Enhancing Salesforce Security: Employing Artificial Intelligence and Automation for Strong Protection
© 2022 Sandhya Rani Koppanathi, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Abstract
ABSTRACT
In today's digital age, businesses generally depend heavily on cloud-based platforms like Salesforce to manage client information and handle their regular activities. So, as the usage of these platforms grows, it also becomes necessary to implement increasingly sophisticated security measures in order to guard against attack from hackers. Such traditional protocols do not present a complete solution when it comes to contending with the many-sided nature of modern attacks. This paper looks at how AI and automation are integrated with Salesforce environments. Even in these circumstances, businesses can enhance their defenses against data breaches, unauthorized access, and insider threats by means of AI-driven anomaly analysis, automated incident response systems and threat detection capabilities. This paper shows case studies and practical implementations of AI and automation in pointing to exceptional vulnerabilities, automating security operations and adhering to regulatory standards. The paper intends to give direction for future Salesforce security, highlighting the importance of AI and automation in safeguarding privacy and protecting customer trust.
Introduction
Overview of Salesforce Challenges in Security and Role of AI: Salesforce is a leading customer relationship management (CRM) platform, which revolutionizes how businesses record data and interact with customers. Today, Salesforce has an umbrella which helps corporations with sales, service, marketing and application development all under one roof. However, as a result of the huge volume of individual data for every customer put into it by corporate companies and banks, that platform increasingly become targeted by cybercriminals who are seeking opportunities.
Issue with security is one of the major problems among salesforce users. With the continual change in threats to things like phishing attacks, insider threat detection, data breaches and non-compliance it just means that using old fashioned ways does not provide enough assurance that your accounts are being protected adequately from these risks by themselves. A strong security framework to tackle this challenge has never been in greater demand.
In the world of cybersecurity, Artificial Intelligence (AI) and automation emerged as game changers for their potential to greatly expand what existing human response teams can achieve. You can utilize it for real-time threat detection and anomaly analysis creating AI-driven security solutions with automated incident response powers. Using machine learning algorithms, AI processes large data sets to uncover characteristics of malicious activities that serve as red flags for the infrastructure, facilitating threat mitigation in advance.
The combination of automation and AI helps to automate security workflows that are time-consuming for IT teams. Complex incidents are easily detected, security policies can be enforced and compliance to industry standards is automatic with automation streams. AI and automation together act as a proactive defense that significantly increases the security of Salesforce environments thus protect businesses from unauthorized access to their critical data.
Salesforce Security
Salesforce Security Features and Limitations to Date Salesforce provides users multiple security features in order secure their data means they can avail all the compliance related laws. These include but are not limited to:
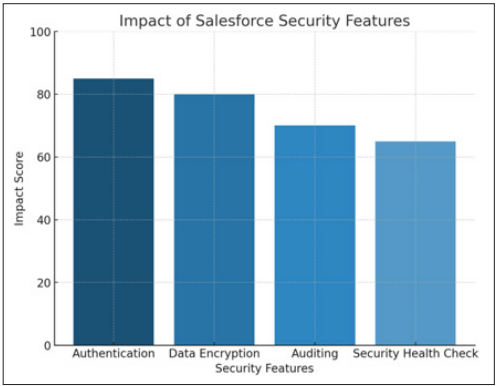
Figure 1: Impact of Salesforce Security Features
Authentication & Access Control: Salesforce has multiple authentication methods available like Single sign-on (SSO), Multi- factor authentication (MFA) and OAuth. Access Control - This ensures the appropriate role-based rights.
Data Encryption: Salesforce provides data encryption which protects the data at rest and in flight, securing information against any unauthorized access.
Auditing and Monitoring: Salesforce records user operations and system events, enabling organizations to better track access patterns thus identifying any irregularities.
Security Health Check: This tool measures company security settings and gives recommendation that can improve the security.
This sounds complex, but these are the basics and may not be enough if new threats or a more sophisticated attacker targets the system. To sufficiently safeguard the Salesforce environment, organizations need to employ more advanced security solutions.
