Data Masking for GDPR Compliance in Financial Transactions
© 2024 Pooja Badgujar, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Abstract
Projecting future trends in financial technology, this paper will draw on insights and experiences from Wells Fargo to outline potential developments in the field. It will discuss emerging technologies, anticipated challenges, and strategic approaches for leveraging technology to drive innovation in banking. The paper will also reflect on the author's contributions to the field and outline future research and development directions. The GDPR mandates stringent measures to protect personal data, imposing obligations on organizations to ensure the lawful and transparent processing of such information. Within the financial realm, where transactions involve a plethora of sensitive data points, adhering to GDPR regulations becomes paramount. Data masking serves as a vital mechanism in this endeavor, facilitating the anonymization or pseudonymization of sensitive data elements while preserving their utility and integrity. By anonymizing or pseudonymizing sensitive information, data masking mitigates the risk of unauthorized access or disclosure, thus safeguarding customer privacy. This proactive approach not only aligns with GDPR principles but also fosters trust and confidence among stakeholders. Moreover, data masking enables organizations to strike a delicate balance between regulatory compliance and operational efficiency, ensuring that essential business functions remain unhindered.
Introduction
Unstructured data, encompassing various forms such as text, images, and videos, represents a substantial fraction of contemporary data volumes [1]. Despite its ubiquity, extracting actionable insights from unstructured data poses considerable challenges owing to its diverse composition and absence of predetermined organization. In this paper, we aim to elucidate the multifaceted challenges inherent in the analysis of unstructured data while delineating strategies and tools devised to surmount these obstacles effectively.
The inherent heterogeneity of unstructured data presents a formidable hurdle in data analysis endeavors. Unlike structured data, which adheres to predefined schemas and formats, unstructured data lacks uniformity, rendering traditional analytical techniques inadequate. Additionally, the sheer volume and complexity of unstructured data further compound the analytical complexities, necessitating novel approaches for data interpretation and extraction of meaningful insights.
Furthermore, the absence of a predetermined structure in unstructured data exacerbates the challenge of data interpretation and analysis. Traditional analytical methodologies, tailored for structured data, are ill-suited for the nuanced characteristics of unstructured data, thereby impeding the extraction of actionable insights[2]. Consequently, organizations grapple with the formidable task of unraveling the latent value embedded within unstructured data while contending with its inherent intricacies and idiosyncrasies.
In light of these challenges, it becomes imperative to explore innovative techniques and tools tailored for the analysis of unstructured data. By harnessing advanced methodologies such as Natural Language Processing (NLP), image analysis, and sentiment analysis, organizations can unravel hidden patterns and trends within unstructured data, thereby unlocking its latent value [3]. Moreover, the advent of sophisticated analytics platforms and machine learning algorithms offers promising avenues for extracting actionable insights from unstructured data, thereby enabling organizations to derive strategic value from this vast and heterogeneous data landscape.
Understanding GDPR Compliance in Financial Transactions Understanding GDPR compliance in financial transactions requires a comprehensive grasp of the regulations and their implications within this specific context. The General Data Protection Regulation (GDPR) mandates stringent requirements for the handling and processing of personal data, imposing obligations on organizations involved in financial transactions. Central to GDPR compliance are key principles such as data minimization, purpose limitation, and data protection by design and by default.

An Image on GDPR Compliance as a Showcase
Data minimization entails the collection and retention of only the necessary personal data required for a specific purpose, thereby limiting the scope of data processing and minimizing privacy risks. Purpose limitation dictates that personal data should be collected for specified, explicit, and legitimate purposes, ensuring that data processing activities remain aligned with the intended objectives. Additionally, GDPR mandates the implementation of data protection measures by design and by default, necessitating the integration of privacy safeguards into the development of systems and processes from the outset.
Financial institutions encounter various challenges in achieving GDPR compliance within transactional data environments. These challenges stem from the complexity of financial transactions, which involve the exchange of sensitive personal data such as account numbers, transaction details, and financial histories [4]. Ensuring compliance while maintaining the seamless flow of transactional data poses significant technical and operational challenges for financial institutions. Additionally, the need to balance GDPR requirements with regulatory obligations, industry standards, and business objectives further complicates the compliance landscape.
