Author(s): Vivek Somi
This work explores the critical issue of security vulnerabilities in the Continuous Integration and Continuous Deployment (CI/CD) pipeline, an approach rapidly embraced in modern software development to boost speed and efficiency. While CI/CD approaches accelerate software delivery, they present a range of potential security issues that must be addressed. The paper emphasizes the importance of integrating security measures throughout the CI/ CD lifecycle by employing automated testing and deployment methods in code development and repository management. The primary security issues highlighted include code defects, unstable dependencies, misconfigured environments, and challenges in securing containerized applications. Addressing these risks helps underscore the necessity for businesses to implement best practices in configuration management, conduct regular security audits, and utilize automated security testing technologies. Ensuring that security is perceived as a shared responsibility rather than a secondary concern relies on fostering a security-first culture within development and operations teams. Emerging methods and technologies aimed at enhancing security within CI/ CD environments include static and dynamic application security testing (SAST and DAST), Software Composition Analysis (SCA), and Infrastructure as Code (IaC) practices. This article seeks to provide companies with a comprehensive understanding and practical guidance to establish robust security policies within their CI/CD systems. Prioritizing security in the CI/CD architecture can significantly reduce the risk of data breaches and system failures, thereby increasing customer confidence in digital products.
Integration security takes front stage in the development process as cycles combining program creation and deployment racing at a unique speed in the digital age of today. Businesses today build, test, and distribute software differently as cloud-native apps with pipelines for continuous integration/continuous delivery (CI/CD) become more common. But if we are to guarantee regulatory compliance and safeguard personal data, this also presents major security concerns that demand attention. For companies trying to include security controls right into the CI/CD process, DevSecOps - a methodology consisting of security concepts in a CI/CD framework has grown even more important. Among teams working on operations, development, and security, DevSecOps marks a cultural revolution encouraging group accountability and cooperation. By including security into the Continuous Integration/ Continuous Deployment (CI/CD) strategy, businesses can address vulnerabilities before development, therefore reducing the chance of security breaches or the cost of corrective action. This proactive approach ensures that, rather than as a final issue, security is natural throughout the development process. When businesses adopt cloud-native technologies usually needing dynamic environments and microservices architecture, the traditional perimeter-based security solutions are insufficient. Instead of trying to control the complexity of modern software development, a more all- encompassing, ongoing safety strategy is required. Among the particular security concerns the cloud-native environment raises are poorly specified cloud services, inadequate access constraints, and container vulnerabilities. Companies employing containers and serverless designs also must have good security policies handling the specific risks related with these technologies based on their needs. More complexity for implementing container safety measures or ensuring suitable separation between workloads is added by Kubernetes and other container orchestrating systems [1-4].

Figure 1: Cloud Native CI/CD Pipeline
Directly integrating safety measures in the CI/CD pipeline allows companies to use automation to run security audits at multiple locations, from code commits through deployment, therefore lowering the risk of exposing vulnerabilities into use. From a cloud-native standpoint, businesses ready to apply DevSecOps in a CI/CD pipeline must combine security integration technologies, tools, and approaches. Combining the two forms of security testing (DAST and SAST) techniques would help vulnerabilities to be found during pre-production. Using Infrastructure as Code (IaC) approaches also helps companies follow security guidelines by means of automated inspections, therefore preventing misconfigurations during deployment. By allowing teams to version their security rules alongside the code of the application, using security as code lets them foster a culture of responsibility and openness. Usually, a solid DevSecOps plan relies largely on communication and cooperation. Working closely with the groups of development and operations, security teams help to guarantee that security needs are completely understood and implemented in the development process [5,6]. Quick identification and resolution for security concerns are made possible by constant surveillance and feedback loops. By including security measurements and key performance indicators, or KPIs, into the CI/CD process, businesses can assess their security posture and make well-informed decisions to enhance their security systems anchored on facts. Growing use of cloud-native technologies and the increasing complexity of cyberthreats highlight the importance of applying DevSecOps in modern software development. Businesses who overlook security aspects of their CI/CD systems risk severe vulnerabilities and possible breaches. Conversely, companies which successfully incorporate security technologies into their development strategies might foster a culture of safety consciousness, which would finally lead to more safe software releases and higher customer confidence. Not only a recommended habit but also a requirement for security to be embedded into the CI/CD pipeline in the fast- paced, threat-filled internet environment of today [7,8]. DevSecOps provides a framework for businesses to embed security policies all through the software development process, therefore promoting cooperation, automation, and ongoing improvement [9]. Using a DevSecOps methodology will be absolutely vital in maintaining the safety and resilience of your apps in a constantly changing threat environment as companies negotiate the complexity of cloud-native development [10].
