Author(s): <p>Estifanos Tilahun Mihret</p>
COVID-19 is an ongoing pandemic and dangerous of coronavirus disease 2019. It caused by the transmission of severe acute respiratory syndrome coronavirus 2 (SARS-CoV-2). COVID-19 spreads most often when people are physically close. And, it spreads very easily and sustainably through the air, primarily via small droplets or aerosols, as an infected person breaths, coughs, sneezes, sings or speaks. The recommended preventive measures include hand washing, covering one’s mouth when sneezing or coughing, physical distancing, wearing a face mask in public, ventilation and air-filtering, disinfecting surfaces, and monitoring and self-isolation for people exposed or symptomatic. Hence, this paper proposed the architecture of physical distancing detection system with distance sensor which deployed on UAV System with the help of BTS (2G/3G/4G/5G) to enrich the COVID-19 preventive measures, as well as I have also developed a few algorithms for distance sensor (on UAV System) operations which sensing, tagging and disseminating the current distance, position and waiting time of resident’s information, and forwarding schemes to respective infrastructures and suspected residents including the security forces.
The COVID-19 pandemic, also known as the coronavirus pandemic, is an ongoing pandemic of coronavirus disease 2019 (COVID-19) caused by the transmission of severe acute respiratory syndrome coronavirus 2 (SARS-CoV-2). It was first identified in December 2019 in Wuhan, China [1]. The outbreak was declared a Public Health Emergency of International Concern in January 2020 and a pandemic in March 2020. As of 27 October 2020, more than 43.5 million cases have been confirmed, with more than 1.15 million deaths attributed to COVID-19 [2]. COVID-19 spreads most often when people are physically close. And, it spreads very easily and sustainably through the air, primarily via small droplets or aerosols, as an infected person breaths, coughs, sneezes, sings or speaks. It may also be transmitted via contaminated surfaces, although this has not been conclusively demonstrated [3-5]. Airborne transmission from aerosol formation is suspected to be the main mode of transmission. It can spread from an infected person for up to two days before they display symptoms, and from people who are asymptomatic. People remain infectious for seven to twelve days in moderate cases, and up to two weeks in severe cases.
Common symptoms include fever, cough, fatigue, breathing difficulties, and loss of smell and taste. Complications may include pneumonia and acute respiratory distress syndrome. The incubation period is typically around five days but may range from one to 14 days. There are several vaccine candidates in development, although none have completed clinical trials. There is no known specific antiviral medication, so primary treatment is currently symptomatic [6].
Recommended preventive measures include hand washing, covering one’s mouth when sneezing or coughing, physical distancing, wearing a face mask in public, ventilation and airfiltering, disinfecting surfaces, and monitoring and self-isolation for people exposed or symptomatic. Authorities worldwide have responded by implementing travel restrictions, lockdowns, workplace hazard controls, and facility closures. Many places have also worked to increase testing capacity and trace contacts of the infected.
Physical distancing (also known as social distancing) includes infection control actions intended to slow the spread of the disease by minimizing close contact between individuals. Methods include quarantines; travel restrictions; and the closing of schools, workplaces, stadiums, theatres, or shopping centers. Individuals may apply physical distancing methods by staying at home, limiting travel, avoiding crowded areas, using no-contact greetings, and physically distancing themselves from others [7,8]. Many governments are now mandating or recommending physical distancing in regions affected by the outbreak. Non-cooperation with distancing measures in some areas has contributed to the further spread of the pandemic.
However, to enforce the rule of physical distancing by lockdown and related ways in developing countries such as Ethiopia, it is very tough because of their majority populations are living in hand-to-mouth life style. So, they need another method that is why this paper proposed.
In this paper, I have designed the architecture of physical distancing detection system with distance sensor which deployed on UAV System with the help of BTS (2G/3G/4G/5G) to enhance the COVID-19 preventive measures. Besides the architecture, I have also developed a few algorithms for UAV System operations which sensing, tagging and disseminating the current distance, position and waiting time of resident’s information, and forwarding schemes to respective infrastructures and suspected residents including the security force.
