Author(s): <p>Ravindar Reddy Gopireddy</p>
The high increasing cybersecurity landscape has pushed the difficulties of providing strong security as well as respecting user privacy towards being an
important concentration. This paper focuses on privacy-preserving techniques in the latest innovations of cybersecurity. This study contributes to analyze
the prevalent methodologies today for instance homomorphic encryption, differential privacy and federated learning in order to strive not only a security
secure but also private system using these state of art methodologies. The research goes on to describe the emerging trends and future direction in this area
with some recommendations that could be used for writing secure protection of sensitive data across multiple applications
The growing digitization of data and the prevalence of interconnected devices have dramatically increased the risk from cyberattacks. Consequently, a solid cybersecurity setup has never been more mandatory. At the same time, techniques based in privacy preservation are increasingly sought to safeguard user data against unauthorized access while also making it available for legitimate use. The presented paper deals with the domain of cybersecurity innovation combined to privacy-preserving and traverses over emerging advances that have potential practical implications for future security strategies.
In the age of mass data aggregation and sophisticated cyber- attacks, it has become increasingly difficult to maintain privacy while providing utility from information. They offer creative privacy-preserving means, securing your information processing and analysis that is sensitive without having to violate any of the most intimate details expositing yourself fully. These are the leading cybersecurity innovations that include homomorphic encryption, differential privacy and federated learning. They allow companies to use big data and machine learning while still respecting the strictest privacy standards such as fascists or regulations in this chapter, we visit the fundamental principles (core) of these techniques in addition to its use-cases and advances explaining how all these three approaches are helping shape the cybersecurity world today.
In other words, Homomorphic encryption lets one to do operations on data without un-encrypting (as a norm for any other encrypted values). This technology allows confidential data computation in cloud-computing and other environments with sensitive information. Fully homomorphic encryption is too computationally demanding, but partially homomorphic schemes with less rigidity are already being applied in practice to improve security without much of a performance overhead.
The concept of homomorphic encryption has come a long way since its inception. It is having application from secure voting systems to privacy-preserving data mining. A typical example is for the case of cloud services which enables processing sensitive data without revealing it thereby preserving privacy in outsourced computations.
Healthcare: Ensure the safe use of patient data to provide medical researchers with access without breaking privacy guardrails for patients.
Finance: Secure financial analytics on encrypted data stored in the cloud
Differential privacy introduces a statistical framework that ensures the privacy of individual data points while allowing aggregate data analysis. It adds controlled noise to the data, making it difficult to infer any single data point's information. This method is widely used by organizations to share useful datasets without compromising individual privacy. Differential privacy is particularly effective in scenarios like census data publication and machine learning model training.
These charts provide a visual representation of emerging trends in cybersecurity and data privacy-preserving techniques and highlights the implementation levels of privacy-preserving data mining techniques in various countries:
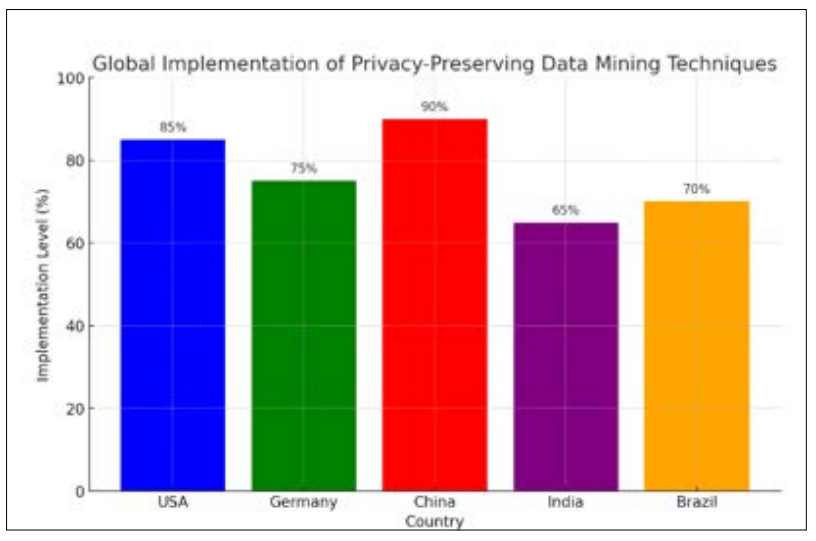
Figure 1: Global Implementation Levels of Privacy-Preserving Data Mining Techniques
Given the U.S. economy accounts for 24% of total world GDP and that it is a global center of technology- and innovation-based sectors, America stands poised like no other to establish best- practices in privacy-preserving data use policies. By dedicating continued investment in and focus on the adoption of these methodologies, the U.S. can affirm its standing as a global leader in data privacy and cybersecurity. This strategic center of gravity will further both national security and the confidence that worldwide partners and customers are seeking as data privacy concerns grow.