Alanda 2022 et al. Emphasizing speed and efficiency via several tools and programming languages, the application development process has changed dramatically. Applying Continuous Integration (CI) with Continuous Delivery (CD) lets one quickly develop and distribute applications. Automated deployment of real-time apps on cloud infrastructure via the AWS Code Pipeline - source code resides on GitHub and Amazon S3; the AWS Code Pipeline tests automatic deployment. Based on results, all programming languages can be used successfully; their average deployment time is 60 seconds [11].
Paul 2021 et al. Delves into the adoption of Security-First approaches within CI/CD pipelines in cloud computing environments, focusing on the enhancement of DevSecOps practices. As organizations increasingly migrate their development operations to the cloud, the traditional DevOps model, which emphasizes speed and agility, has faced scrutiny due to its insufficient focus on security. This study argues that a shift toward a DevSecOps paradigm where security is embedded from the inception of the development process is imperative for mitigating risks associated with cloud- native applications [12].
Carroll 2021 et al. Canary deployments, green/blue installations and roll-back - before they are put into use, both ad hoc and system integration test traffic can be directed towards components. This design incorporates front-end code by means of server-side JavaScript bundle rendering. Pre-production deployments side by side with production deployments using suitable degrees of isolation in environments designed for integration testing. Pre- production components are known to operate with production exactly as they are following a successful integration test run. Test traffic employs daily copies of staging databases taken from production databases for isolation, therefore excluding sensitive information. Safety and security issues are addressed not monolithically but rather with specific attention. This design better fits agile business practices than conventional techniques; scales well with organization size, and is more effective for integration testing [13].
Ravi 2021 et al. Explores important ideas including automated compliance checks, shift-left security, and continuous security testing to fully appreciate how these ideas improve the security posture of cloud-native apps. The foundation of the DevSecOps methodology, shift-left security stresses early integration of security measures into the development lifecycle, therefore discovering and reducing vulnerabilities at the earliest phases of the application lifetime. Early approach helps to lower the complexity and cost connected with late-stage security updates. Including automated inspections in the Continuous Integration/ Continuous Development (CI/CD) process guarantees that every code commit and deployment is under careful inspection and helps to further complement this paradigm a lot more [9].