Threats and Vulnerabilities in Salesforce
Salesforce has a lot of security threats that can bring about the loss of confidentiality, integrity and availability of its data. A few common threats and vulnerabilities are as follows:
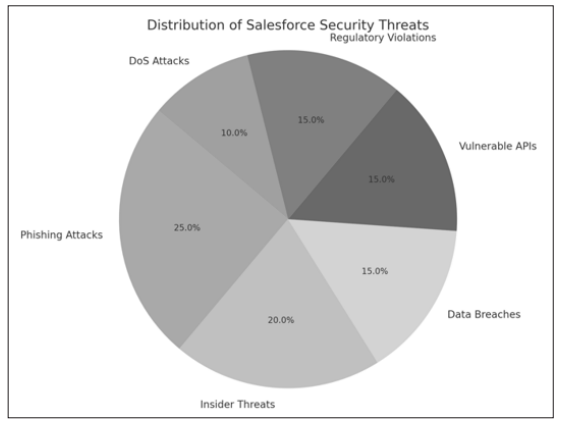
Figure 2: Distribution of Salesforce Security Threats
Phishing Attacks: Hackers get hold of Salesforce users with their email in order to rob the Login password which has been stolen. Once they have done that, the phishers can access sensitive data. Insider Threats: Employees, or contract workers who have proper access to Salesforce, might either intentionally or accidentally misuse what they're allowed to see or know to gain or disclose sensitive information.
Data Breaches: Weak passwords, misconfigured security settings, or unpatched vulnerabilities can allow unauthorized access to Salesforce data. Data breaches result.
Vulnerable APIs: Attacks on Salesforce APIs can let attackers alter data, make unauthorized transactions, or cause service interruptions.
Regulatory Violations: Certain regulatory violations as GDPR or HIPAA, should they occur, carry heavy financial penalties and harm the company's reputation.
Denial of Service (DoS) Attacks: DoS attacks can oversaturate and bring down Salesforce services, making them unavailable to legitimate users while disrupting business operations. So as to combat these threats, organizations must be proactive, adopting advanced technology and strategic security policies.
Security Enhancements Making use of AI Technology Threat Detection and Prevention: AI-driven security solutions offer advanced techniques for detecting and preventing threats in Salesforce environments. These technologies leverage machine learning algorithms to analyze large amounts of data and identify where security problems might lie.
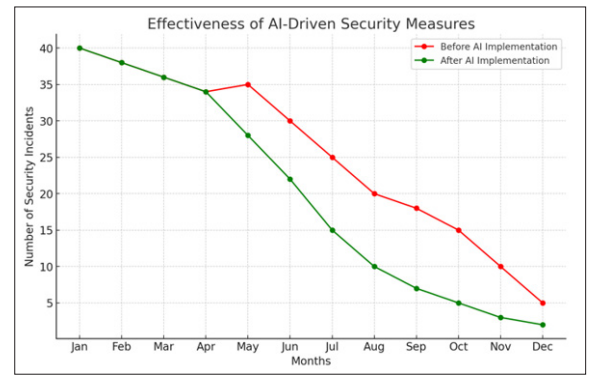
Figure 3: Effectiveness of AI-Driven Security Measures
Continuous Threat Analysis: AI systems in the Salesforce world are always on the watch, looking for what users do and how they access data. Patterns that deviate from expected ones they investigate.
Pattern Recognition: Machine learning algorithms learn how to distinguish patterns that are typical of the known threats, enabling them to anticipate possible attacks and respond early.
Adaptive Leaning: By learning from earlier incidents, AI systems can adapt to new threats. This improves their ability to detect and prevent future attacks.
Risk Assessment Automation: AI strengthens the business risk assessment process. AI can automate the risk assessment progress, gauging the potential impact of security threats and suggesting measures for prevention.
By using AI for detecting and preventing threats, companies can heighten their defense of Salesforce data from illegal acts as well as break-ins.
Anomaly Detection and Behavioral Analysis
Anomaly discovery and behavioral interpretation are key technologies of AI security systems that help organizations identifying abnormal activities that spell a threat to security:
- User Behavior Analytics: In analyzing user behavior, AI systems can establish a baseline of typical Differing from this can send out warnings--for instance if there Is a singly unusual login time or if people suddenly have access to strips.