The paper is organized into two broad sections followed by conclusion, recommendations, acknowledgement and references. Section II describes about the related works in detail. And, section III gives a deep design of the architecture of the proposed solution with the developed algorithms.
In a proximity detection and contact tracing for COVID-19 has been presented [9]. The press released different techniques to enhance the workplace safety by enforcing social distancing policies with proximity sensors. The main objectives of the press are to ensure that people are keeping the safe distance between each other and reduce virus interactions, avoid temporary shutdowns of operating factories with enhanced safety measures and track all the interactions between the infected and healthy people to identify a contamination cluster.
The press has presented five basic techniques or solutions to proximity detection and contact tracing for COVID-19. As a first technique, each employee can be equipped with a compact wearable proximity sensor which enables easy monitoring of interactions within the common areas, also working alongside security badges for access control when the sensors record that two or more people have exceeded the safety limit, it warns them with an audible or visual alarm. In addition, as an optional, there is a centralized monitoring of contact events which can afterwards help back-track contaminations chains, making it easy to locate contamination clusters. In the second technique, zoning policy enforcement, factory floor is subdivided into zones to limit spread of COVID-19. It help workers remain within their assigned zones by audio notification and optionally inform the management if worker repeatedly violates the zoning policy. In the third method, density policy enforcement, the audio warning help employees respect maximum density of shared areas (e.g. rest and food areas, meeting rooms). And, the employee to employee proximity monitoring takes in account distance and time. As like as the first method, this method also has two options. As a first option, there is a centralized monitoring and violation reporting, and as a second option, there is a backtracking of infection chains. In the fourth method, sanitization of shared assets, the worker presence in front of shared-use asset can be analyzed using proximity detection. The asset requires only inexpensive Bluetooth Beacon and the disinfect assets based on usage metrics. And, it ensure traceability of cleaning operations with a list of visited WiFi/BLE SSIDs or another Abbeeway device. In the final method, Nurse-call bedside buttons in hospitals, the nonmedical facilities get converted to hospitals to manage large influx of Coronavirus patients. The patients in these facilities need nurse call-buttons - Tracker has button and can locate bed. And also, the trackers can be used to monitor usage and prevent loss of medical equipment (e.g. Respirators).
The press has also presented in technical perspectives (from devices to screens - processing positioning information at the edge of the LPWA network to deliver actionable data to business applications) as follows:
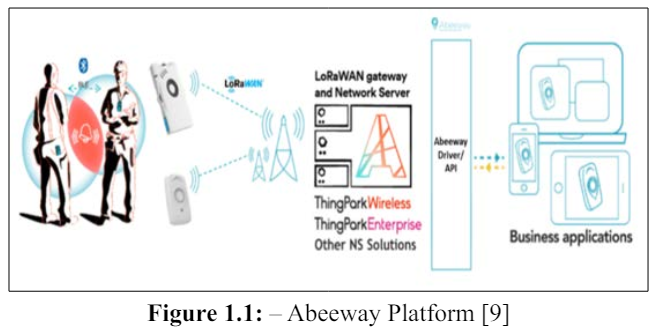
However, the work considered only the indoor surroundings such as business centers and industries, thus further exploration on outdoor conditions such as open market places and concerts are needed. Furthermore, the work completely depends on the behalf of the workers because of if one worker off the wearable proximity sensor, the work cannot enforce the social distancing policies. And also, the work presented the centralized monitoring of contact events as optional but it should be mandatory to ensure the enforcement of social distancing policies.
In [10] a comprehensive survey and open problems on enabling and emerging technologies for social distancing has been conducted. The work intentions to provide an inclusive background on social distancing as well as how emerging technologies, e.g., wireless and networking, machine learning, artificial intelligence (AI), computer vision, thermal, ultrasound can enable, encourage, and even enforce social distancing practice.
The authors have identified/proposed a practical social distancing scenarios in the survey. The scenarios can be briefly classified as follows:
However, all these proposed scenarios are not respect the citizens’ privacy as well as the scenarios are completely depends on the consensus of the residents.
