Author(s): Joseph Aaron Tsapa
Today, with more businesses moving their software infrastructure to the cloud, the security and resilience of such systems take priority. The current whitepaper discusses architectural best practices in building secure, reliable software infrastructure within the Amazon Web Services (AWS) cloud environment. It investigates microservices, containerization, data encryption, and disaster recovery and how these practices affect risk reporting. The strategies outlined in the paper will be crucial in empowering organizations to build resilience within their cloud-based software infrastructure. This will be a fundamental component in enabling them to withstand their challenges
One of the strategic imperatives to organizations in the present world has been the migration of software infrastructures to cloud platforms like Amazon Web Services (AWS). Indeed, the cloud platform offers a scalable and flexible environment with a relatively low cost but still ensures its own security and resiliency issues. In order to fully capitalize on the advantages of cloud computing while mitigating potential risks, it is essential to implement architectural approaches aligned with industry best practices. This will ensure that your software infrastructure remains secure and reliable. This white paper addresses the aspects and approaches required to develop resilient systems within the AWS Cloud.
As companies move their software systems to AWS Cloud, they
encounter many difficulties ensuring they are secure and can
recover from problems. These difficulties involve:
• Protecting against cyber threats and unauthorized access
• Maintaining the availability and reliability of services
• Ensuring data confidentiality and integrity
• Recovering from disasters and minimizing downtime
• Addressing these challenges requires a well-architected
approach incorporating best practices across various domains.
When you make software in the cloud, using a microservices design is very important to make it strong. By breaking extensive programs into smaller parts that work separately, companies can grow more efficiently and handle problems better [1]. Every microservice can be created and put into use, and its scale can be adjusted on its own, which gives you more detailed management of the whole setup. AWS offers tools such as Amazon Elastic Container Service (ECS) and AWS Lambda that help build systems based on microservices.
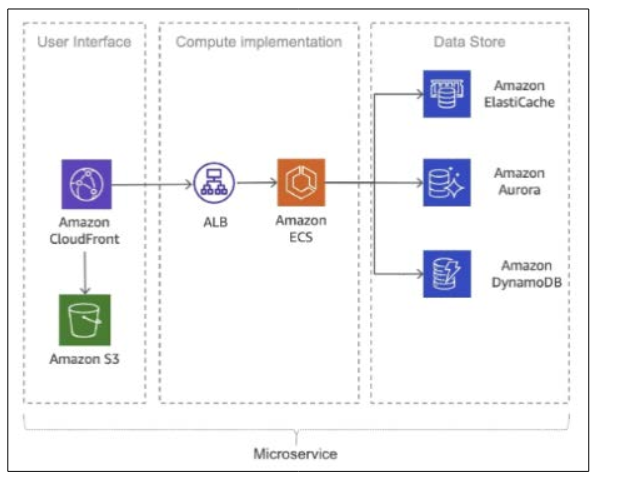
Figure 1: Example of a Microservices Architecture on AWS
Containerization is vital in supporting microservices and is essential for creating robust software systems. Containers offer a streamlined and movable execution setting, which lets programs be bundled with all they need to run and installed uniformly in various settings [2]. AWS provides services like Amazon Elastic Kubernetes Service (EKS) and AWS Fargate to make coordinating and handling containers easier for users.
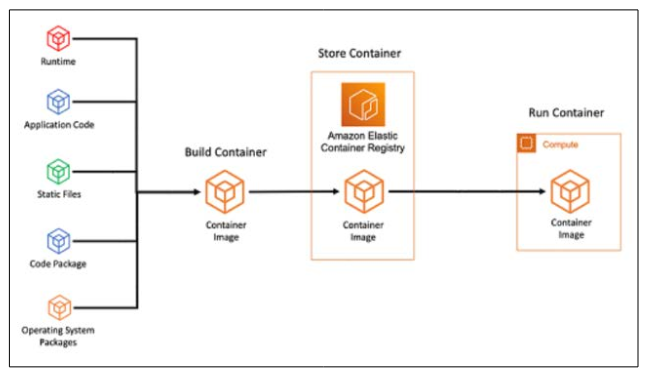
Figure 2: Containerization Workflow using AWS Services
Segmenting the network adequately is very important to keep cloud software infrastructure safe. By dividing resources logically according to their need for protection, companies can ensure that any security problems affect only a tiny area and minimize the chance of attacks. AWS offers a Virtual Private Cloud, or VPC, that allows you to set up separate network spaces and security groups that manage incoming and outgoing traffic for each instance.
