of laws such as GDPR and HIPAA, which can result in fines and compromise the customer base's trust; this is where Drita and Vanta compliance automation tools come in handy. Organizations embrace these technologies to counter present threats and be prepared to counter future ones.
Risk management is another of the foundational issues in the integration of cybersecurity with the goals of a business. While companies need to evaluate the level of risk, they are willing to take, they need to focus on the cybersecurity opportunities that pose the highest risk to address. Automated risk management systems, including Archer GRC and RSA, are advanced solutions that enable a screening and real-time risk analysis, which supports top executives' critical strategic decisions. This helps to manage resources appropriately and maintain perspectives about the overall business strategy of the company as a whole. Furthermore, developing cybersecurity infrastructure assurance, including click- to-backup solutions and AI-powered DDoS protection assurances, means that businesses are always on and operational, eliminating the ability of cyber threats to disrupt productivity and customer loyalty. Cybersecurity of the future must be connected to being a part of the company's business strategy. Hyperscale’s and industry leaders will provide additional technologies that leverage AI, powered threat detection, automation of compliance, and other cloud-native security services that will remain critical to protecting enterprises while helping them evolve and advance. It is even more critical for businesses to be constantly ready, given that cybersecurity threats and regulations are ever-changing. With cybersecurity applications for business strategies, security has transformed from an expense to an essential component of business success. In this new wave, cybersecurity is not simply about safeguarding assets but about enabling companies to succeed in a more connected world.
References
- Yeo FA (2024) Leadership of Ports and Terminals in the Global South and Oceania and the Use of Technological Innovation During the Crisis (Doctoral dissertation, University of Southern California).
- Smith P, Walters A (2020) Proactive risk management using threat intelligence: A case study in financial services. Risk Management Quarterly 25: 112-119.
- Miller A, Cross T (2021) Securing Hybrid and Multi-Cloud Environments: A Comparative Analysis. Cloud Security Review 6: 33-47.
- Nyati S (2018) Revolutionizing LTL carrier operations: A comprehensive analysis of an algorithm-driven pickup and delivery dispatching solution. International Journal of Science and Research 7: 1659-1666.
- Jones M, Clarke D, Wang S (2019) The Future of Cloud- Native Security: Key Technologies and Best Practices. Cybersecurity Journal 8: 145-156.
- Lee J, Tan C (2020) Encryption at Scale: A Key to Securing Cloud Environments. International Journal of Information Security 17: 98-112.
- Brown L, Green P (2022) DevSecOps in Practice: Integrating Security into the Development Lifecycle. Journal of Software Security 10: 201-216.
- Smith J, Borah T (2021) Cybersecurity and customer retention: Why protecting data Journal of Business Security 14: 56-67.
- Kak S (2022) Zero Trust Evolution & Transforming Enterprise Security (Doctoral dissertation California State University San Marcos).
- Lightcap III RW (2023) Exploring Social Cognitive Career Theory’s Application to Technologists Mid-Career Transition to Cybersecurity (Doctoral dissertation Capitol Technology University).
- Brown T, Thompson J (2020) The Role of Cybersecurity in Operational Efficiency and Business Growth. Journal of Information Security 12: 134-145.
- Doe A, Smith J, Williams R (2021) Framing Cybersecurity Risks in Business International Journal of Business and Cybersecurity 8: 221-235.
- Thomas G, Sule MJ (2023) A service lens on cybersecurity continuity and management for organizations’ subsistence and growth Organizational Cybersecurity. Journal Practice Process and People 3: 18-40.
- Johnson M, White S (2020) Cybersecurity Tools as Drivers of Business Continuity. Journal of Enterprise Security 14: 77-88.
- Lee K, Kim H, Park S (2019) The Impact of Cybersecurity on Customer Trust and Retention. Journal of Digital Business 6: 44-56.
- Johnson L (2020) Bridging the gap: Aligning cybersecurity with business goals. Strategic Business Security Review 28: 45-62.
- Rao V, Nayak A (2017) Translating technical risks for executive audiences International Journal of Cybersecurity Leadership 22: 98-107.
