Author(s): Ouafae Elaeraj and Cherkaoui Leghris*
Now a days, the company’s information security become among a main priority. Indeed, the more the attack force on the network develops, the more it is necessary to develop the security and the network surveillance. The data is to be exchanged between the internal company network and the outside one such as Internet. It is therefore necessary to be protected against malicious intrusions into the company's network, but also to monitor the traffic inside the network in order to prevent possible internal attacks. Currently, security and reliability have become the major concerns of an individual or organization. A rule-based intrusion detection system (IDS) called Snort is an open-source software used as a network protection tool that can only detect recognized attacks. In order to detect advanced network attacks and detect fraudulent network traffic, this research paper proposes an advanced and more intelligent approach by applying machine learning. To find the best algorithm to use with Snort to improve its detection, the support vector machine (SVM) was chosen based on its accuracy. The proposed system has produced efficient detection rates versus other proposed approaches in the security intrusions detection field.
The openness of systems and their interconnection with the Internet have made attacks more and more numerous and diverse. In addition to the implementation of firewalls and authentication systems, it is nowadays necessary to implement an intrusion detection system. There are two main types of intrusion detection systems. The first type is host-based intrusion detectors (HIDS), which could analyze and monitor only the activity and information of the host on which the HIDS is installed and thus ensure only the security of the host in question. The second type consists of network intrusion detectors (NIDS), which observe and analyze network traffic, look for indicators of attacks and send alerts. The most known NIDS is SNORT, which is, an open-source software, often used as a probe. It also has an active mode that allows it, when installed on a routing device, to block any suspicious traffic. It is therefore a network intrusion detector allowing real-time analysis of traffic on a network segment.
SNORT is a free intrusion detection system (or NIDS) released under the GNU GPL. Originally written by Marty Roesch, it is currently owned by the American company Sourcefire. It is one of the most active open-source NIDS and has a large community contributing to its success. Firstly, it is open- source software that can be deployed by individuals and organizations, and it is widely used in companies. Since we are going to focus on the network security of a small or medium-sized company, we will implement a system that allows monitoring traffic and updating security rules and policies from a security manager because a small or medium-sized company may not have the means to equip itself with a "computerized information system security" department.
SNORT is a powerful Intrusion Detection System (IDS) and also an Intrusion Prevention System (IPS) that provides real-time network traffic analysis and packet logging, uses a rule-based language that combines anomaly inspection methods, protocols and signatures to detect potentially malicious activity. Using this detection system, network administrators can detect denial-of- service (DoS) attacks, distributed DoS (DDoS) attacks, common gateway interface (CGI) attacks, buffer overflows and stealth port scans. SNORT creates a series of rules that define malicious network activity, identify malicious packets, and sends alerts to users. The SNORT rule language determines what network traffic should be collected and what should happen when it detects malicious packets. This sniffing sense can be used in the same way as network sniffers and intrusion detection systems to discover malicious packets or as a complete network IPS solution that monitors network activity and detects and blocks potential attack vectors.
Snort captures packets at a point on an IP network, analyzes the resulting flow in real time, and compares the network traffic to a database of known attacks. Known attacks are listed in rule libraries maintained by several very active communities.
Snort can also be used with other compatible modules (such as GUIs, independent attack library updaters, etc.).
Snort is compatible with most OS. Windows, Mac, Linux Ubuntu, CentOS.