Data Masking Techniques for GDPR Compliance
Data Masking Techniques for GDPR Compliance in Financial Transactions
Data masking techniques are essential tools in ensuring GDPR compliance within financial transactions, playing a crucial role in safeguarding sensitive data while facilitating seamless data exchange and analysis. Among these techniques, anonymization stands out as a fundamental approach for obscuring Personally Identifiable Information (PII) in financial transactions.
Anonymization Methods: Randomization: Randomization is a key anonymization method that involves replacing original data values with randomly generated values. By introducing randomness into the data, randomization makes it challenging to identify individual data points, thereby protecting the privacy of individuals involved in financial transactions.
Substitution: Substitution is another effective anonymization technique wherein sensitive data is replaced with fictitious or generic values [5]. By substituting actual data with fictional counterparts, substitution helps to conceal the true identity of individuals and mitigate the risk of unauthorized access or disclosure.
Shuffling: Shuffling involves rearranging the order of data elements within a dataset, thereby obfuscating any identifiable patterns or sequences [1]. By shuffling the data, sensitive information becomes more difficult to decipher, enhancing the overall privacy protection within financial transactions.
Application in Financial Transactions: In financial transactions, anonymization techniques such as randomization, substitution, and shuffling are applied to various data elements containing PII. These techniques ensure that sensitive information, such as customer names, account numbers, and transaction details, is effectively masked to prevent unauthorized access or misuse.
Benefits of Anonymization
The anonymization of sensitive data in financial transactions offers numerous benefits, including enhanced privacy protection, regulatory compliance, and risk mitigation. By anonymizing PII, financial institutions can demonstrate their commitment to GDPR compliance while fostering trust and confidence among customers and stakeholders.
On the other hand, pseudonymization methods are employed to replace identifiable data with pseudonyms or tokens, thereby further enhancing data privacy and protection. Pseudonymization techniques include tokenization, hashing, and encryption, each offering unique advantages in preserving data integrity while pseudonymizing sensitive information. Tokenization involves replacing sensitive data with unique tokens or identifiers, ensuring that the original data cannot be easily deciphered [5]. Hashing converts sensitive data into irreversible hashed values, ensuring that the original data remains obscured while maintaining consistency for verification purposes. Encryption transforms sensitive data into ciphertext using cryptographic algorithms, requiring decryption keys to restore the original data, thus providing an additional layer of security.
By leveraging anonymization and pseudonymization techniques, financial institutions can mitigate privacy risks associated with GDPR compliance while preserving the usability and integrity of transactional data. These techniques enable organizations to strike a balance between data protection and operational efficiency, ensuring compliance with regulatory requirements while facilitating legitimate data processing activities. Ultimately, the effective implementation of data masking techniques is essential for financial institutions to maintain customer trust, uphold regulatory standards, and safeguard sensitive data in today's digital landscape.
Implementing Data Masking in Financial Transactions Implementing data masking techniques in financial transactions involves careful integration into existing transactional data workflows while balancing the imperatives of GDPR compliance with operational efficiency and data usability. A strategic approach is essential to ensure seamless integration and effectiveness.
A fundamental strategy in ensuring compliance with GDPR regulations in financial transactions involves the identification of sensitive data elements within transactional datasets and prioritizing them for masking. By directing attention to high-risk data fields such as Personally Identifiable Information (PII) and financial identifiers, organizations can effectively mitigate privacy risks while minimizing disruptions to core business processes [2]. This targeted approach allows for the focused application of data masking techniques, thereby safeguarding sensitive information without unduly impeding operational efficiency.
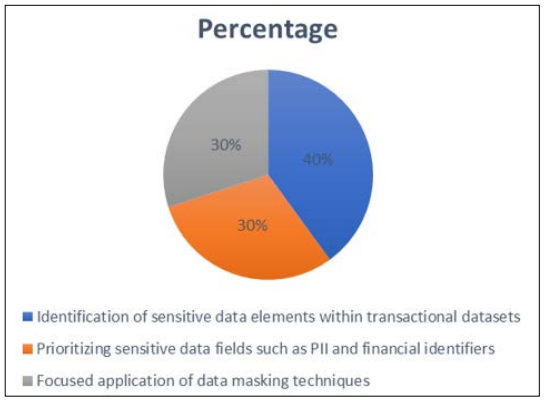
This pie chart above effectively visualizes the distribution of strategies involved in implementing data masking techniques in financial transactions. It highlights the emphasis on identifying sensitive data elements, prioritizing high-risk fields, and applying masking techniques strategically to ensure GDPR compliance while maintaining operational efficiency Moreover, organizations should adopt a multifaceted approach to data masking, employing a combination of anonymization and pseudonymization techniques tailored to the specific requirements of their transactional data environment. Anonymization methods such as randomization, substitution, and shuffling serve to obscure identifiable details, rendering sensitive data elements unidentifiable and thus compliant with GDPR mandates [5]. Conversely, pseudonymization techniques such as tokenization, hashing, and encryption replace identifiable data with pseudonyms or tokens, preserving data integrity while ensuring privacy protection.