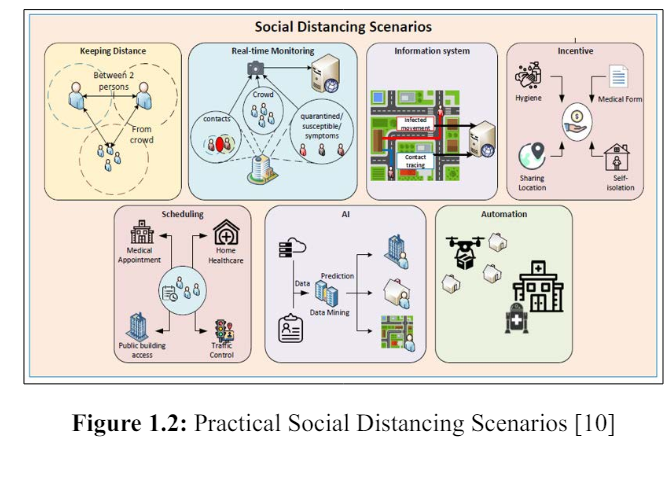
Figure 1.2: Practical Social Distancing Scenarios [10]
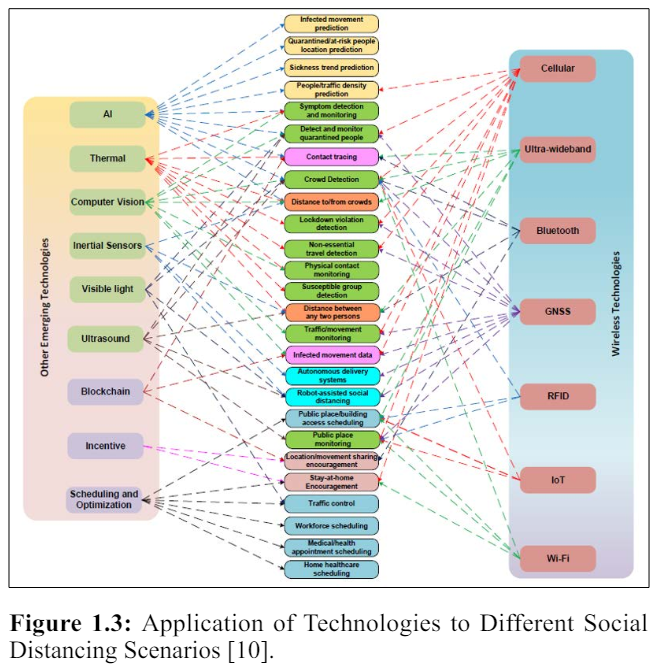
The work has presented an important open issues and challenges, (e.g., privacy-preserving, scheduling, and incentive mechanisms) in implementing social distancing in practice. As an example, instead of reacting with ad-hoc responses to COVID-19-like pandemics in the future, smart infrastructures (e.g., next-generation wireless systems like 6G, smart home/building, smart city, intelligent transportation systems) should incorporate a pandemic mode in its standard architecture/design.
As I have discussed in related work, different technologies are very significant to enforce the physical distancing policies. Most of current works on physical distancing enforcement are focusing on indoor environments and they completely depends on the behalf of the residents/workers because of if one resident/worker off the wearable proximity sensor (a technology that support to enforce the physical distancing policies), the resident/work cannot apply the policies. And also, the works presented the centralized monitoring of contact events as optional but it should be mandatory to ensure the enforcement of physical distancing policies. Hence, to overcome these limitations (particularly on outdoor/high coverage area) as much as possible, I have proposed the architecture of physical distancing detection system with distance sensor which deployed on UAV System with the help of BTS (2G/3G/4G/5G) to enrich the COVID-19 preventive measures, as well as I have also developed a few algorithms for distance sensor (on UAV System) operations which sensing, tagging and disseminating the current distance, position and waiting time of resident’s information, and forwarding schemes to respective infrastructures and residents including the security forces
I describe and present the overall architecture of my proposed system on potential spots such as pedestrians’ walkways, restaurants, taxi fermatas, stadiums and open shopping centers as shown in Figure 1.4. As a first section, I describe and present my proposed distance sensor on UAV System operations which periodically sensing, tagging and disseminating the current distance, position and waiting time of resident’s information with MAVLink and other related packets. As a second section, approaches and objectives of forwarding models of the sensed information (tagged packets) to the respective infrastructures and residents including the security forces are discussed. And, as a final section, I discuss and present the general proposed architecture states.