SNORT allows the analysis of IP type network traffic; it can be configured to operate in three modes:
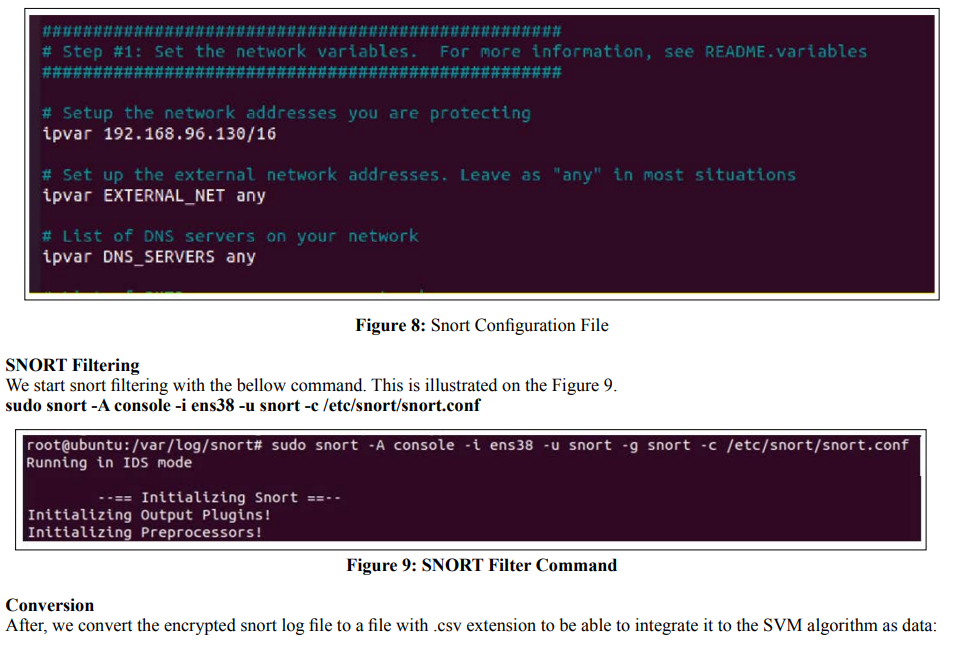
Sniffer Mode: In this mode, SNORT reads packets traveling over the network and displays them continuously on the screen; running Snort in this mode allows you to dump the data in the header and body of each packet for the screen. To start Snort so that it displays all the data in the application, enter the following: snort -vde
Mode "packet logger": In this mode, SNORT records network traffic in directories on disk, also allows thanks to its arguments interesting operations allowing to limit the logs to some criteria, like a range of IP address: snort -vde -l <path_to_journal_ directory>, -l = location of log directory.
Network Intrusion Detector Mode (NIDS): In this mode, SNORT analyzes the network traffic, compares this traffic with the rules already defined by the user and the established actions to be performed; this mode allows to make a system based on IDS that will place sensors, so network cards that we will place in peripheral networks as seen in Figure 1, so that they can analyze the incoming and outgoing flows of the network. It captures all the network traffic in real time:
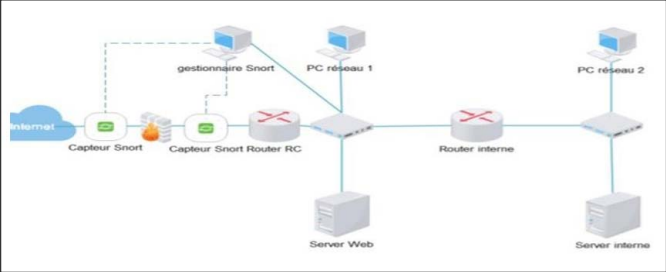
Figure 1: Operation of a NIDS
SNORT is an open-source Network Intrusion Detection System capable of real-time analysis of traffic on IP networks. SNORT uses protocol analysis and string searching in packets for attack detection. It is used to detect a variety of attacks such as port scans, common gateway interface (CGI) attacks, buffer overflows, and more.