|
Author’s name / Year |
Methodology used |
Problem statement |
Research gap |
|
Bernhardt/2021 [14] |
Automated CI pipeline for embedded devices. |
Limited wireless testing in IoT continuous integration for embedded devices. |
Lack of practical CI pipelines for testing embedded IoT devices. |
|
Sivathapandi/2021 [15] |
Optimizing CI/CD pipelines for cloud-native enterprise application deployment challenges. |
Challenges in optimizing CI/CD pipelines for cloud-native technologies. |
Limited studies on CI/ CD pipeline optimization in cloud- native environments. |
|
Ghimire/2020 [16] |
CI/CD pipelines for cloud deployment. |
Challenges in cloud- based CI/ CD pipeline deployment and optimization strategies. |
Lack of simplified CI/ CD solutions for small teams in cloud. |
|
Khan/2020 [17] |
DevOps pipeline plementation on cloud. |
Automating cloud DevOps pipeline with CI, CD, and monitoring. |
Limited cloud-native DevOps automation integrating CI, CD, and monitoring. |
|
Ivanov/2018 [18] |
Serverless DevOps pipeline implemented using CI/ CD and monitoring practices. |
Challenges in automating DevOps practices for serveries applications identified. |
Limited studies on DevOps automation practices for serverless computing applications. |
Shift-left security highlights the crucial need of implementing security techniques prior to the creation of software process, therefore changing the approach teams take to handle application security. Early-stage security guidelines should be given primary priority so that companies can find and fix problems before they become major concerns. This proactive approach assists development teams to control prospective dangers, therefore reducing risk by means of regular security reviews during the planning and development phases. Under this method, Static Application Security Testing (SAST) becomes rather relevant whenever one evaluates the code of vulnerabilities as they become written. Teams improve the general security postures for their apps by embedding security in the development process, therefore lowering the costs associated with late-stage repairs and updates. This intentional change guarantees that security is seen as a basic component of the quality of software, hence fostering a culture of security consciousness among developers and hence producing increasingly strong and safe products over time [19].
Strong application security mainly concentrates on adding constant security evaluations all around based on the cycle of continuous integration and continuous deployment. Safety checks ensure that every code change passes comprehensive testing prior to deployment from every pipeline point of view. Using automated methodologies, teams can evaluate efforts in real time as Interactive Application Security Testing (IAST) or Dynamic Application Security Testing (DAST), therefore allowing the detection of vulnerabilities and compliance issues as they grow. Constant security monitoring and review help to lower the possibility of using vulnerable code. This proactive approach not only improves the general safety posture of apps but also increases their resistance against different threats, thereby offering an additional safe software development environment which delivers security precedence alongside quick delivery [20].
Maintaining compliance calls for the use of automated techniques verifying adherence to legal criteria or organizational security standards. By including automated compliance inspections in the Continuous Integration or Continuous Deployment (CI/CD) process, businesses can track security setups and processes in real time against set criteria including the General Data Protection Regulation (GDPR) and the Consumer Privacy Act of the State of California (CCPA). Regular infrastructure or code compliance audits enable these solutions to automatically detect any deviations or flaws that might surface during deployment and development. Also, frequent compliance audits enable businesses to promptly address any issues, therefore lowering their risk of fines. Apart from promoting adherence to rules, this proactive strategy helps the company to foster a culture for responsibility and accountability, therefore enhancing the general security posture or authenticity of the software development process [21].
Secure applications are defined early in the design process via early security risk and vulnerability assessments. By closely reviewing the architecture and components of the application through threat modelling sessions, development teams can find any attack paths prior to the project starting point. Early on application of required security rules and design changes made possible by proactively assessing risks in the early stage of application development. By means of specific tools or threat modelling systems, teams can find vulnerabilities and grade them based on their impact or probability. Dealing with these issues during the design phase not only considerably reduces dangers but also helps to minimize the labor involved to perform audits after application development. Including security concerns into the initial design process enables businesses to build a team with a culture of security awareness that benefits all stages of software development [22].
By following safe coding standards and supporting a culture stressing best practices, developers can reduce the likelihood of security issues during the development process. Comprehensive training courses covering safe coding techniques including effective handling of errors, comprehensive input validation, and effective authentication will teach engineers about responsible coding practices. Establishing security-oriented coding standards would help development teams regularly solve problems all through the coding process. Including automated security tools and code review techniques also helps teams find such problems early, before the code is put into use. Organizations enable developers to give security top importance by encouraging a culture of security consciousness and responsibility. This proactive strategy supports the creation of more resilient and safe applications. Encouragement of a security-centric atmosphere guarantees that security best practices are ingrained in every stage of the development life, therefore drastically lowering the chance of security breaches [23].