Figure 1.4 shows the general low-level architecture of the proposed system on potential spots such as pedestrians’ walkways, restaurants, taxi fermatas, stadiums and open shopping centers. In this low level architecture, I have designed four major wireless and wired infrastructures (UAV System, UAV’s GCS (Gateway Control Station), BTS (2G/3G/4G/5G) and Central Control Station (like data center)) with their respective locations and the communication range of each wireless infrastructure is considered as an ideal cell.
I have supposed that the proposed single small UAV system is a full autonomous Quadrotor Drone (4 rotor wing) type which does not require any direct human intervention for flying (uplink communication) and it capable to hover on a specific area for a while. The system has deployed around on the potential spots/areas with about 10m altitude (height) of UAV flight from the ground and its transmission range covered nearby 150-200m, and completely confined by the transmission range of BTS (2G/3G/4G/5G). The drone has a hovering motion over the area of sensing operation and proceed a different types of communications such as with residents’ mobile phones, BTS (2G/3G/4G/5G) and central control station via IEEE 802.11b/g interface with the help of its CCT BS/GCS.
In the proposed architecture/model, I have only used a downlink communication that a UAV broadcasts the sensed information (tagged packet) within coverage area. In order to this, the residents’ mobile phones and GCS will receive the broadcasted packet via LOS or direct radio link of IEEE 802.11b/g communication. In addition, the GCS which being in the proposed model has also used as a gateway to facilitate a communication among UAV-to-BTS (2G/3G/4G/5G) and UAV-to-Central control station.
Whereas the BTS (2G/3G/4G/5G) network has designed on the road segment as one of the wireless access network infrastructures. I supposed that the BTS (2G/3G/4G/5G) cell covered about 1km which means it can completely cover the coverage area of the other deployed infrastructures as shown in Figure 1.4. And, the network can communicate with the UAV System through its core network (Base Station Center/BSC). As well as, the BTS (2G/3G/4G/5G) network can make a direct communication with residents’ mobile phones.
Central Control Station (Centralized Data Center) has also designed on the road segment. The control station is connected with Internet (Cloud/Gateway) to communicate with the designed infrastructures including the security forces’ mobile phone. Moreover, I have considered few basic assumptions when I design the proposed architecture. For instance, all residents and security forces have a mobile phone.
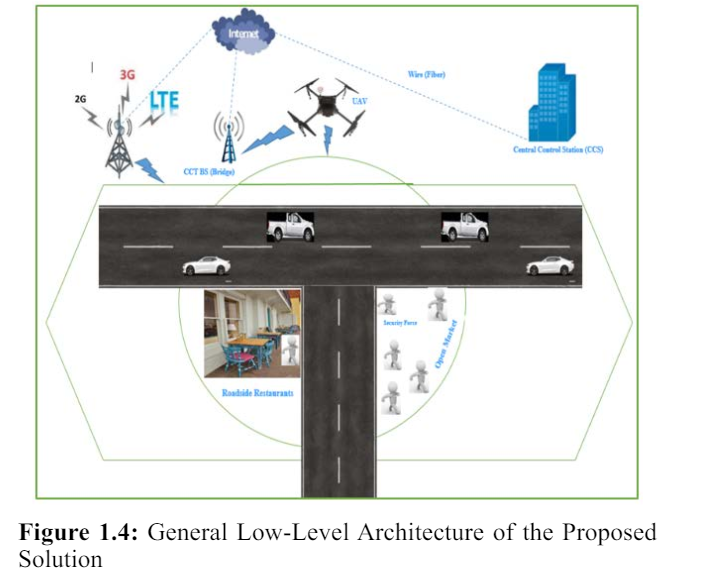
Figure 1.4: General Low-Level Architecture of the Proposed Solution
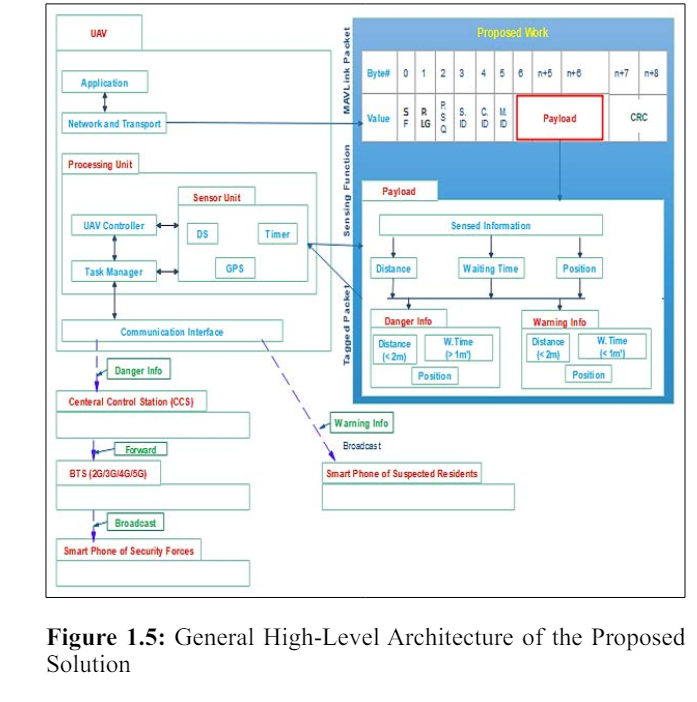