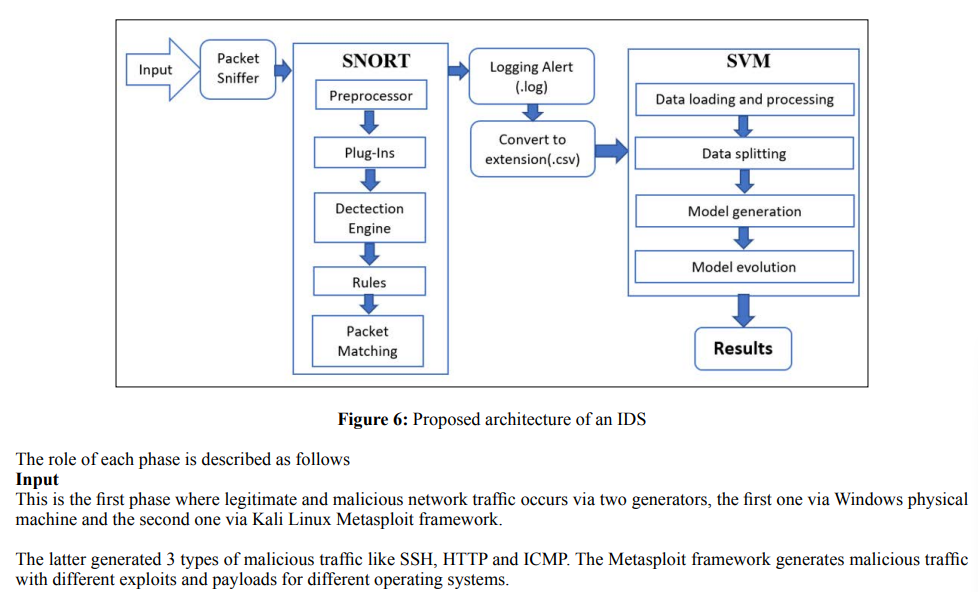
SNORT's architecture is organized in modules, consisting of four main modules: the packet decoder, the preprocessors, the detection engine, and the alerting and logging system as seen in Figure 2.
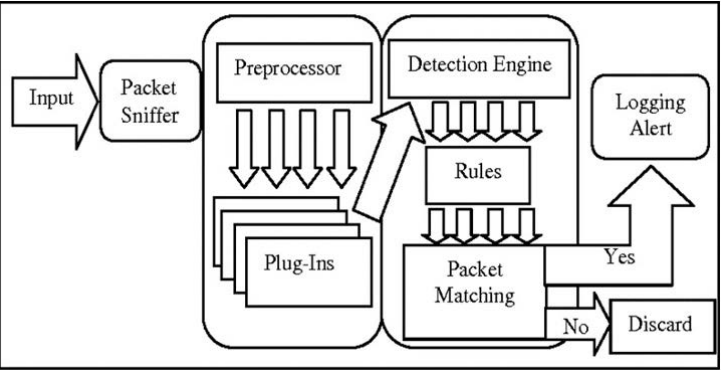
Figure 2: SNORT Architecture
The Packet Decoder: An intrusion detection system activates one or more network interfaces of the machine in promiscuous mode, this will allow it to read and analyze all the packets that pass through the communication link. SNORT uses the libpcap library to capture the frames. A packet decoder is composed of several sub-decoders which are organized by protocol (Ethernet, IP, TCP.), these decoders transform the elements of the protocols into an internal data structure;
The Preprocessors: Deals with the detection of intrusion by looking for anomalies, a preprocessor sends an alert if the packets do not respect the standards of the protocols used. A preprocessor is different from a detection rule, it is a program that aims to go into more details in the analysis of traffic. We will see through an example how preprocessors work;
Detection Engine: This is the most important part of IDS. The detection engine uses rules to detect intrusion activity. If a packet matches a rule an alert is generated. The rules are grouped into several categories in the form of files. SNORT comes with a set of predefined rules. These rules are not activated automatically, they must be activated in the snort.conf configuration file. Each rule file describes a type of traffic to be reported;
Alert and Logging System: The alert and logging system takes care of generating logs and alerts. The alerts are stored by default in the directory /var/log/Snort/. As soon as the system becomes operational, we can consult the generated alerts directly in the text files or use a management console. ACID (Analysis Console for Intrusion Detection) is an application that provides a management console and allows the visualization of alerts in graphic mode. The alerts in this case are stored in a MySQL database.