By integrating these complementary approaches, organizations can effectively balance the imperatives of regulatory compliance and operational functionality within their transactional data workflows. This strategic alignment enables the seamless execution of data masking initiatives, facilitating the attainment of GDPR compliance objectives while safeguarding sensitive information throughout the transactional lifecycle [3]. In essence, the judicious application of data masking techniques tailored to the unique characteristics of transactional datasets constitutes a cornerstone of GDPR compliance efforts in the financial sector, ensuring the harmonization of privacy protection and operational efficacy in tandem.
Considerations for balancing GDPR compliance requirements with operational efficiency and data usability are paramount. Organizations must strike a delicate balance between data protection and data utility, ensuring that masked data remains usable for legitimate business purposes while safeguarding customer privacy [5]. This involves careful planning and collaboration between data privacy experts, compliance teams, and business stakeholders to establish clear policies and procedures for data masking.
Furthermore, organizations should leverage advanced technologies and tools to automate the data masking process and streamline compliance efforts. Robust data masking solutions offer features such as dynamic data masking, tokenization, and data de- identification, enabling organizations to efficiently anonymize or pseudonymize sensitive data without compromising operational efficiency. By adopting a proactive approach to data masking and compliance, organizations can effectively navigate the complexities of GDPR regulations while maintaining the integrity and usability of their transactional data.
Case Study: Leading Bank Implements Anonymization Techniques for GDPR Compliance A prominent bank implemented anonymization techniques to ensure GDPR compliance while handling transactional data. By employing sophisticated data masking algorithms, the bank obscured Personally Identifiable Information (PII) such as customer names, account numbers, and transaction details [4]. This approach enabled the bank to anonymize sensitive data elements within financial transactions while preserving data integrity and usability. As a result, the bank achieved GDPR compliance by safeguarding customer privacy without compromising operational efficiency.
The above is a Data anonymization Case Study Visualization
Case Study: Financial Services Firm Adopts Pseudonymization Strategies to Protect Data Privacy A financial services firm adopted pseudonymization strategies to enhance data privacy and comply with GDPR regulations. Leveraging advanced pseudonymization techniques such as tokenization and encryption, the firm replaced identifiable data elements with pseudonyms or encrypted tokens within transactional data sets. This approach enabled the firm to protect sensitive customer information while maintaining the usability of data for analysis and reporting purposes. By implementing robust pseudonymization practices, the firm successfully achieved GDPR compliance and instilled trust among customers regarding data privacy and security.
Case Study: Insurance Company Integrates Data Masking Solutions for Regulatory Compliance An insurance company integrated data masking solutions into its transaction processing systems to address GDPR compliance requirements. By incorporating data masking techniques such as randomization and substitution, the company obscured sensitive data attributes in financial transactions, including policyholder information and claims data [1]. This proactive approach enabled the company to meet GDPR obligations by anonymizing personal data while ensuring the uninterrupted flow of business operations. As a result, the insurance company demonstrated its commitment to protecting customer privacy and regulatory compliance, enhancing trust and confidence among stakeholders.
Challenges and Best Practices
When implementing data masking for GDPR compliance in financial transactions, organizations commonly encounter several challenges and pitfalls. One prevalent challenge is the complexity of transactional data environments, which often contain a multitude of interconnected systems and databases housing sensitive information. Additionally, ensuring data masking techniques adequately anonymize or pseudonymize data without compromising its integrity or usability presents a significant challenge[5]. Moreover, maintaining compliance with evolving GDPR regulations amidst changing business requirements and technological advancements poses an ongoing challenge for organizations.