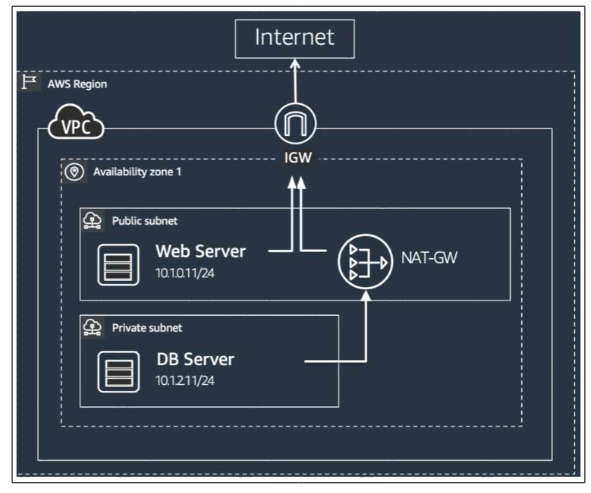
Figure 3: Network Segmentation using VPC and Security Groups
Protecting critical information in the cloud is very important, so data must be encrypted when it is stored and also when it is being sent [3]. AWS offers many encryption options, such as encryption on the server side for Amazon S3 and Amazon EBS and on the client side with AWS Key Management Service (KMS). Encrypting data helps maintain confidentiality and integrity, even if the underlying infrastructure is compromised.
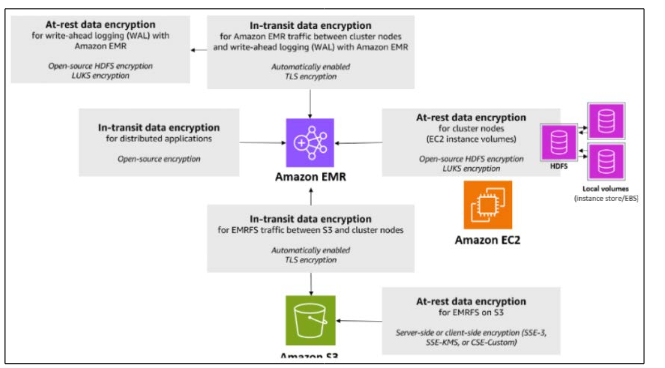
Figure 4: Data Encryption Options in AWS
A strong disaster recovery strategy is essential to keeping the business running when problems occur. AWS offers tools such as Amazon S3 to back up data and Amazon RDS to copy databases in different areas (Amazon et al.). Organizations can reduce the time systems are down and protect against losing data during a disaster by using deployments across different regions and making failover happen automatically.
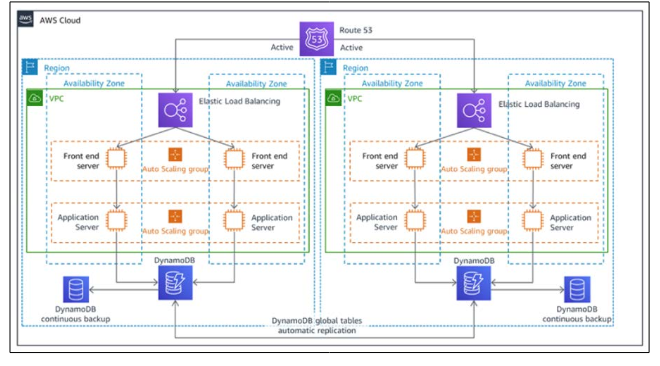
Figure 5: Disaster Recovery Architecture Spanning Multiple AWS Regions
Using the suitable methods for building architecture that this text
discusses can make a big difference in how safe and robust our
computer systems in AWS Cloud are Amazon, et al [4]. When
companies take advantage of small, separate services, using
containers for software parts, splitting up networks into sections,
making data secret with encryption, and planning for emergencies
when things go wrong - they can:
• Improve the scalability and agility of their systems
• Decrease the number of vulnerable points and minimize the
consequences of possible security incidents.
• Safeguard the confidentiality and maintain the integrity of
sensitive data.
• Minimize downtime and data loss during disasters
• Enhance risk reporting by demonstrating adherence to best
practices
These advantages lead to greater customer trust, improved adherence to rules and regulations, and an advantage over market competitors.
This paper describes suitable methods for many software systems in the AWS Cloud. If a company is creating a new system or moving an old one to the cloud, they can change these ideas to fit their needs. The range of applying it can change depending on how big and complicated the system is, how sensitive the data is, and what kind of rules there are.
We need to use many methods to strengthen the software infrastructure and recover in AWS Cloud. This includes breaking down the system into microservices, using containers, dividing the network into parts, ensuring data is encoded, and planning emergencies. When companies follow these essential steps well, they can make their cloud systems much safer and more dependable and get better at telling about possible risks. Organizations need to keep up with new trends because the cloud keeps changing, and they should continuously improve their architecture strategies to stay competitive in the digital world [5].