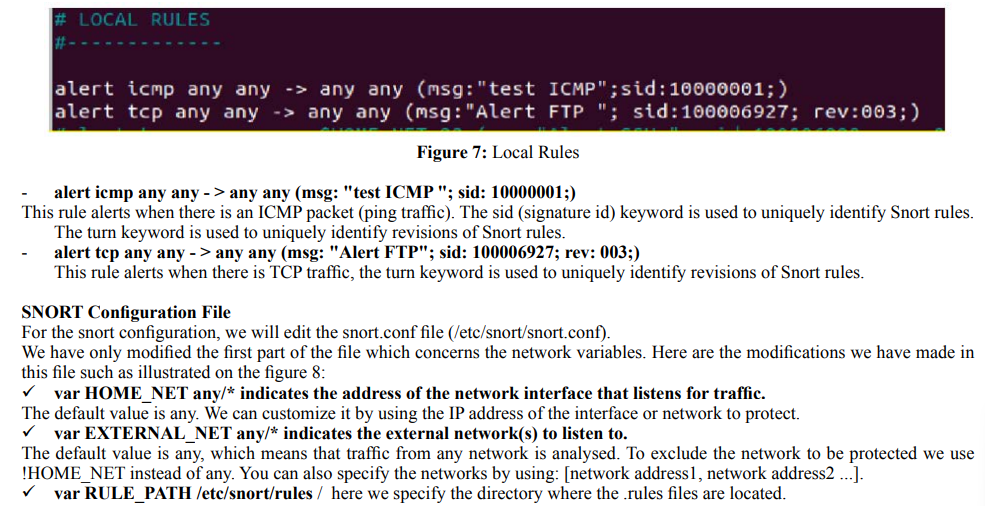
Snort rules are written to ensure that security policies with respect to enterprise monitoring are respected. However, it is important to know how to write a Snort rule, because there are variables, options, and signatures to write, and we are always looking for an optimal solution.
Here is the composition of a Snort rule:
We are going to see in detail each of these points to have the best use and knowledge of a Snort rule.
Snort rules describe a basic action. There are several possible actions to perform on the traffic as illustrated on table 1.
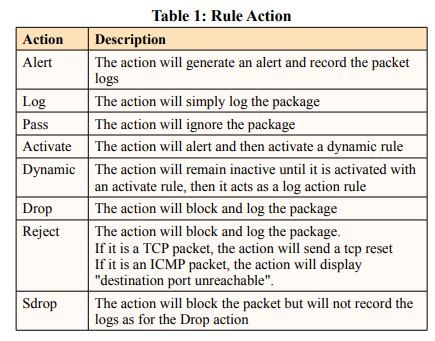
It can be seen in table 1 that with the action, we can indicate what Snort will do, in relation to a given event. Either it will alert in the log/alert file, or log the packets with the event information in the log/log<number> file, or discard it, etc.
It is important to note that only the Alert, Log, Pass, Activate and Dynamic rules are going to be useful to us because these are the rules that are going to allow us to operate as an IDS (and not as an IPS because we are only going to use the IDS part of Snort).
Following the rule, we will now describe the protocols that we can configure.
The rule must be given a protocol to monitor. Indeed, it would be very difficult and very heavy in terms of bandwidth, to observe the traffic of all the protocols, therefore, we will specify one protocol per rule. Here is the choice of protocols available:
The UDP protocol, also called "Best Effort", is a communication and data routing protocol, but without error control.
The TCP protocol is based on IP addressing and is useful for communication between two devices that both have an IP address. The ICMP protocol is a protocol that will allow us to send messages on the machines of a network (for example the PING). The IP protocol allows the transport of data through two machines with an IP address, and it includes ICMP, TCP and UPD.
SVMs are a class of learning algorithms initially defined for discrimination, i.e., the prediction of a binary qualitative variable. They were then generalized to the prediction of a quantitative variable. In the case of discrimination of a dichotomous variable, they are based on the search for the optimal margin hyperplane which, when possible, correctly classifies or separates the data while being as far as possible from all the observations. The principle is thus to find a classifier, or a discrimination function, whose generalization capacity (prediction quality) is the highest possible. This approach follows directly from Vapnik's work in learning theory since 1995. It focused on the generalization (or prediction) properties of a model by controlling its complexity.
As presented in the introduction, SVM is a supervised machine learning model that is mainly used for classifications (but it can also be used for regression). The intuition behind Support Vector Machines is to simply separate data by delimiting them (creating boundaries) in order to create groups. In other words, SVMs aim at solving classification problems by finding good decision boundaries (see figure 3 below) between two sets of points belonging to two different categories.