- Anomaly Detection Algorithms: Advanced algorithms for detecting out-of-the-ordinary can pick up on changes in network traffic, the manner that data is being treated and patterns of actions that Salesforce users make which point to possible threats.
- Insider Threat Detection: By looking at user activities, AI can identify insider threats: data leakage or unauthorized
- FraudDetection: AI systems can detect fraudulent activities,
e.g. unauthorized transactions or manipulation of financial data, by analyzing patterns and discrepancies.
Predictive Analytics for Vulnerability Management Predictive analytics give organizations the ability to anticipate potential security vulnerabilities and address them before they are exploited:
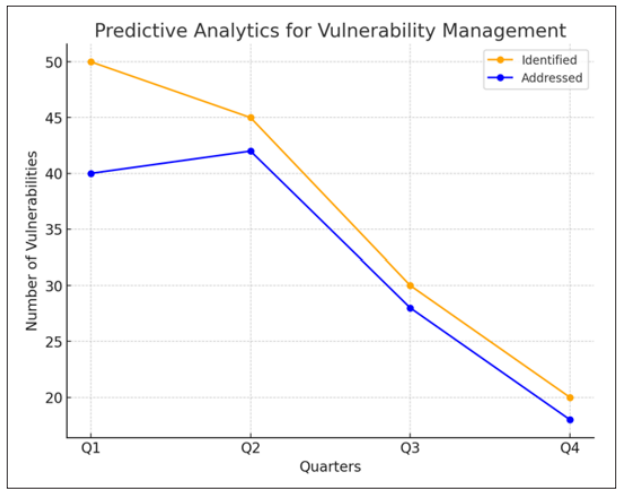
Figure 4: Predictive Analytics for Vulnerability Management
Vulnerability Scanning: AI-driven scanning tools for vulnerabilities can identify faults in Salesforce settings, suggesting patches and improving security.
Predictive Threat Modeling: Possible attack scenarios can be modelled by AI systems, giving organizations a tool for proactively strengthening their defense against probable threats.
Risk Forecasting: Based on historical data, predictive analytics can gauge the likelihood of future threats – this helps businesses choose where they should focus their security efforts.
Security Posture Assessment: AI can assess an organization’s general security posture, pointing out areas for improvement and advising on strategic security planning.
With AI for predictive analysis, the company could strengthen its strategy for vulnerability management, and this will lower the chances of a security crack.
Automatic Incident Response in Salesforce Security Automated Incident Response: Automation can streamline the process for reacting to an incident, greatly reducing the time and effort that has to go into responding to a security threat.
Automated Alerts and Notifications: Important thing security incidents will all signals and alert: It causes alarms to go off and IT inspectors are on-scene in a hurry.
Response Integration: Automated orchestration of response activity can isolate affected systems and stop illegal access, and even begin investigation.
Integration with Security Tools: Automation enables seamless integration with security tools like firewalls and intrusion detection systems, thus enhancing response capabilities.
Auto-remediation: Security problems are quickly fixed by automatic scripting, such as reloading configurations to standard or rolling patches back.
Workflow Automation for Security Management Automation can make security management more efficient by making workflows electronic and adhering to the letter of security policies:
- Policy Enforcement: Automated workflows enforce security policies--such as password complexity requirements and access controls--system-wide in Salesforce environments.
- AccessManagement: Automation tools can manage who can get in and do what, thus ensuring that permissions are given and withdrawn in line with established policy.
- Audit and Compliance Reporting: Automated reporting tools crank out compliance reports that broaden the channel to include regulatory agencies and auditors, thus always ensuring adherence with industry regulations.
- SecurityTrainingandAwareness: Automated systems can deliver security training and awareness programs to staff members, reducing dependence on humans who are prone for errors of judgment.
Integration with Security Information and Event Management (SIEM) Systems
Integration with SIEM systems augments Salesforce security by affording a more comprehensive view and enhanced insight into potential threats:
- Centralized Security Monitoring: SIEM systems can pool data from security systems and Salesforce, making for united watching and analysis.
- Correlated Threat Intelligence: SIEM tools can correlate security events across different systems, which can provide insight into complex threats and attack vectors.