The technique allows parties to train a machine learning model together without the need for exchanging any raw data. Instead, it shares the model upadates [which are summed to get a global improvement in fixtures] This method mitigates the risk of privacy breaches by minimizing the exportation of sensitive data. Federated learning is becoming increasingly popular in environments with sensitive patient data (e.g., healthcare), or user-related datasets, like those used by mobile applications - improving privacy while benefiting from a wealth of distributed information.
Federated Learning is the decentralized approach of training a model instead. The process includes:
Privacy-Preserving Mechanisms - Efficiency and Practical
While its contributions in privacy-preserving techniques are significant, where rubber meets the road is how well those ideas work out and what costs they entail. This part covers the case studies and practical deployment in different domains proving that these modern techniques are not only securing confidential information but also realizing operational efficiency, compliance management with strict regulation. These examples from the real-world provide important understanding on the issues faced, achievements gained and lessons learnt in-deploying privacy preserving technologies. The three case studies in this post help exemplify the transformational possibility of these innovations to shift towards a more secure and privacy-focused future.
Financial institutions deal with massive amounts of confidential data, so privacy-preserving methods are critical to their operations and especially for customer trust and regulatory compliance. More protocols like differential access and secure multi-party computation are being implemented to bolster data privacy and security. A case study of how they are currently applied could be Confidential Financial Analytics, where banks and financial firms leverage homomorphic encryption to analyze sensitive transaction data hosted in the cloud without ever having to decrypt it.
Services and User Experiences - Many tech companies and social media platforms collect widespread user data to improve their services, provide better experiences for they users. These companies are using privacy preservation techniques to process data and protecting user privacy.
Differential Privacy File Data Collection Using differential privacy methods to collect data without risking individual anonymity has been in place for Google and Apple user cases. This means that some things such as the differential privacy algorithm in Apple find it much more accessible to improve services like Quick Type and emoji suggestions using an analysis of your behavioral patterns while they protect who you are.
To issue transparent and effective services while retaining personal privacy and satisfying regulatory requirements, governments and public sector entities are increasingly inclined to deploy privacy-preserving methods. An example of this case is the Privacy-Preserving Census Data: national statistical authorities issue census data by using differential privacy, which guarantees that it impossible to distinguish between individual respondees based on published data. This feature isn’t perfect, but it strikes a reasonable compromise between accurate demographic data and substantial privacy protections

Figure 2: Usage of Privacy-Preserving Techniques by Sector
These case studies corroborate the positive impact that privacy- preserving technologies have on future consumers’ security and privacy. These proven use cases truly attest to the value that these new-tech innovations create for industry players who want their data well-protected and business as usual.
The cybersecurity landscape is ever changing, and new emerging trends highlight just how dynamic the field continues to be as a result of balancing security with privacy efforts. Innovations like zero-knowledge proofs, privacy-preserving data mining and decentralized security architectures such as Blockchain are pushing the boundaries of what is known to be feasible in protecting sensitive information. These are far reaching promises: not just to boost the resilience of cybersecurity but also new models guaranteeing data privacy. The discussion in this section provides the current trends, their impact and challenge to cybersecurity technologist on how future direction of cybersecurity technology should be evolved considering that securing digital asset without breaking user trust, regulation.