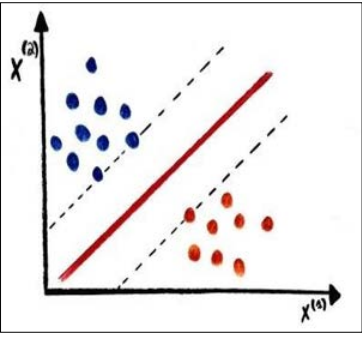
Figure 3: SVM Principle
A decision boundary can be thought of as a line or surface separating your training data into two spaces corresponding to two categories. To classify new data points, you simply check which side of the decision boundary they are on.
SVMs perform the search for these boundaries in two steps:

Figure 4: Decision Frontier
This technique used by Support Vector Machines is called "kernel trick". It transforms the data, and then, based on these transformations, it finds an optimal boundary between the possible outcomes. In other words, it performs extremely complex data transformations and then determines how to separate the data based on the labels you set.
This tool is becoming widely used in many types of applications and is proving to be a serious competitor to the most powerful algorithms (model aggregation). The introduction of kernels, specifically adapted to a given problem, gives it great flexibility to adapt to very diverse situations (pattern recognition, genomic sequences, characters, spam detection, diagnostics...). Note that, algorithmically, these algorithms are more penalized by the number of observations, i.e., the number of potential support vectors, than by the number of variables. Nevertheless, powerful versions of the algorithms allow taking into account large databases in acceptable computation times.
This paper is organized as follows. Section 2 presents related work to study what others have done in the studied area, then section 3 models the proposed intelligent system that combines the Snort intrusion detection system and the SVM machine learning algorithm, as well as the results. Finally, section 4 dresses the conclusion and some prospects.
Shah, Syed & Issac, Biju & Jacob, Seibu [1] conducted a study on machine learning algorithms that can be used with Snort by first performing an analysis via Weka on three different IDS datasets. The SVM algorithm was found to perform the best, followed by fuzzy logic and decision tree. The simple and ensemble versions of SVM were then applied to Snort to improve detection, followed by the combined versions of SVM and fuzzy logic, and SVM and decision tree. The false positive rate of the machine learning optimized intelligent intrusion detection system 17 and the false negative rate were significantly reduced in the optimized versions, especially with the firefly optimization with RPF of 9.0% and FNR of 1.7%.
The paper [2] proposes a system that uses learning rule-based classification and machine learning to automatically detect attacks against networks and computer systems more accurately, the approach uses two different learning styles in series to detect network intrusions. First, they used a rule-based system to identify incoming network packets as either intrusion or normal packets, and then a trained machine learning classifier model to further validate whether the incoming packets are intrusion or normal packets. For the "SNORT" rule-based system and machine learning classification, they used simple logistics, J48, and sequential minimum optimization (SMO). The experimental results show that the proposed approach can successfully reduce the false positive and false negative rate of rule- based NIDS.
Snort captures and checks in real time whether data packets match the traffic characteristics described by a certain detection rule and triggers an alarm if they match, due to insufficient packet capture capacity and performance flaws in Snort's detection engine module. It is difficult to process all the data packets arriving in real time when Snort uses a large number of detection rules to process high- speed network traffic. This results in a high false negative rate. Longwen Shuai & Suo Li [3] analyzed Snort's architecture and proposed a key to reducing the false negative rate under high-speed network traffic: it is to improve Snort's packet capture capability and the performance of the detection engine module. To improve the performance of Snort's packet capture module, they implement Snort's DAQ module based on the DPDK high-performance packet processing framework. Experiments show that Snort's packet capture capability and malicious traffic detection rate under high-speed network traffic were significantly improved after the optimization.
This paper [4] examines the performance of two open-source intrusion detection systems, namely Snort and Suricata, in accurately detecting malicious traffic on computer networks. These systems were installed on two different, but identical computers and performance was evaluated at a network speed of 10 Gbps. Suricata was able to handle faster network traffic than Snort with a lower packet loss rate, but it consumes more computer resources. Snort had better detection accuracy and was therefore chosen for the following experiments. It was observed that Snort triggered a high rate of false positive alarms. To solve this problem, an adaptive Snort plug-in was developed. In order to select the best performing algorithm for the adaptive plug-in of Snort, an empirical study was performed with different learning algorithms and the support vector machine (SVM) was selected. The best result was obtained using an optimized SVM with a Firefly algorithm with a FPR (false positive rate) of 8.6% and FNR (false negative rate) of 2.2%, which proves a good result.