SIEM systems apply AI and machine learning to discover advanced threats, including both zero-day attacks and sophisticated malware. SIEM solutions allow for swift incident investigation in extensive detail. They report on the impact of security events. The integration of Salesforce with SIEM systems can contribute to an enterprise's security posture, enhancing its ability to respond to threats in real time.
Case Studies and Applications in Real Life AI and Automation for Financial Services
The financial services industry is a prime target for cyber criminals, where the sensitive nature of financial data makes it especially vulnerable. AI and automation help to strengthen the security of Salesforce in financial institutions in numerous ways:
- Detection of Fraud and Prevention: Financial institutions can use AI algorithms to analyze transaction patterns and detect deviations. By integrating AI with Salesforce, these institutions can guard against unauthorized transactions, identity theft and account takeovers in a way that's entirely automated. Suspicious activities recorded by AI systems act as a first line of defense - potential fraud is nipped in the bud before it can spread to customers or threaten the organization's operational safety.
- Compliance with Financial Regulations: Automation makes the companies compliant with financial regulations like PCI DSS and SOX by forcing security policies automagically as well and automatically generating audit reports. AI-based tools that run in the background and look for Salesforce environments out of compliance, instead automatically alerting when anomalies are found. By taking a proactive approach, financial institutions can ensure they are compliant with changing regulatory requirements and do not face the alternative which results in expensive fines as well as reputational damage.
- Threat Sharing: Financial institutions can employ AI to consolidate and analyze threat intelligence originating from every source imaginable - cybersecurity vendors, government security agencies, or trade bodies. This can be meshed into Salesforce for meaningful real-time insight on new threats and Automation fosters widespread distribution of threat intelligence throughout a corporation, which allows all elements of the organization to respond in common to any risks that might arise.
Enhancing Security in Healthcare Data Management Organizations in healthcare use Salesforce to keep patient data and run operations. Machine learning and automation enhance the security of confidential health information as follows:
- HIPAA Compliance: Automation enforces HIPAA compliance by monitoring data flow logs and managing access controls. Artificial Intelligence (AI)-driven systems can scan a Salesforce setup to make sure that the organization follows all best practices for handling information which are mandated by This not only means some way or another encryption, limited admissions and punctual reporting of safety incidents also its about making sure there is no open gap.
- Patient Data Protection: Patient data can be protected from getting into the wrong hands and from leaking both by safe management tools all AI-driven encryption methods these systems pick up on access patterns that are unusual and attempts to access sensitive information without proper authority. Automated alerts then tell security teams about potential leaks, so they can move quickly to protect patient
- Anomaly Detection for Insider Threats: healthcare organizations frequently face the threat of collusion from within the camp employees who abuse their access to patient AI systems can check the behavior of users for signs they might have passed information out with recourse to former insiders or otherwise. Machine learning can impose harsh access rules, allowing employees to read or edit of knowledge in their current dopamine levels.
- RetailSector: Security of Customer Data And Transactions: Retail companies using Salesforce to coordinate customer contacts and sales also undergo a round of improvements when it comes to the security of customer data:
- PCICompliance: Automation enforces PCI DSS compliance by both watching for controls and monitoring payment transactions. AI-driven systems can identify potential compliance breaches automatically, such as unencrypted payment reporting data or attempts at entering that are not authorized. In this way companies work hard to protect the data of their customers on an ongoing basis while also maintaining trust.
- Real-time Fraud Detection: AI systems are capable of spotting fraudulent transactions through methods such as credit card fraud and account takeovers, which analyze a user's work patterns itself. Retailers can use Machine Learning algorithms in order to find behaviors which may be worth careful looking into, such as there being a number of immediate buys from different places or even people all at once.
- CustomerDataPrivacy: AI-driven privacy controls prevent end-user’s data from being accessed or admins from siphoning it off. This is entrusted entirely to computers, the decisions made by themselves also involve computer automation; only qualified personnel can read and store confidential customer
Challenges and Best Practices
Addressing AI Bias and Ethics: As well as being a powerful tool for securing information, AI creates new problems for security related to bias and ethics.