Figure 1.5 that shown on the below depicts the overall high-level architecture that will be implemented in the proposed system in a potential spots like open markets. Generally, the architecture has four core modules, Unmanned Aerial Vehicle (UAV), BTS (2G, 3G, 4G, 5G - Mobile Networks), Central Control Station (Data Center) and Residents and Security Forces Mobile Phones respectively. And also there are four major proposed forwarding schemas that from Distance Sensor (DS) on UAV to Central Control Station (Data Center), Central Control Station (Data Center) to BTS (2G/3G/4G/5G, BTS (2G/3G/4G/5G) to Suspected Residents (Residents’ Mobile Phones), and Distance Sensor on UAV to Suspected Residents (Residents’ Mobile Phones).
In the UAV module, there are four major layers such as application, network & transport, processing unit, and communication layers respectively as revealed in Figure 1.5 as shown below [11, 12]. The communication layer has capable to transmit and receive various data from/to other UAV and/or GCS via IEEE 802.11b/g based RF transceiver. In the processing unit layer, there are three major internal modules such UAV Controller (FCS), Task/Mission Manager and Sensor Unit. The primary operation of UAV controller is reads and analyzes data from a wide variety of sensors and produces a mission flight plan, and it has direct communications with sensor unit and task manager modules. Task/Mission Manager module is responsible for registering new and monitoring ongoing missions, and it has three direct communications such with sensor unit module, task manager module and communication interface layer. The third module of processing unit layer is a sensor unit which responsible for detecting and measuring a different stimulus and signal of UAV’s internal part and sensing operation area. In this module, there are many well-known sensors are installed, such as GPS for navigating a position of UAV and operation area, Distance Sensor (DS) for measuring the distance of residents being in the operation area and Timer for determine the waiting time among nearest residents from operation area. The network and transport layer of UAV is a fundamental layer that primarily responsible for routing a MAVLink packet and end-to-end communication via UDP or TCP/IP respectively [13]. Whereas, the last layer of UAV module is application layer that accountable for supporting and providing different services such as mapping, surveying, traffic controlling, military operation and border monitoring. However, those applications are depending on the type and capacity of UAV.
As presented in Figure 1.6, the 2G/3G/4G/5G - Mobile Networks module has two major components which named as BTS/ NodeB/eNodeB (eNB) / gNB and BSC/EPC Server (Gateway) respectively. The BTS/NodeB/eNodeB(eNB)/gNB is a fixed base station that has GSM/UMTS/E-UTRAN/NR interfaces (radio technologies). And, it can transmit and receive different data and signals from/to residents and security forces mobile phones via its own transceiver antenna within a cell. Whereas, BSC/EPC Server (Gateway) has encapsulate and control the core network of 2G/3G/4G/5G which includes different respective gateways such as S-GW and PDN-GW.