The paper [5], proposes an SDN software-defined network based intrusion detection system using support vector machines (SVMs) along with selective logging for IP tracing which results in a detection accuracy of 95.98% obtained on the full NSL- KDD dataset and 87.74% on the selected sub- features of the dataset. The detection of abnormal traffic and network intrusion is performed at the PACKET_IN event at the controller level and then they retrieve flow statistics from OpenFlow switches at regular intervals. Selective logging of suspicious packets/flows during a PACKET_IN event which allows for IP tracing in the event of an attack that can be initiated by a network administrator using an HTTP-based web console.
An analytical study of intrusion detection techniques presented on the paper [6] the latter is based on support vector machine (SVM) consisting of four main steps, namely data collection, preprocessing, SVM technique for training and testing and decision. The simulated results were analyzed on the basis of overall detection accuracy, receiver operating characteristic, and confusion matrix (ROC). The NSL-KDD dataset is used to analyze the performance of SVM techniques. The results obtained show that the linear SVM, quadratic SVM, fine Gaussian SVM and mean Gaussian SVM give an overall detection accuracy of 96.1%, 98.6%, 98.7% and 98.5% respectively.
Distributed Denial of Service (DDoS) attacks are common today, especially due to the relative simplicity of their implementation and their effectiveness against an unprepared target. These attacks can cause significant financial losses through service interruption or indirectly through damage to the target's image. The occurrence of Software Defined Network (SDN) evokes new methods such as deep learning algorithm is adopted to model the attack behavior based on the collection from the SDN controller. In this paper [7], a mininet and projector simulation platform of SDN environment is built, the characteristic values at 6 tuples of the switch flow table are extracted, and then the DDoS attack model is built by combining the SVM classification algorithms. Experiments show that the average accuracy rate of 95.24%.
The support vector machine (SVM) has played an important role in providing potential solutions to the IDS problem. However, the feasibility of introducing SVM is affected by the difficulties in selecting the appropriate kernel and its parameters. The paper[8] presents a work to apply different kernels for SVM in ID Son the KDD'99 and NSL-KDD dataset as well as to determine which kernel is the best for SVM. An RRE-KDD dataset used to remove redundant records from KDD'99 train. This RRE- KDD includes both the KDD99Train+ and KDD99 Test+ datasets for training and testing purposes, respectively. The results show that the kernel can achieve higher detection rate and lower false positive rate with higher accuracy than the other kernels in the RRE-KDD and NSL-KDD datasets.This paper [9] proposes an anomaly-based IDS using genetic algorithm and support vector machine (SVM) with a new feature selection method. This model uses a feature selection method based on the genetic algorithm by reducing the data dimension, increases the detection of true positives and simultaneously decreases the detection of false positives. The results show that the proposed method can simultaneously achieve high accuracy and low false positive rate (FPR) which results in more stable features compared to other techniques. The proposed model is experimented and tested on the KDD CUP 99 and UNSW-NB15 datasets.