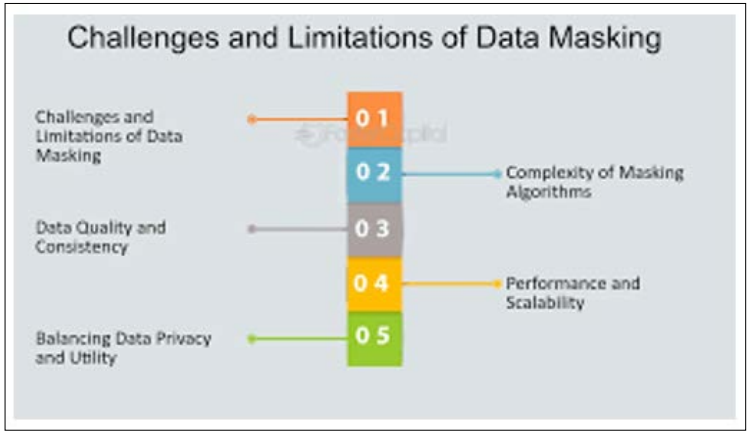
To address these challenges effectively, organizations can adopt best practices for selecting and implementing data masking techniques. Firstly, conducting a comprehensive assessment of data flows and identifying sensitive data elements is crucial for determining the scope of data masking requirements. Additionally, organizations should prioritize the selection of data masking techniques based on the specific characteristics of their data and compliance needs. It is imperative to employ a combination of anonymization and pseudonymization techniques tailored to the nature of the data being masked.
Furthermore, organizations should implement robust data governance practices to ensure proper documentation, monitoring, and auditing of data masking processes. Regular assessments and reviews of data masking implementations are essential to identify and address any potential vulnerabilities or compliance gaps. Additionally, organizations should invest in employee training and awareness programs to ensure staff understand the importance of data masking for GDPR compliance and adhere to established protocols.
By adopting these best practices, organizations can navigate the challenges of implementing data masking for GDPR compliance in financial transactions effectively. By prioritizing data privacy and compliance, organizations can build trust with customers and regulators while safeguarding sensitive information in today's increasingly data-driven financial landscape.
Conclusion
In summary, data masking emerges as a vital strategy in aligning financial transactions with GDPR regulations, effectively safeguarding customer privacy while facilitating seamless data processing. Through the adept application of data masking techniques, financial institutions can navigate the intricate landscape of GDPR compliance, ensuring adherence to regulatory requirements without compromising operational efficiency or compromising data integrity.
The implementation of robust data masking protocols empowers organizations to anonymize or pseudonymize sensitive information within financial transactions, thereby mitigating privacy risks and enhancing regulatory compliance. By obscuring personally identifiable details through anonymization and substituting them with pseudonyms or tokens via pseudonymization, institutions strike a delicate balance between regulatory adherence and operational agility.
Moreover, data masking serves as a cornerstone for promoting trust and transparency in financial transactions, fostering confidence among customers and stakeholders alike. By demonstrating a commitment to safeguarding customer privacy, organizations not only fulfill their legal obligations but also cultivate long-term relationships built on trust and integrity.
Looking ahead, the continued evolution of data masking techniques promises to further enhance GDPR compliance efforts within the financial sector. As technology advances and regulatory requirements evolve, financial institutions must remain vigilant in adapting their data masking strategies to address emerging challenges and mitigate new risks effectively.
In essence, data masking emerges as an indispensable tool in the arsenal of financial institutions striving to uphold GDPR compliance standards. By embracing and refining data masking practices, organizations can navigate the regulatory landscape with confidence, ensuring the protection of customer privacy while upholding the principles of transparency and accountability in financial transactions.
References
- Savage A (2020) Every tool’s a hammer: life is what you make https://www.amazon.in/Every-Tools-Hammer-Life-What/dp/1982113472.
- Sanjay Sharma and Menon P (2024) Data privacy and GDPR https://www.wiley.com/en-in/Data+Privacy+and+GDPR+Handbook-p-9781119594192.
- Izzat Alsmadi, Chuck Easttom, Lo’ai Tawalbeh (2020) The NICE Cyber Security https://www.amazon.in/NICE-Cyber-Security-Framework-Management/dp/303041986X.
- Maniotis Spyridon (2022) Industrializing Financial Services with https://www.packtpub.com/product/industrializing-financial-services-with-devops/9781804614341.
- Chris Dotson (2023) Practical Cloud Security. https://www.oreilly.com/library/view/practical-cloud-security/9781098148164/.