Zero-knowledge proofs are a method that allows one entity to confirm to a second party that it knows a secret without revealing any other secret information about the secret. For example, ZKPs could be used to confirm a current password without sharing the characters of a password. It is a new privacy measure that may increase privacy throughout the authentication process and make transactions on a blockchain network confidential
These privacy-preserving data mining ways involve the notion of obtaining valuable evidence from a massive byte database without violating or illicitly invading the privacy rights and personal data of individuals involved in such a database. These approaches are predicated on the idea that several parties can create circuits and estimate them concurrently in a manner that protects their privacy. The primary sorts of tests are anonymization and perturbation.
Secure Multi-Party Computation (SMC) SMC allows a set of mutually distrustful parties to jointly compute an arbitrary function over their inputs without revealing the details of this input data functionality. For instance, SMC is quickly emerging as the go- to consensus mechanism for privacy-conscious collaboration in settings like joint data analysis by competing firms.
The decentralized security approach of blockchain where integrity and transparency of data are the main guarantees, along with privacy-preserving approaches such as ZKPs, can provide a secure and private transaction solution, and becoming a strong competitor in handling future cyber security threats.
On the other hand, using its encryption power and decentralization capabilities, blockchain technology provides a coverage for data integrity publicly clearly. CryptoNote is a proof-of-work algorithm that by itself can be used to verify cross-chain transactions, and when combined with zk-SNARKs or similar privacy-preserving technologies makes blockchain solutions secure and private enough plus it may act as part of your future cyber security training.
The advancement of data privacy can also serve as a bridge to multiple other disciplines such as cryptography, machine learning and large scale decision algorithms generating an interdisciplinary melting pot. This could be the basis for novel approaches to solve difficult problems in privacy and security. Stimulating interdisciplinary research will be important to push privacy-preserving technologies toward a state-of-the-art level of development [1-12].
As privacy-preserving technologies become ubiquitous, it unlocks new business models and avenues. This benefits companies in that it enables them to provide privacy enhancing services, and attract customers which value their data security and are concerned about preventative measures preserving the individuals right of informational self-determination. It can drive new revenue and growth drivers in the market. The demand for privacy-centric solutions will continue to grow and organizations that innovate in this area will be well positioned.
The cornerstone of data privacy and protection, however, is cybersecurity - an idea that looms large as we traverse the difficult terrain of digital age. The future of cybersecurity is not just securing against threats, but rather an entire ecosystem where extreme security and seamless user privacy live together as first principles. If there is one thing that never stops evolving it has to be the cybersecurity threat landscape and with this evolution, our strategies are bound to evolve in parallel. New technologies - homomorphic encryption, federated learning and more recently differential privacy among them -enable these possibilities; they offer new ways to build a digital environment that is both private and secure.
They can help us process and analyze data without ever exposing the actual information, leading to more secure cloud computing, trustable financial transactions or privacy-preserving machine learning. With the inclusion of these advanced solutions, we can take steps to protect our most sensitive data even against a more evolved e-threat landscape.
That's not the end of journey, though with adversaries constantly inventing new access vectors so too must techniques, and continuous research is necessary in order to be one step ahead of the pack. As such, it is important to extend and improve upon these privacy-preserving solutions in order to maintain the same balance between security and usability. Moving forward, interdisciplinary collaboration and innovation will be necessary to meet the complex challenges posed by cybersecurity.
Well, to sum it up: The way forward in Cybersecurity is a wide- spread adoption of these state-of-the-art privacy-preserving technologies that organically intertwines within the foundation of our digital infrastructure. In doing so, we not only safeguard data but also protect the trust and integrity underpinning our ever- more interdependent world. By continuing to push the envelope and iterate on what we have learned, it is our strong belief that this commitment will become more common practice than exception.