Minimizing vulnerabilities in implemented applications depends on including security into the CI/CD pipeline. Including security safeguards at every level helps businesses actively identify and manage potential hazards from first creation of code until deployment, therefore preventing significant consequences. This approach helps to find vulnerabilities in code as it is written by means of automated safety testing - static and dynamic analysis. Frequent security audits and feedback loops also enable teams to always enhance their security practices. By ensuring security is a basic component all through the construction process, organizations may greatly lower risks while improving the entire safety posture with their applications before they impact production environments [24].
Maintaining compliance to both internal organizational standards and legal criteria requires adding security to the CI/CD process. Automated inspections of compliance all throughout the pipeline enable businesses to monitor their infrastructure and applications for conformity to approved security criteria. Being proactive helps one lower the likelihood of non-compliance fees, which may seriously damage reputation and finances. Moreover, it promotes responsibility and governance across the development of operational teams. Encouragement of openness and teamwork helps companies create a more compliant safe workplace, therefore strengthening their total security posture [25].
Strong security practices applied throughout the CI/CD pipeline are essential for building confidence or dependability among users, clients, and stakeholders. Companies that consistently show a commitment to security by way of well-defined rules considerably enhance their market reputation. This commitment towards security ensures stakeholders that the business first gives priority to the protection of sensitive data. Clients hope for the company's ability to stop operational interruptions and data leakage when they witness proactive security measures in place. This confidence not only raises consumer loyalty but also attracts potential clients [26].
Including safety within the CI/CD design promotes a continuous evolution in security policy. As they actively find flaws and review security incidents, development teams get a lot of knowledge that impacts their attitude to risk management. By means of this iterative process, teams can enhance tools, reinforce their security systems, and establish standards depending on actual experience. Companies can build an ecosystem whereby learnt knowledge is distributed and used to increase the flexibility of their products against changing risk. This proactive strategy over time builds a more strong security posture that helps teams to properly protect their assets and shift with times to meet new demands [27].
Identifying Security Risks in the CI/CD Pipeline Understanding security concerns in the CI/CD pipeline allows one to maintain dependability and integrity for activities in the field of software development. Acting as a blend of Continuous Integration or Continuous Development, CI/CD automates software production, therefore allowing developers to frequently and consistently provide code updates. On the other hand, if not properly regulated, this automation could expose different security flaws. One of the main risks is code repositories. Among the vulnerable coding techniques these repositories could be prone to, improper authentication and input validation, therefore creating vulnerabilities like SQL injection and cross-site scripting (XSS). Relying on external libraries increases risk because outdated or poorly maintained source code can contain known vulnerabilities that attackers might exploit. Frequent code repository checks will help to find and resolve these problems, therefore guaranteeing the safe coding standards.

Figure 2: Security for all Stages of a CI/CD Pipeline [28].
Deployment stages are overlooked or carried out wrongly. Security methods should be included into automated systems to identify harmful code and vulnerabilities before they are used.
Inadequate security allows undetectable defects into the production line, may lead to major consequences including data leaks or system breakdowns [29,30]. Moreover, the use of obsolete or inadequate security testing techniques can impede threat detection, hence allowing the deployment of compromised or defective programs. Every CI/CD level of thorough security inspection must be done if we wish to sufficiently reduce these risks. Moreover, configuration control decides whether the CI/CD pipeline has secured stages. Two situations that might expose readily available vulnerabilities are unsecured server setups or incorrect privileges. For example, too liberal access limits can reveal sensitive information or provide illegal access to important systems [31]. Through constant configuration audits and safe setting implementation, one can help to lower these risks and guarantee that surroundings remain secure all during the development life. Containers might bring new issues even if they have benefits like scalability and isolation. For example, incorrect defaults or set container images can expose likely defects [32]. By regularly scanning for vulnerabilities using reliable base images and implementing runtime security measures to monitor unusual activities, companies prioritize the security of their container images [33]. Apart from these technical challenges, organizational culture mostly determines identification and elimination of security vulnerabilities in the CI/CD system. Rooted in a security-first perspective, encouragement of cooperation and communication should help operations, security teams, plus success all around. Including security criteria into the CI/CD flow helps businesses to guarantee that security is not only a fundamental component from the development process but also not a secondary problem [21,31,32]. This method not only points up early hazards but also encourages a responsible culture in the development team. If the development team of companies are to remain current on the most recent security concerns and best practices, they must be continuously educated on security best practices. Security awareness initiatives, seminars, and regular training courses enable teams to spot prospective hazards and implement reasonable defenses. Giving security top focus all through the CI/CD process would help companies greatly lower their attack surface and improve the general safety posture for their software development systems [33].