AI Bias: AI systems can be biased in threat detection and decision- making, therefore causing false positives/negatives. For example, an AI model trained on biased data might cast certain behaviors as suspicious simply because they come from a particular race, gender or nationality. Firms need to be very careful about watching the output of their AI and ensure that it comes from a variety of sources in order to limit bias.
Ethical Considerations: When organizations turn to AI for security, they must also consider the ethical consequences. Systems should be non-invasive and maintain a respectful distance from human rights violations. AI solutions need to give reasons for their decisions and industry organizations have to explain clearly how AI driven decisions are made and data is handled.
Transparency and Accountability: AI systems ought to be open and responsible, offering clear explanations for policing operations. Companies should put in place ways of reviewing decisions made by AI and holding them beyond reproach if necessary, so as to avoid causing any harm whatsoever.
Ensuring Data Privacy and Compliance: Businesses need to take care that the data they use does not contravene privacy regulations or international law otherwise most likely end up losing thousands in legal fees for breach lawsuits.
Data-protection Regulations: AI-driven security solutions must comply with applicable data-protection rules like GDPR and CCPA. This involves managing data collection, processing and storage so that it complies with all legal standards – while making everything clear for the customer just how their information is being handled.
Privacy by Design: AI systems should apply privacy by design principles by building privacy into their architecture from the start. Organizations should also adopt rigorous encryption methods, carefully restrict access to data, and anonymize information in sensitive areas to protect it from prying eyes.
Access Controls: It is vital to have strong protections around access for sensitive data or else unauthorized persons could bring on fatal hacks without you noticing for weeks. Automation can enforce strict access policies and make sure that only authorized personnel are allowed anywhere near certain Salesforce environments or blocks of data.
Best Practice for Implementing AI and Automation: Organizations should adhere to best practices when implementing AI and automation for Salesforce security.
Continuous Monitoring and Assessment: It is essential to continually monitor and assess the effectiveness and reliability of AI systems. Organizations should regularly monitor models for potential biases or errors in calculations, correcting systems as new threats appear.
Integration with Existing Security Frameworks: AI and automation should be integrated with existing security frameworks to strengthen overall security posture. By tying AI-driven insights together with traditional security means, organizations can mount a comprehensive defense against current and emerging threats alike.
Training and Awareness: Employee training and awareness courses are essential (or staff won't obey our safety regulations). Organizations need to teach employees about what role AI and automation play in protecting our ocular world axis from marauders, as well as passing on the nitty gritty of how to keep a secure Salesforce environment.
Scalability and Adaptability: AI and automation solutions must be scalable and adaptable to the crime problems of the future. Organizations should build systems that can grow in step with their business; more importantly, change where necessary to adapt to an evolving threat landscape.
Future of AI and Security Automation
Emerging Trends: Next-Generation AI & Security Automation is designed for this era of accelerating cybersecurity. As automation technologies evolve over time, any future direction for AI and security automation in the Salesforce environment will closely mirror what we are already seeing today in these two trends.
AI-Powered Predictive Security: In an increasingly complex world, AI systems can predict potential security threats and take corrective action. Predictive security solutions analyze what has happened in the past and look for patterns that indicate where future risks may arise, enabling an organization to take preventive measures before something goes wrong.
Automated Threat Hunting: Automation has made for more efficient threat hunting (finding vulnerabilities and potential attack vectors) by means of automated scanning. This reduces the burden on security teams and speeds up identification and mitigation of threats.
AI and IoT Integration: While IoT has become increasingly pervasive AI driven security solutions are now in development to protect interconnected devices and systems. Integrating AI into IoT security helps spot threats and respond efforts aimed specifically at destroying IoT networks.
Behavioral Biometrics: Behavioral biometrics employs AI systems to analyze such behaviors as typing patterns and mouse movements in order to authenticate the user and spot anomalies. This approach improves authentication and makes fraud detection easier in Salesforce environments.
The Evolution of Cyber Threats and Defense Mechanisms The cybersecurity landscape is ever-changing, where organizations need to stay one step ahead of emerging threats if they are to protect their Salesforce environments well:
- Advanced Persistent Threats: These are sophisticated attacks that home in on specific organizations in order to gain access and control of confidential data over time. AI- style solutions can be used to detect and stem the impacts of one such type of APT by looking at network traffic for signs continued threat.