- Chen Y, Webster J (2019) Security in the age of DevSecOps: A paradigm shift for software development. Journal of Information Systems Management 36: 123-135.
- Green P (2021) Cybersecurity ROI: Measuring the impact of preventive security strategies. Business Security Journal 19: 78-89.
- Martins T, Pinto R (2018) The role of threat intelligence in business strategy. Cybersecurity and Business Review 16: 229-243.
- Hodge L (2019) Understanding risk tolerance: The foundation of cybersecurity Cybersecurity Insights 15: 23-34.
- Blanchard S (2020) Executive collaboration in cybersecurity: Strategies for aligning security and business goals. Journal of Cybersecurity 12: 85-92.
- Kure HI, Islam S, Mouratidis H (2022) An integrated cyber security risk management framework and risk predication for the critical infrastructure protection. Neural Computing and Applications 34: 15241-15271.
- Wang T (2021) Risk-based cybersecurity strategies for aligning with business operations. International Journal of Information Security 10: 102-113.
- Salin H, Lundgren M (2022) Towards agile cybersecurity risk management for autonomous software engineering teams. Journal of Cybersecurity and Privacy 2: 276-291.
- Mukherjee T, Sharma A (2020) Cybersecurity resilience in business operations: A study on minimizing downtime and protecting customer trust. Business Security Review 12: 145-160.
- Gomez R, Patiño M (2019) Business continuity in the digital age: The integration of cybersecurity and operational Journal of Business and Technology 45: 112-128.
- Kumar N, Singh P (2020) Aligning business strategies with cybersecurity resilience: A focus on disaster recovery and business continuity planning. Global Management Review 36: 91-108.
- Majumdar S (2018) Building resilient organizations: Cybersecurity frameworks for effective disaster recovery. Journal of Information Systems 23: 34-50.
- Campbell R (2020) Cybersecurity and compliance: Bridging the gap for business success. Wiley.
- Walker P, Caldwell H (2019) GDPR and its global implications for data privacy and cybersecurity. Routledge.
- Turner S, Martin L (2020) Data privacy regulations and their impact on business operations: Compliance as a competitive advantage. Journal of Business Law 37: 255-275.
- Chapple M (2019) Information security governance and risk management: Building a robust compliance Pearson.
- Lee J, Norton A (2021) Automating compliance for the modern enterprise: Leveraging tools for efficient security management. Springer.
- Adama HE, Popoola OA, Okeke CD, Akinoso AE (2024) Economic theory and practical impacts of digital transformation in supply chain optimization. International Journal of Advanced Economics 6: 95-107.
- Wallis T (2023) How can we design a socio-technical, interorganizational response to ensure better cybersecurity for critical infrastructure?.
- Jones D, Walters L (2020) The impact of threat intelligence on business decision-making. Cybersecurity Review 11: 48-55.
- Thompson R (2019) The role of technology in modern threat intelligence. Journal of Cybersecurity & Innovation 2: 34-40.
- O Connor S (2021) Leveraging advanced threat intelligence to strengthen business resilience. Journal of Cybersecurity Innovation 3: 14-23.
- Gill A (2018) Developing A Real-Time Electronic Funds Transfer System for Credit Unions. International Journal of Advanced Research in Engineering and Technology 9: 162-184.
- Johansen A, Khalid M (2020) Artificial intelligence in cybersecurity: Enhancing business continuity through intelligent threat detection. International Journal of Cybersecurity Research 14: 51-67.
- Nyati S (2018) Transforming telematics in fleet management: Innovations in asset tracking, efficiency, and communication. International Journal of Science and Research 7: 1804-1810.
- Patel V, Sharma K, Liu Z (2021) Artificial Intelligence and Cybersecurity Defending Against Adversarial International Journal of Cyber Research 9: 50-62.
- Smith R, Jones D (2019) Bridging the Communication Gap between Cybersecurity and Business Leaders. Journal of Information Systems 10: 87-105.
- Yuan P (2020) AI and automation in cybersecurity risk management: A new era of proactive defense. Journal of Information Technology and Security 18: 62-75.