The Central Control Station (Central Data Center) module which demonstrated in Figure 1.6 has three basic layers. They are core network, aggregation network, and access network. The core network layer is responsible for connecting the data center (central control station) to the Internet. The aggregate network layer is responsible to make interconnect together multiple access layer switches and also it is connected to each other by core network layer switches. Whereas, the access network layer is responsible for connecting end-users or end nodes such as PCs and printers. And it supposed to facilitate the continuous network connection of the end devices no matter where they are located. Moreover, all layers are connected to each other directly and indirectly
As shown in Figure 1.6, the Residents and Security Forces Mobile Phones module has three major layers. They are hardware layer, middleware layer, and application layer respectively. The hardware layer is responsible to make a connection with the middleware layer services such as data storage, location management, and communication management. The middleware layer is responsible to facilitate a communication between hardware and application layers. The application layer is responsible to offer different services/application to user and to facilitate a communication with middleware layer.

In this section, I have proposed UAV periodically sensing, tagging and broadcasting operations of the current distance, position and waiting time of residents’ information with a single small UAV to enforce the physical distance policy. Next, I discussed every UAV’s proposed operation as follows.
In this first task of the proposed high-level architecture model, I have only used a downlink communication that a UAV broadcasts the sensed information (tagged packet) within coverage area. In order to this, the residents’ mobile phones and GCS will receive the broadcasted packet via LOS or direct radio link of IEEE 802.11b/g communication. In this work, I have interested to periodically sense the distance, position and waiting time of residents within UAV’s transmission range. To achieve this, the UAV will periodically broadcast a beacon or Hello message to residents’ phone within its transmission range, and if the message is received by the residents then I will use a UAV’s DS, GPS and Timer to detect current distance, position and waiting time of residents respectively. As shown, in Figure 1.4, the UAV’s transmission range has covered the road and some potential spots; thus the residents who being in these spots would be detected by UAV’s sensors. And, the detected information will be organized as a danger or a warning information and stored in a payload of MAVLink packets as I have discussed follows.
After completing the UAV’s sensing operation, the sensed information will be tagged in a MAVLink packet via UAV. In this tagging operation phase, I will organize the sensed information as a danger or a warning message. To proceed the organization process, I have proposed a model that helps me to arrange the sensed information in an easy manner. Additionally, this proposed model is not only significant for arranging the sensed information even it is very compulsory to forwarding the information to the respective infrastructures and residents including the security forces.
Generally, in the proposed model, any periodically sensed information in the coverage area of UAV System only consists the distance, position and waiting time between nearest residents. Then based on this circumstance, I have proposed a model of danger and warning info and optimize the forwarding of the information to the target infrastructures and residents. I have discussed this proposed model in details as shown as below.
I have assumed that if the distance between nearest residents is less than 2 meter and their waiting time for less than 1 minute, there is no a high likelihood to expose the COVID-19. And, the distance among the nearest residents denoted by D, their waiting time represented by T and the all sensed information which consists the distance, position and waiting time of residents within the coverage area of UAV denoted by I. Therefore, if the distance among the nearest residents is less than 2 meter and their waiting time is more than 1 minute, I will be classified as a danger information and tagged in the Danger Info module of the proposed work in the payload of MAVLink packet. Whereas if the distance among the nearest residents is less than 2 meter and also their waiting time is less than 1 minute, I will be classified as a warning information and then tagged in a Warning Info Module.
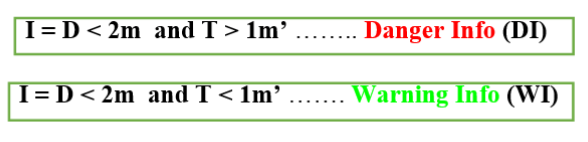
Where, D is distance, T is time, m is meter, and m’ is minute.
After accomplishing the tagging process, the UAV will proceed the forwarding schemes based on the tagged info.
Algorithm 1.1 shows the pseudo code of UAV sensing, tagging and broadcasting operations of resident’s info on potential spots.