- Zero-DayExploits: Zero-day exploits hit vulnerabilities that have not yet been patched or publicly With AI we may be able find these signs of a zero-day attack in anomaly detection mechanisms and notify security teams accordingly.
- Ransomware Attacks: Ransomware still constitutes a significant threat, as criminals encrypt systems and ask for payments in return for the necessary decryption keys. AI systems can identify patterns of ransomware and prevent encryption attempts to protect critical documents.
- Insider Threats: Insider threats continue to loom large over companies; employees or contractors having authorized access may misuse their privileges. AI-driven behavior analysis can discern suspicious insider activities and deal with them before they escalate.
Salesforce Security in the Age of AI and Automation
With the evolution of an ever-changing digital landscape, cyber threats for cloud-based platforms like Salesforce have also cranked up their game. In the battle against digital dangers, AI and automation have become indispensable weapons that enable companies to acquire modern-day security solutions, proactively protecting their Salesforce environments with ease.
IT teams need an AI-driven solution that can monitor zero-day threats, analyses advanced threat activity and apply predictive analytics for by detecting the signals in security frameworks. Plus, automation further augments these powers by simplifying incident response actions and the reinforcement of security policies to guarantee industry standard compliance.
Leveraging AI and automation can help organizations strengthen their security foundation, safeguard data assets and win customer confidence. Not only do these technologies provide instant security benefits, but they also enable building a more secure and adaptable security framework going forward.
Conclusion
AI and automation in Salesforce security is more than just a nice addition; it is crucial given the ever-changing threat landscape of today. With cyber threats growing ever more sophisticated and prolific, relying solely on traditional security methods is not enough to protect critical data or uphold customer confidence.
AI and automation deliver compelling defense as they operate much faster, more accurately, and flexibly than manual processes. Enterprises need to understand the potential benefits of these technologies and organizations have a stake in deploying it, as part of their comprehensive defense mechanism against various types of cyber threats.
Using best practices, avoiding challenges associated with AI bias and ethics, as well to enhance security systems constantly will help organizations create a secure Salesforce environment for present needs while staying compliant in the face of potential future disruptions. We are in the time of AI-powered security, which will revolutionize how organizations secure their digital assets.
References
- Chen J, Patel R (2022) Automated Security Management in Salesforce: Integrating AI and SIEM Systems. Journal of Cybersecurity and Privacy 3: 150-162.
- Kadam A (2019) Enhancing Software Security for Salesforce International Journal for Research in Applied Science and Engineering Technology. https://doi.org/10.22214/ijraset.2019.3401.
- Pullig C, Maxham J, Hair J (2002) Salesforce automation systems: an exploratory examination of organizational factors associated with effective implementation and salesforce productivity. Journal of Business Research 55: 401-415.
- Das R, Sandhane R (2021) Artificial Intelligence in Cyber Security. Journal of Physics: Conference https://doi.org/10.1088/1742-6596/1964/4/042072.
- Trifonov R, Manolov S, Tsochev G (2020) Automation of Cyber Security Incident Handling through Artificial Intelligence Methods. https://doi.org/10.37394/23205.2020.19.5.
- Picareta G, Weissheim E, Klöhn M (2021) Intelligent Applications in the Modern Sales https://doi.org/10.1108/978-1-83909-694-520211003.
- Lins S, Pandl K, Teigeler H, Thiebes S, Bayer C, et (2021) Artificial Intelligence as a Service. Business & Information Systems Engineering 63: 441-456.
- Li J (2018) Cyber security meets artificial intelligence: a survey. Frontiers of Information Technology & Electronic Engineering 19: 1462-1474.
- Dhashanamoorthi B (2021) Artificial Intelligence in combating cyber threats in Banking and Financial International Journal of Science and Research Archive. https:// doi.org/10.30574/ijsra.2023.10.2.0948.
- Susanto H, Yie L, Rosiyadi D, Basuki A, Setiana D (2021) Data Security for Connected Governments and Web 2.0 and Cloud Technologies for Implementing Connected Government. 229-251.