Financial Services Organization
By including automated safety testing into its CI/CD process, a large financial services company greatly improved its security posture to satisfy strict regulatory standards. Early phases in development life vulnerabilities were found by the company applying either dynamic or statice application security testing techniques. By reducing the average time needed to handle problems, this proactive strategy permitted faster deployment without compromising security. The company therefore not only streamlined its expansion process but also enhanced its regulatory compliance, so ensuring a robust security basis for its usage [34].
An e-commerce platform, security issues in its online apps caused great challenges that compromised not only the business but also its customers. To address these problems, the platform built a comprehensive security plan involving Software Composition Analysis (SCA) and automated compliance checks.
The corporation uncovered flaws in external libraries using SCA and promptly addressed them. This proactive approach enhanced consumer trust in the platform's commitment to safeguard private data in addition to its general security posture. User activity in the e-commerce platform therefore increased noticeably, reflecting the positive impact of robust security measures on customer confidence and loyalty[35,36].
Aware of the pressing need to address data privacy and compliance concerns, a healthcare provider decided to apply DevSecOps approach to enhance its security systems.
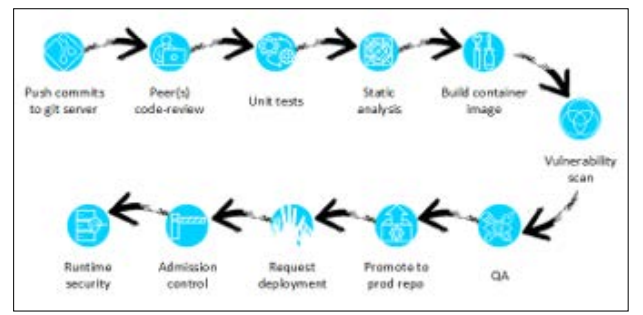
Figure 3: Modern CI/CD workflow [37].
Including security tools right into its Continuous Integration/ Continuous Development (CI/CD) process, the company made sure every code modification passed extensive security testing.
Early in the building process, this proactive approach helped them to find and fix anticipated problems and ensured compliance with Health Insurance Protection & Accountability Act (HIPAA) rules. This not only lowered the possibility of data leaks but also improved their whole security system, thereby improving their power to safeguard patient data [38].
In essence, one must first uncover security concerns in the CI/CD pipeline if we want to safeguard the development of software processes against an ever more complicated threat environment. When businesses embrace agile techniques and embrace automation, the likelihood of vulnerabilities appearing at various stages of development cycle becomes evident. From code development and repository management to development and deployment methods, this stresses the significance of implementing security measures at every level of the CI/CD process. Regular audits and automated security testing technologies help companies to aggressively find and fix vulnerabilities before they find their way into production. Since misconfigurations can result in exploitable vulnerabilities, configuration management and the security of containerized systems must get special attention. Encouragement of a security-first culture in development and operations teams improves cooperation and responsibility, therefore guaranteeing that security is a shared duty rather than a side effect. Awareness campaigns and ongoing education enable team members to remain current with changing risks and best practices, therefore promoting an environment where security takes the front stage. Along with lowering data breach and system failure risk, a complete approach to security in the CI/CD pipeline strengthens customer confidence in software solutions. Organizations can improve their resilience against attacks and fulfil their objectives of fast, dependable software delivery by giving security top priority as a natural component of the development process. Emphasizing security throughout the CI/CD pipeline is a critical investment that safeguards both the organization's assets and its reputation in a competitive marketplace.