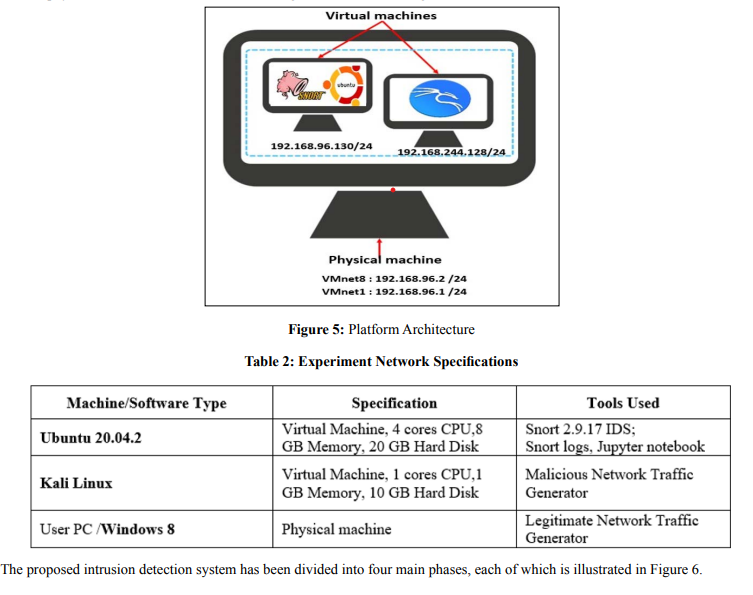
In order to improve the intrusion detection capabilities, we propose in this paper, a system based on the fusion of Snort and SVM techniques. We conducted several platform-based experiments with the hardware as described below.
Our platform requires a physical machine to generate the legitimate traffic with two virtual machines as shown in Figure 5. The first virtual contains the proposed detection system with SVM algorithm in fusion with Snort IDS which uses the default rule set. Using another physical machine, the malicious traffic is generated. Some configured software details are shown in Table 2.

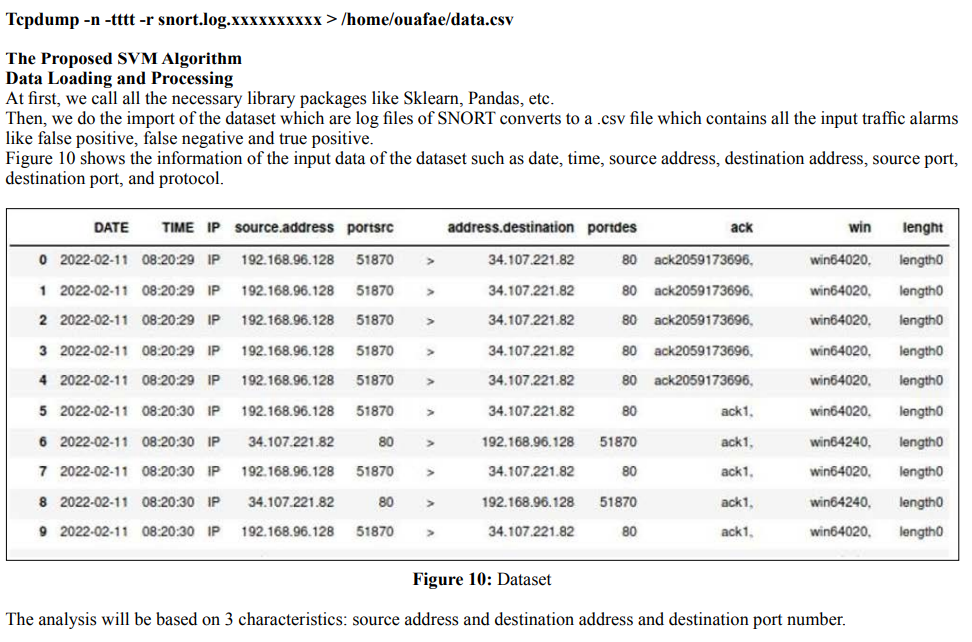
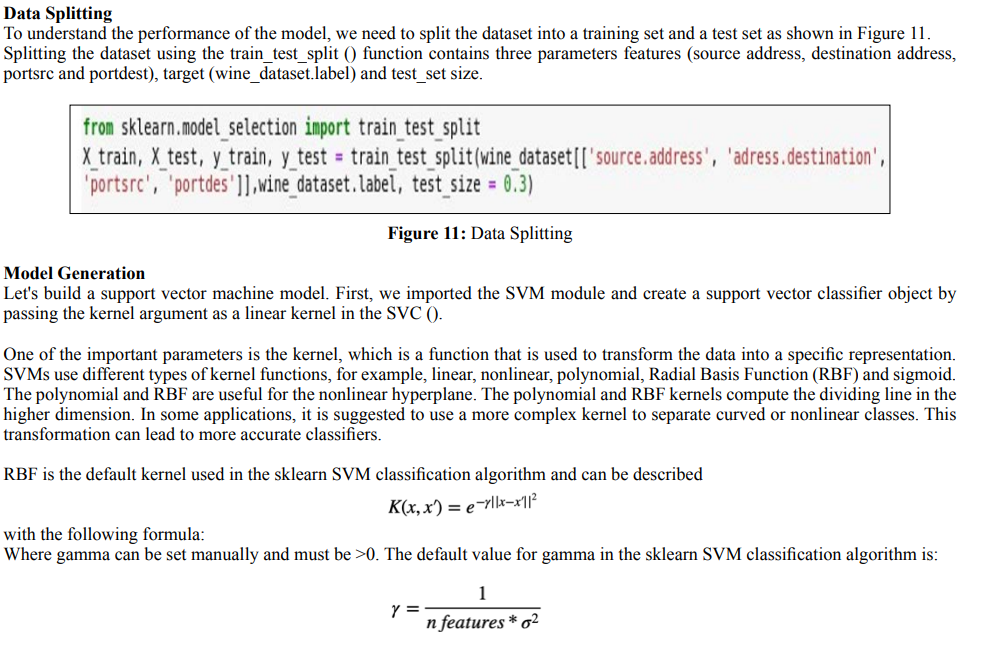
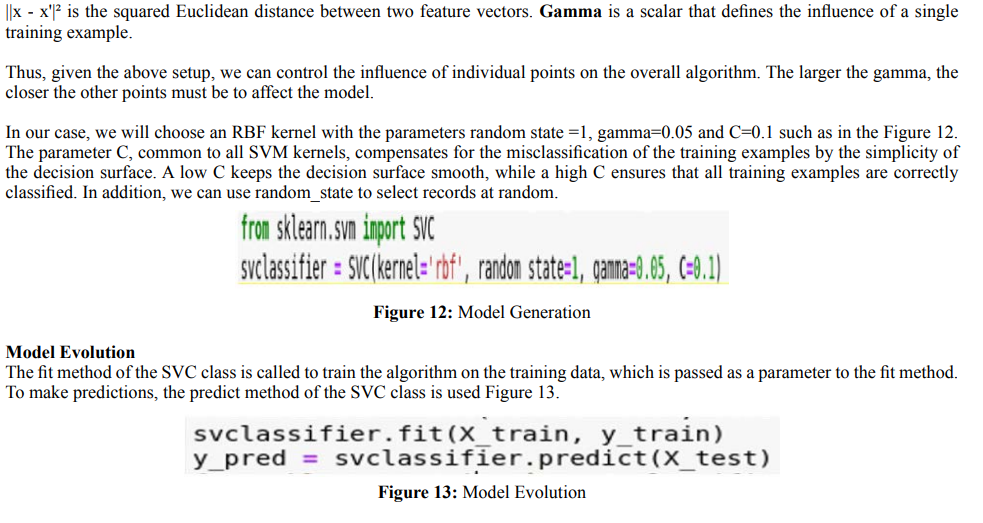

scores are inferior to precision measures because they incorporate precision and recall in their calculation. As a general rule, the weighted average of F1 should be used to compare classifier models, not the overall precision.
F1 score = 2*(Recall * Precision) / (Recall + Precision) Support: The number of occurrences of each label in y_test.
The security of computer networks remains a very sensitive subject for the actors of the computer world because the variables that revolve around this subject are often difficult to master. Even if the evolution of technology has improved, the security mechanisms in computer networks is still difficult or impossible to guarantee 100% security.
Intrusion detection systems are very effective in monitoring and detecting data packets in network traffic. This work focuses on combining SVM machine learning algorithm with Snort intrusion detection system against different types of threats. This proposed intrusion detection system shows better results by comparing it with several support vector machine (SVM) based intrusion detection works, like the work presented on the paper [6] which analyzes the performance of SVM techniques with NSL-KDD dataset and gives maximum detection accuracy 98.5%. Finally we can conclude from our proposed system that Support Vector Machine gives better accuracy on the imported dataset of SNORT.
In future work, advanced data mining techniques and machine learning techniques will be used to detect new suspicious attacks on huge amount of data.