In this section, I have discussed the proposed forwarding model of the tagged information to infrastructures and residents. Generally, there are two proposed forwarding schemes as stated below.
The distance sensor (DS), timer and GPS on UAV sense the current distance, waiting time and location of the residents on UAV’s coverage area. And, if the sensed distance is less than 2m and the waiting time is more than 1 minute then immediately the UAV forward the Danger Info to Central Control Station (CCS) via its own Ground Control Station (GCS), and the CCS check the location (the nearest) security forces and forward the info to them via BTS (2G/3G/4G/5G) as stated in Algorithm 1.2.
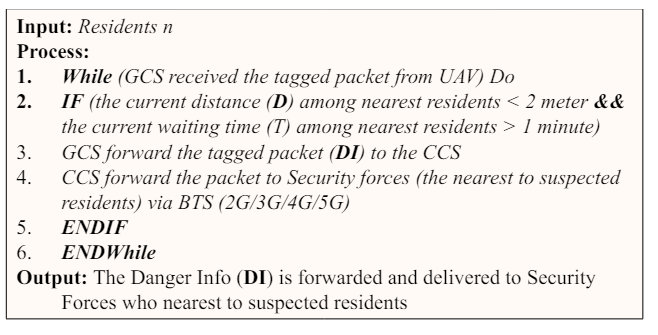
Algorithm 1.2: Algorithm for Forwarding of Danger Info to Security Forces who nearest to Suspected Residents
The distance sensor (DS), timer and GPS on UAV sense the current distance, waiting time and location of the residents on UAV’s coverage area. And, if the sensed distance is less than 2m and the waiting time is less than 1 minute then immediately the UAV directly broadcast the Warning Info to the suspected residents who being on the UAV’s coverage area as stated in Algorithm 1.3

Algorithm 1.3: Algorithm for DirectForwarding/Broadcasting of Warning Info to Suspected Residents who being on UAV’s Transmission Range
The suggested preventive measures of COVID-19 by WHO include hand washing, covering one’s mouth when sneezing or coughing, physical distancing, wearing a face mask in public, ventilation and air-filtering, disinfecting surfaces, and monitoring and self-isolation for people exposed or symptomatic. Thus, this article proposed the architecture of physical distancing detection system with distance sensor which deployed on UAV System with the help of BTS (2G/3G/4G/5G) to enrich the COVID-19 preventive measures, as well as I have also developed a few algorithms for distance sensor (on UAV System) operationswhich sensing, tagging and disseminating the current distance, position and waiting time of resident’s information, and forwarding schemes to respective infrastructures and suspected residents including the security forces.
Though I did my best to propose the architecture of physical distancing detection system with distance sensor which deployed on UAV System with the help of BTS (2G/3G/4G/5G) to enrich the COVID-19 preventive measures, as well as I have also developed a few algorithms for distance sensor (on UAV System) operations which sensing, tagging and disseminating the current distance, position and waiting time of resident’s information, and forwarding schemes to respective infrastructures and residents including the security forces, I do not trust that the architecture is standard enough to incorporate potential matters in networking discipline. For example, despite the importance of the issue, I have not considered the security and privacy aspect of the networking science in my architecture since it was beyond the scope of this work. Thus, I hope that the proposed architecture can be enriched in such a way that the security is taken into account.
Regarding implementation (simulation), I have not considered/ implemented the proposed architecture and forwarding algorithms. Therefore, I believe that the proposed architecture with its forwarding schemes can be enriched in such a way that their implementation is taken into account.
Furthermore, regarding infrastructure deployment consideration, I have not considered an optimal deployment of multiple UAVs (Drones) to proceed UAV’s operations (sensing, tagging, and broadcasting of the current distance, waiting time and location of the residents information within UAV coverage area) on different potential spots. Hence, I hope that the proposed architecture can be enriched in such a way that the optimal deployment of multiple drones on different potential spots is taken into account.
This work would not have been possible without the endless support of son of St. Merry, Almighty God, thus we praise always the name of him and his mother. In addition, this paper is dedicated for my beloved country, Ethiopia.
